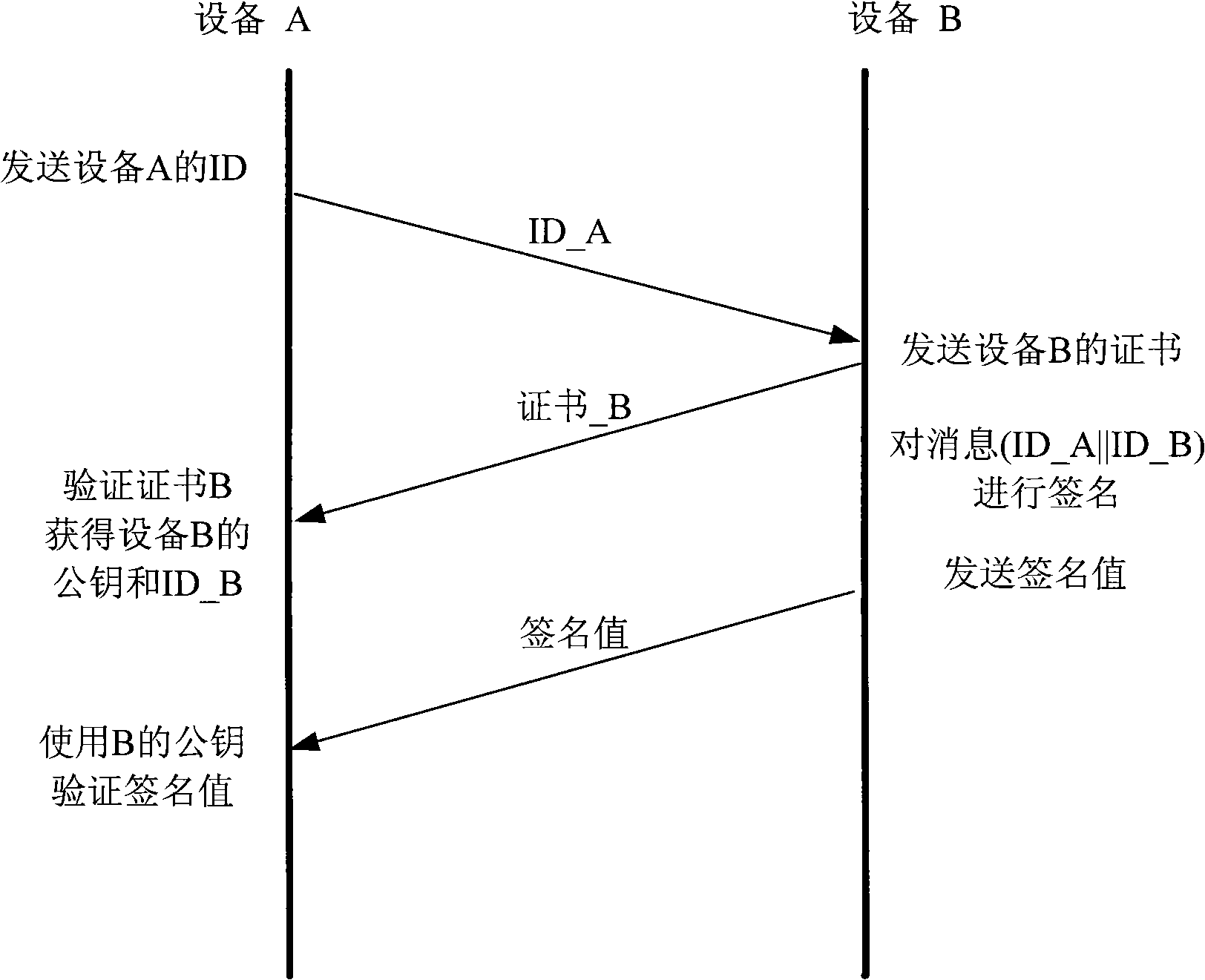
Identity authentication system based on elliptic curve
An identity authentication and elliptic curve technology, applied in the field of identity authentication systems, can solve the problems of inability to guarantee the legality of authentication equipment, complicated two-way authentication, time-consuming and resource-consuming, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] When the specific operation is implemented, all parameters of the algorithm are determined by a trusted third-party authority. Part of the parameters are made public, while the other part of the parameters are strictly kept secret, and the corresponding parameters are set in device A and device B. For simplicity, this embodiment selects the P-192 elliptic curve on the prime number field recommended by NIST and some simple parameters.
[0022] First, the elliptic curve parameters (p, a, b, G, n, h) etc. are selected by the authoritative trust agency:
[0023] The parameters that need to be disclosed are:
[0024] Elliptic curve equation y 2 =x 3 -ax-b
[0025] P=2 192 -2 64 -1
[0026] a=-3(mod p)=p-3=2 192 -2 64 -2 2
[0027] b=0x 64210519 E59C80E7 0FA7E9AB 72243049 FEB8DEEC C146B9B1
[0028] The parameters that need to be kept strictly confidential are:
[0029] G x =0x 188DA80E B03090F6 7CBF20EB 43A18800 F4FF0AFD 82FF1012
[0030] G y =0x 07192B95 FFC8...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com