Full-shield anti-peek anti-code theft blind inputting cipher keyboard
A password keyboard and touch typing technology, applied in the input/output process of data processing, input/output of user/computer interaction, instruments, etc., can solve the problems of weak confidentiality, inconvenient password input, unsafe password input, etc. , to achieve the effect of high confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
[0016] Embodiment 1 In the two-dimensional table of this embodiment, a character that only appears in one character column is called a single character, and the same character column can only have one single character. Therefore, a single character in the two-dimensional table can be The basic input key input corresponding to the column where the character is located; the character that appears at least twice in different columns is called a multiple character, and each character in it is called the sub-character of the multiple character, and the number of sub-characters of different multiple characters can be different, one The combination of the column where the sub-characters of multiple characters are located is called the sub-character combination of the multiple characters. Any two sub-character combinations of multiple characters are different. Therefore, the multiple characters in the two-dimensional table can be formed by clicking the sub-character combination Corresp...
Embodiment 1
[0017] Embodiment 1 Digital touch typing input anti-peep password keyboard
[0018] figure 2 It is a schematic diagram of the keyboard body of this embodiment;
[0019] image 3 It is a schematic diagram of the privacy cover of this embodiment.
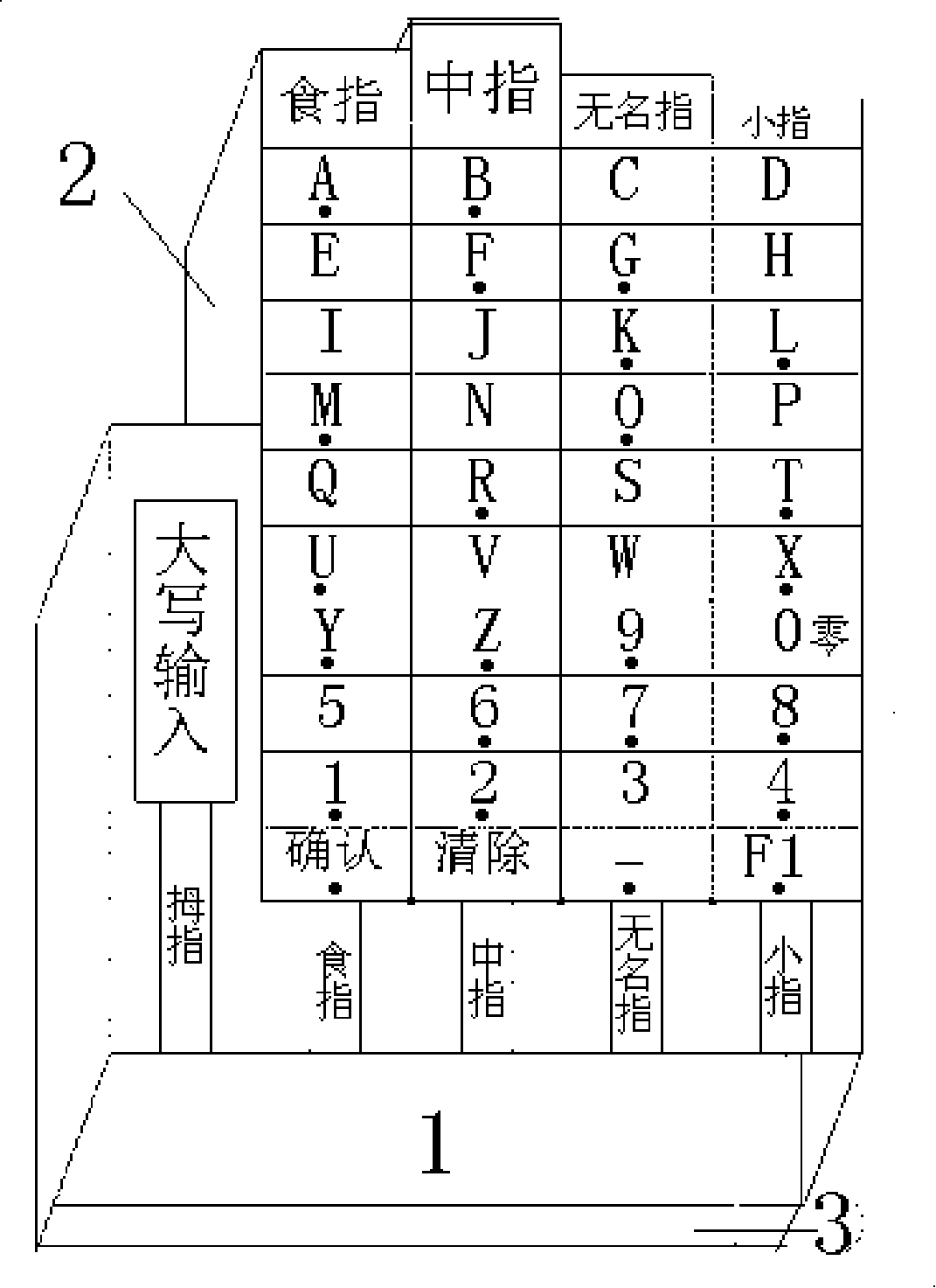
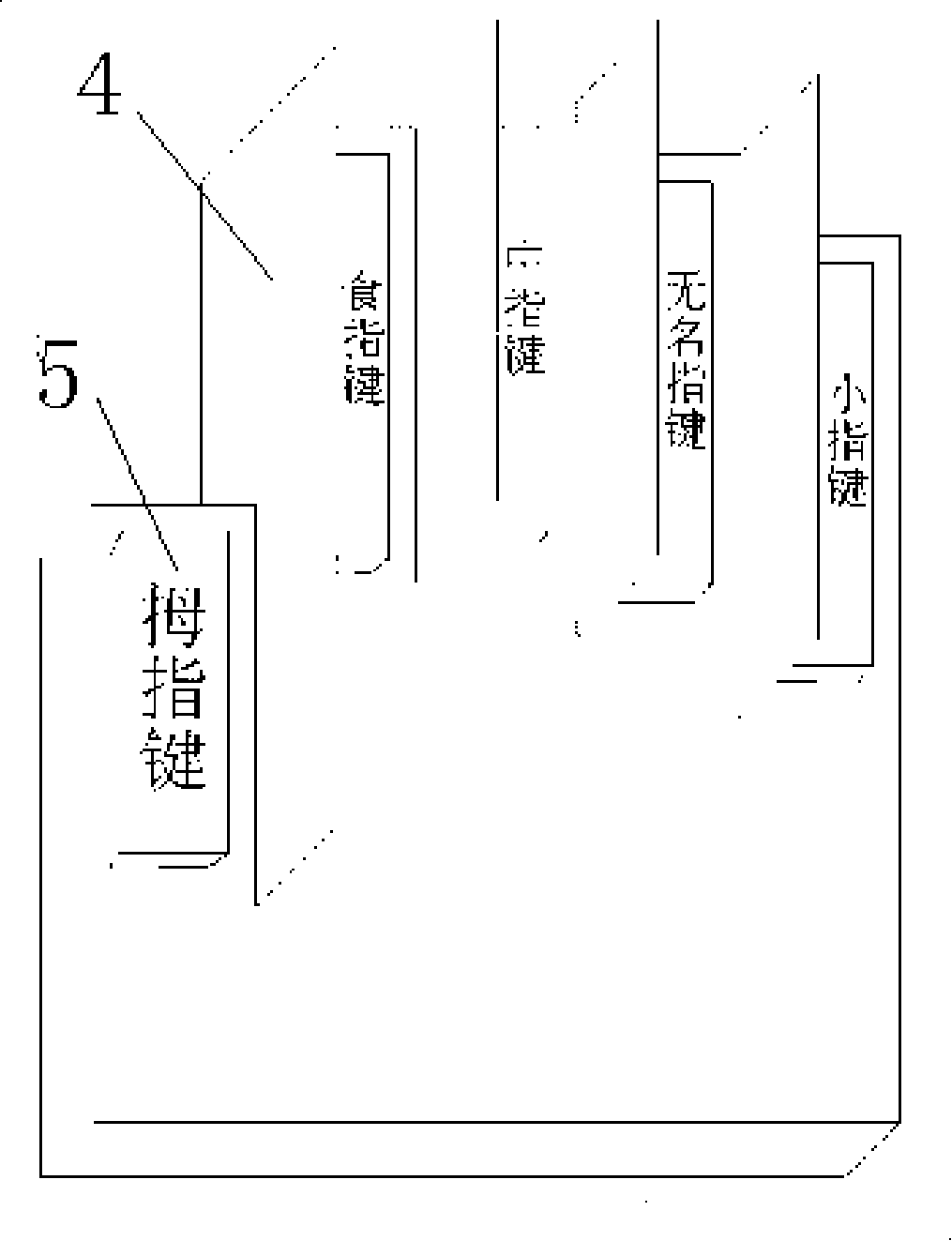
[0020] exist figure 2 On the shown keyboard body, the five strip-shaped basic input keys are separated from each other by the partition plate 4 shown in the figure, so that the five fingers can be positioned accurately on the corresponding basic input keys; Naturally positioned and arranged in a staggered front and back, and the keyboard body and the privacy cover are also designed in the shape of a palm according to the length of the five fingers, so that the inputter can search for characters on the privacy cover more intuitively and quickly.
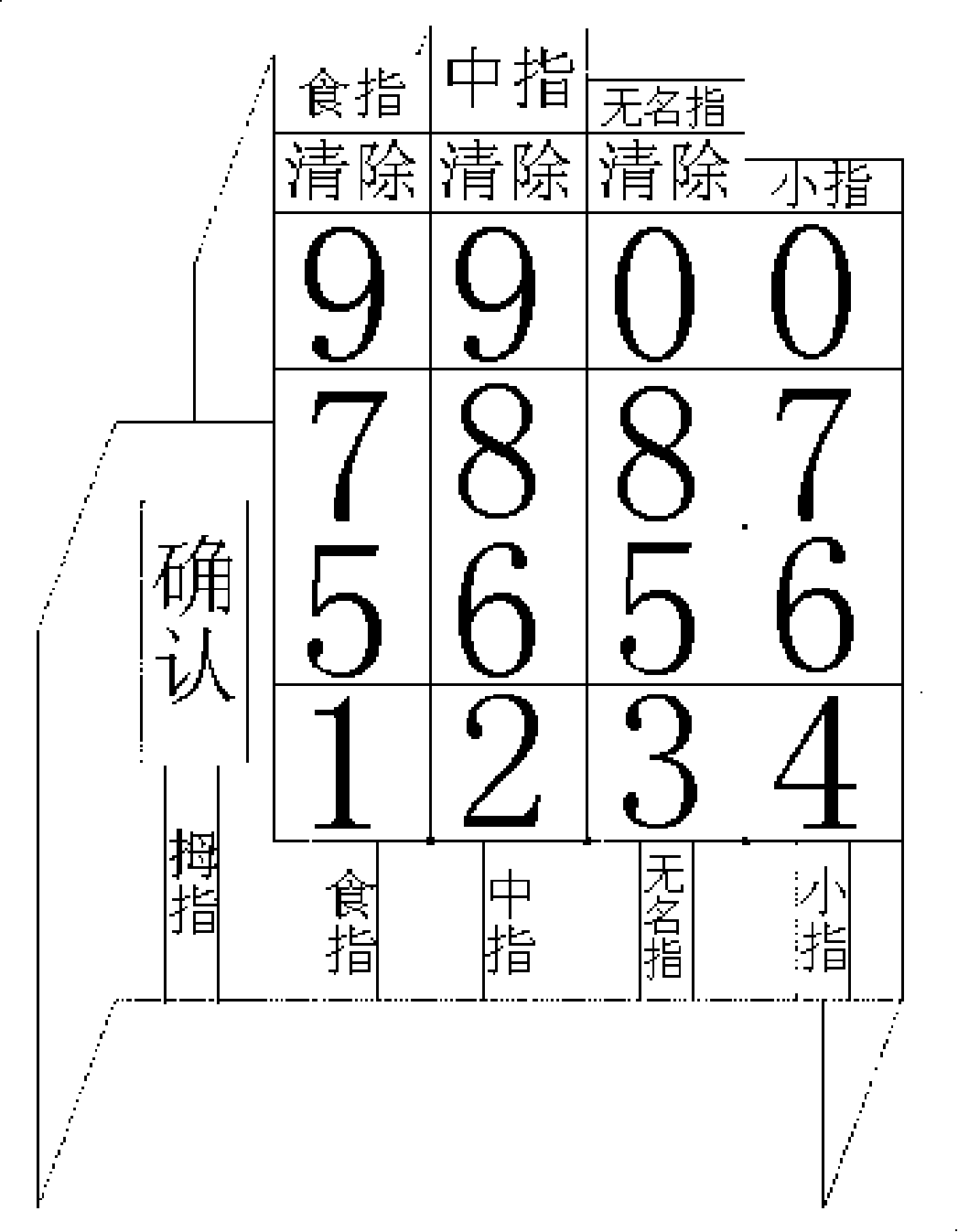
[0021] exist image 3 The upper surface of the anti-peeping cover shown is marked with a virtual key surface composed of ten numbers from 0 to 9 and the characters "confirm" and "clear...
Embodiment approach 2
[0026] Embodiment 2 In this embodiment, the corresponding column of each row of the virtual key surface two-dimensional table is marked with more than one identification symbol 6. The above-mentioned identification symbol refers to the symbol or color located in the corresponding column in a character row. Different rows The number of the above-mentioned identification symbols can be different; the combination of all the identification symbols of a character row in the column is called the identification symbol combination of the row, and the combination of identification symbols of any two different character rows are not the same; there can be one in the same character column Said single character different from the above;
[0027] According to the two-dimensional plane coordinate positioning method, for any character in the two-dimensional table of the virtual key surface, the character can be positioned as long as the column and row where the character is located, so, by fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com