Stream cipher generator
A generator and stream cipher technology, applied in the field of information security transmission, which can solve the problems of unsatisfactory key stream test results and insufficient randomness of the key stream.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] In order to better understand the present invention, the present invention will be described in more detail below in conjunction with specific embodiments. It is to be noted that similar components are given similar reference numerals even though they appear in different drawings. In the following description, when a detailed description of known functions and designs employed may obscure the subject matter of the present invention, these descriptions will be omitted here.
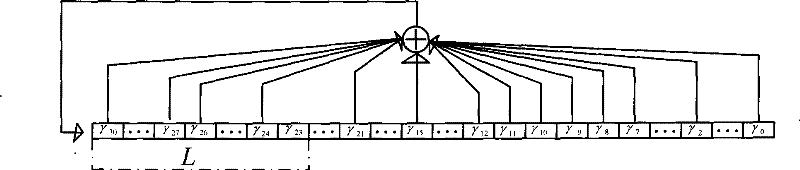
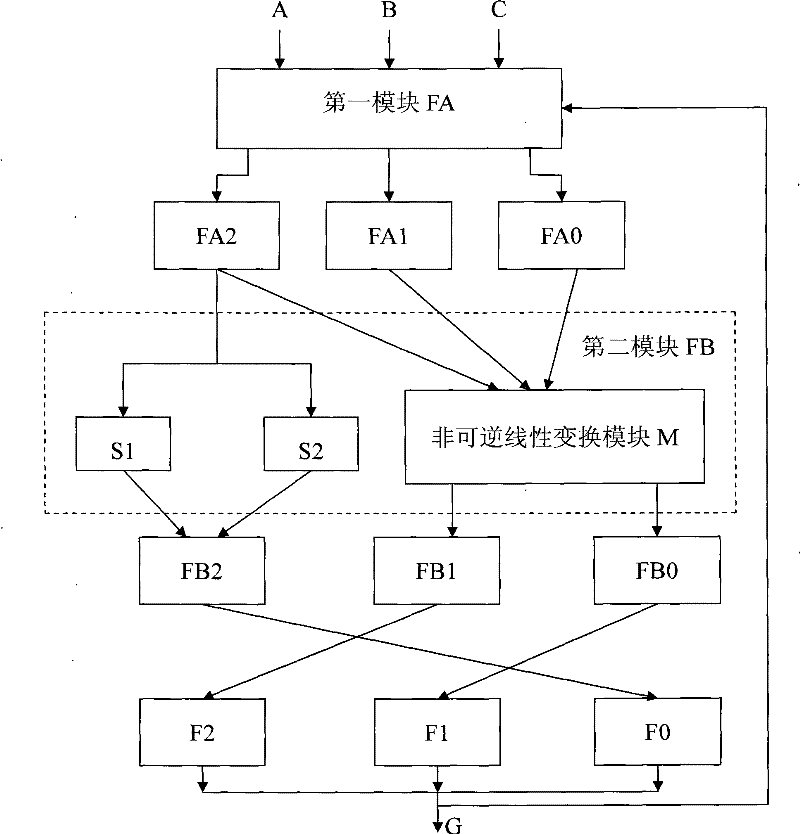
[0028] Fig. 1 is a functional block diagram of a specific embodiment of the stream cipher generator of the present invention. In the figure, the stream cipher generator includes three linear feedback shift registers LFSRα, LFSRβ and LFSRγ, and three linear transformation modules T, K and L, wherein the linear transformation module T performs feedback setting for the key of the linear feedback shift register LFSRα The linear transformation module K scrambles the key of the linear feedback shift regi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com