Method realizing public key acquiring, certificater verification and bidirectional identification of entity
A public key certificate and entity technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve problems such as complex protocols, non-compliance, limited user equipment storage resources, etc., to meet authentication requirements and improve efficiency and the effect of the effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
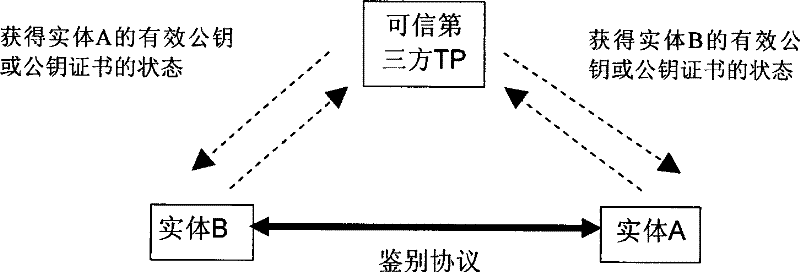
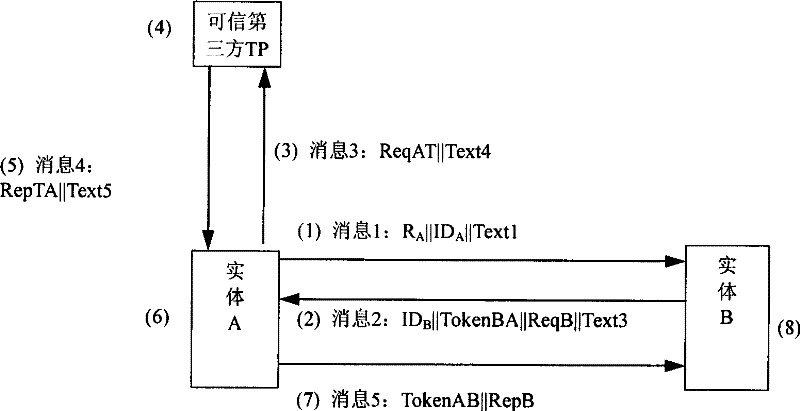
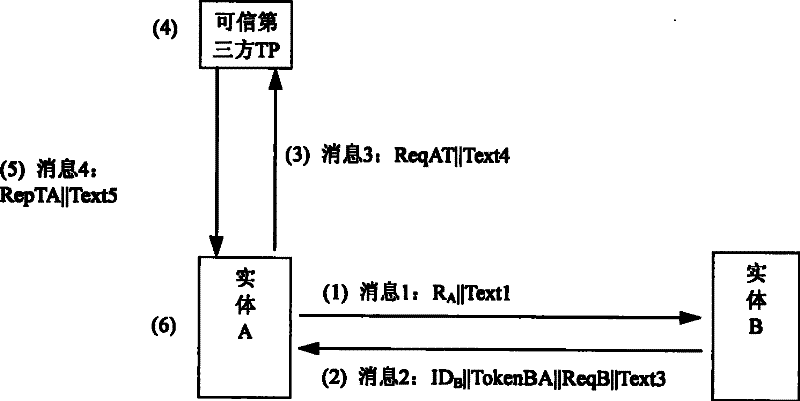
[0039] The method of the present invention involves three security elements, that is, two entities A and B and a trusted third party TP, through the online trusted third party TP, the authentication between entities A and B is completed, and the valid The status of the public key or public key certificate.
[0040] Entity A or B is represented by entity X; then R X Indicates the random number generated by entity X; Cert X is the public key certificate of entity X; ID X Is the identity of entity X, by the certificate Cert X Or the entity's distinguisher X indicates; ReqX indicates the request generated by entity X, requesting information such as the valid public key of the peer entity or the state of the public key certificate; ReqXT indicates the request generated by entity X or forwarded to the trusted third party TP Request; RepX represents the response sent to entity X for ReqX, that is, responds to entity X with the requested entity’s valid public key or the status of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com