Lock, unlocking method thereof, lock administrative center and control method thereof
A management center and lock technology, applied in the field of locks, can solve problems such as inconvenience and safety hazards, and achieve the effects of enhancing security, enhancing confidentiality, and safe and reliable control methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
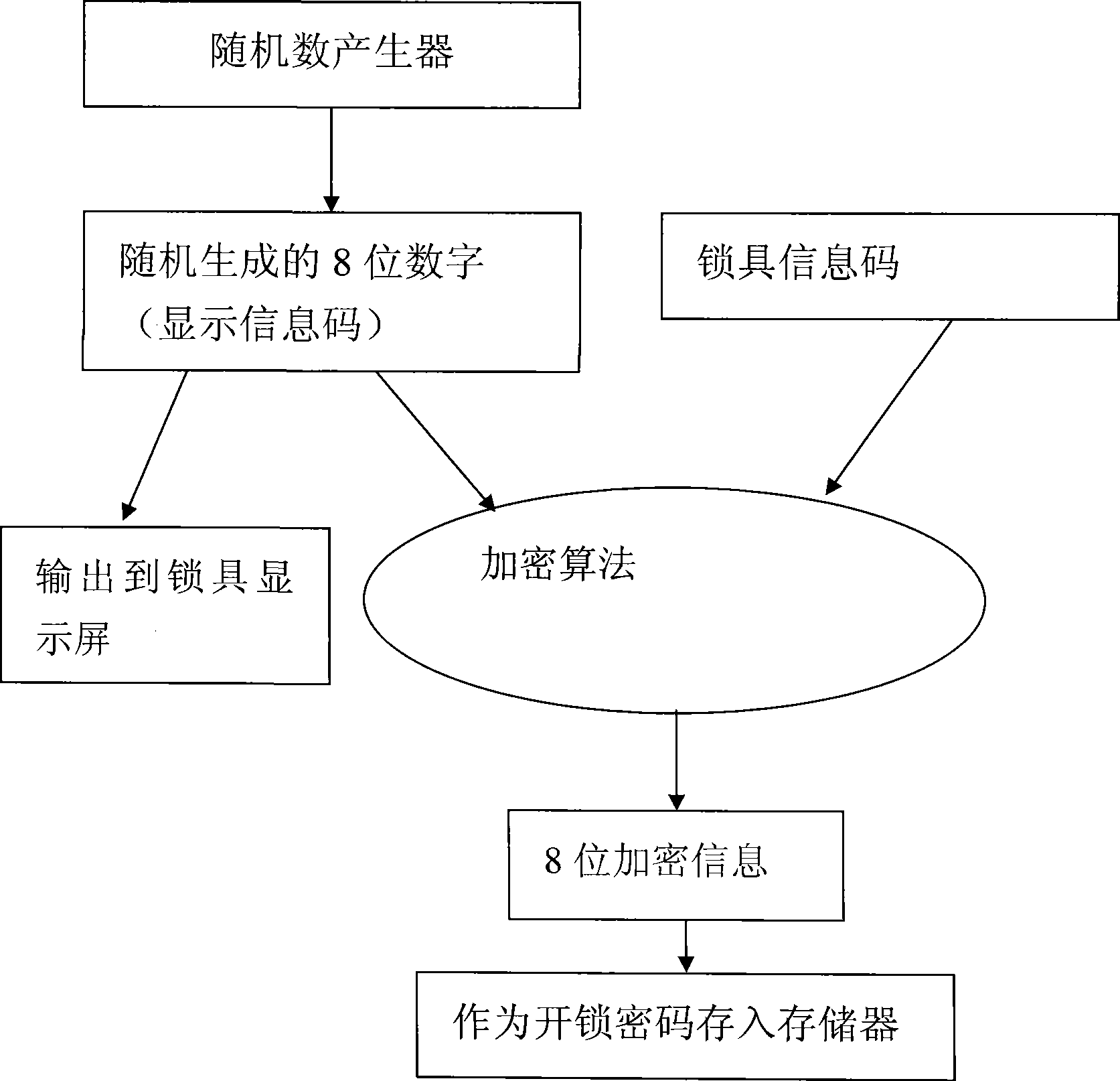
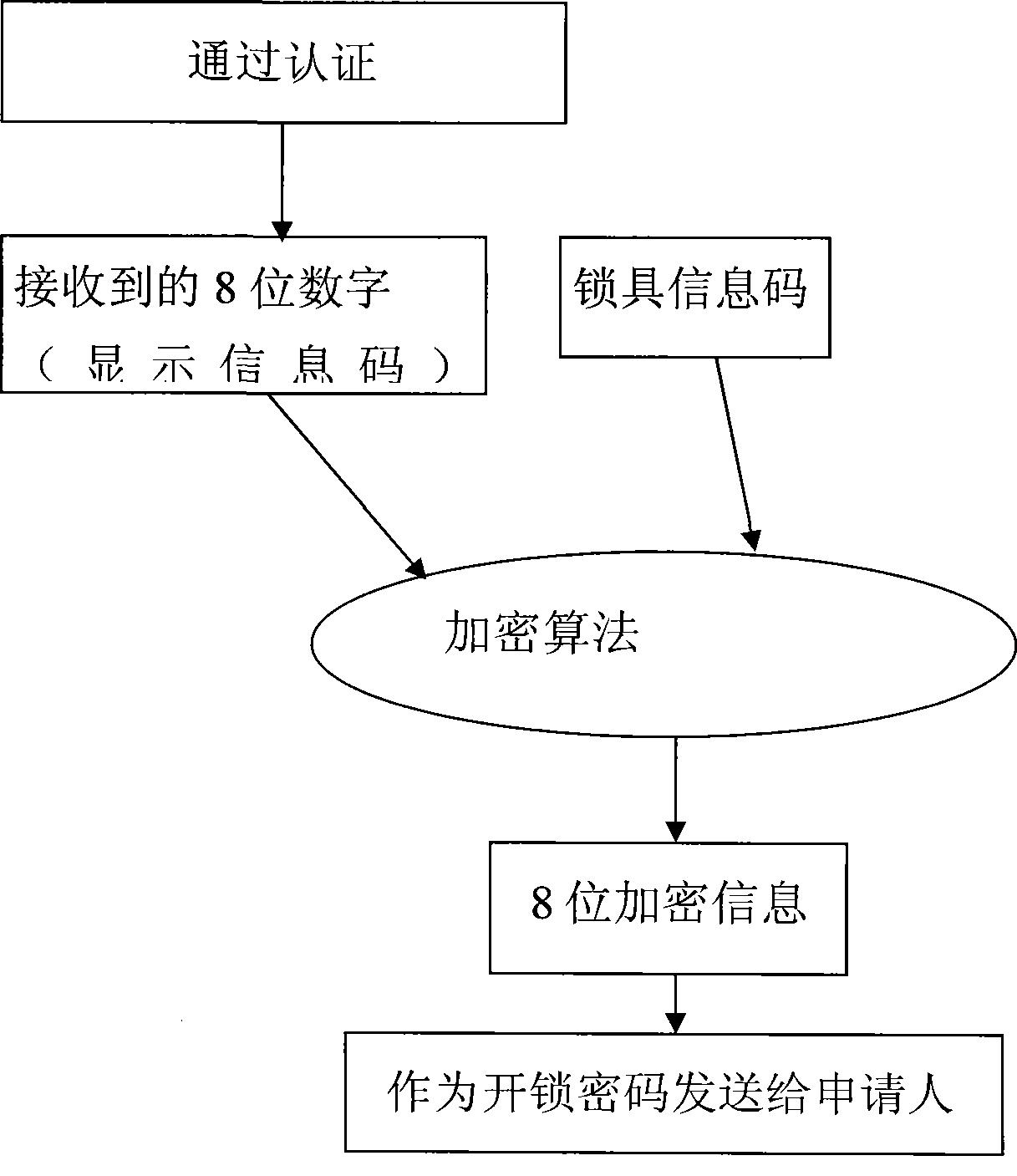
[0026] Such as figure 1 , 2 As shown, a method for unlocking a lock includes the following steps:
[0027] Step 1: Register the lock information code and user identity information code in the lock management center. The registration can be carried out after the lock is sold. The lock information code may be a lock serial number, which is used to distinguish different locks. The user identity information code includes a user code and a control code. The user code is used to distinguish different users, and the user code may be the user name of the lock management center webpage or the user's mobile phone number. The control code is used to confirm the identity of the user. When the user code and the control code received by the lock management center are correct, it indicates that the authentication is passed.
[0028] The user can choose one of the following authentication methods and register in the lock management center:
[0029] Single-person authentication: There is only one...
specific Embodiment approach 2
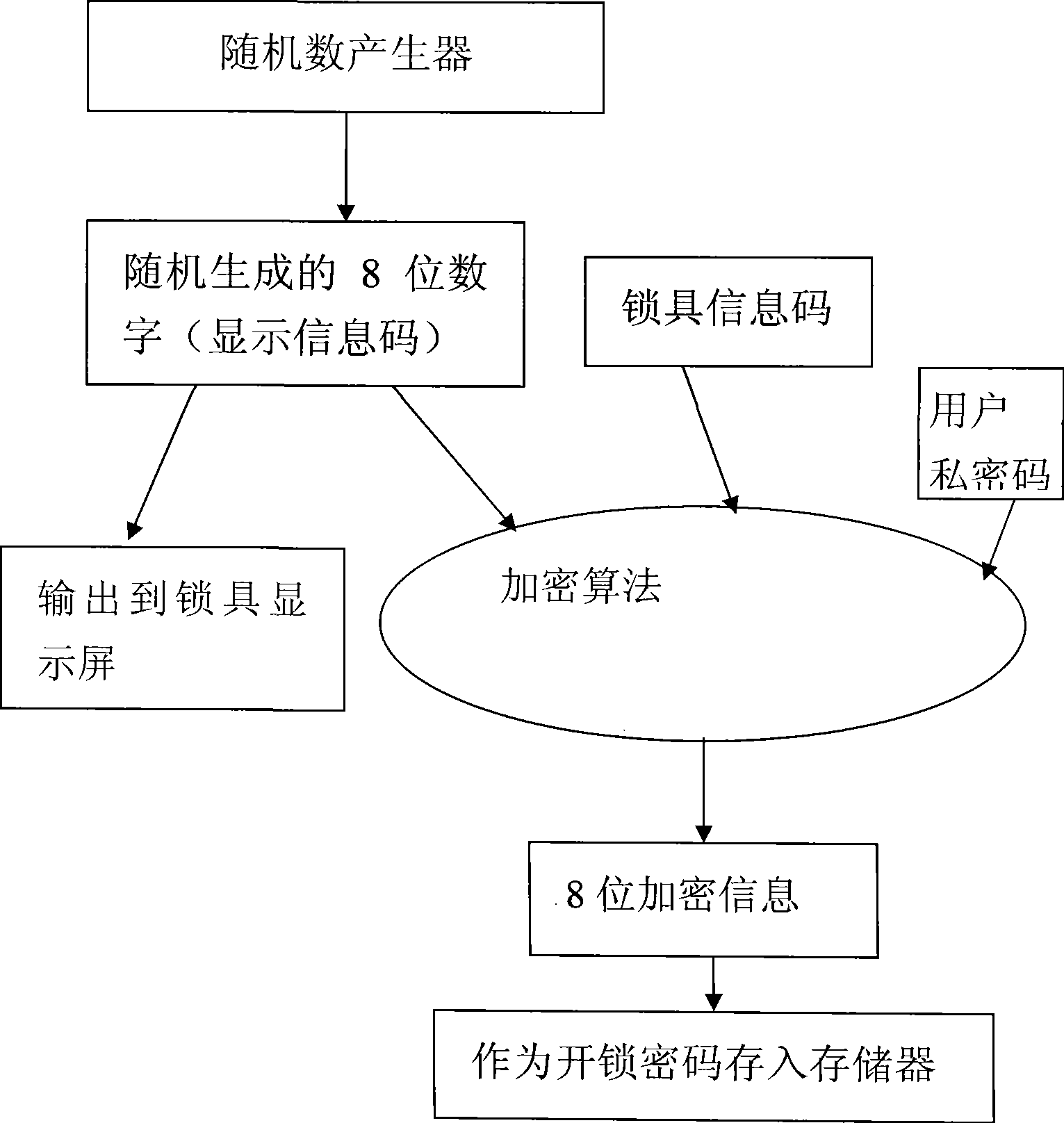
[0042] Such as image 3 , 4 As shown, the difference between this embodiment and the first embodiment is that the user's private code is stored in the lock, and the user's private code is registered in the lock management center. The user's private password also participates in the encryption calculation. The user's private password cannot be obtained by others, so even if the encryption algorithm is deciphered, he cannot calculate the unlock password. The similarities between this specific embodiment and specific embodiment 1 will not be repeated, and the differences between the lock unlocking method of this specific embodiment and specific embodiment 1 will be described in further detail below:
[0043] A method for unlocking a lock includes the following steps:
[0044] The first step: register the lock information code, the user's private code and the user's identity information code in the lock management center, and store the user's private code in the lock. The user's priva...
specific Embodiment approach 3
[0048] This specific embodiment corresponds to the first specific embodiment. Such as Figure 5 As shown, a lock includes an unlocking mechanism, a keyboard, a display, and a built-in processor. The built-in processor includes an input module, an output module, a control module, a display code generation module, and an encryption module. The control module has a built-in storage module. The keyboard is coupled with the input module, the control module is respectively coupled with the input module, the unlocking mechanism, and the display code generation module, the storage module is coupled with the encryption module, and the output module is coupled between the display and the display code generation module. A lock information code is stored in the storage module.
[0049] Every time the lock is locked, the unlocking mechanism will send a locked signal to the control module. When the control module receives the locked signal, it controls the display code generation module to gener...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com