Safety detecting method and system of network data flow
A data flow, network technology, used in network connections, transmission systems, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention will be described in detail below in conjunction with preferred embodiments with reference to the accompanying drawings of the present invention.
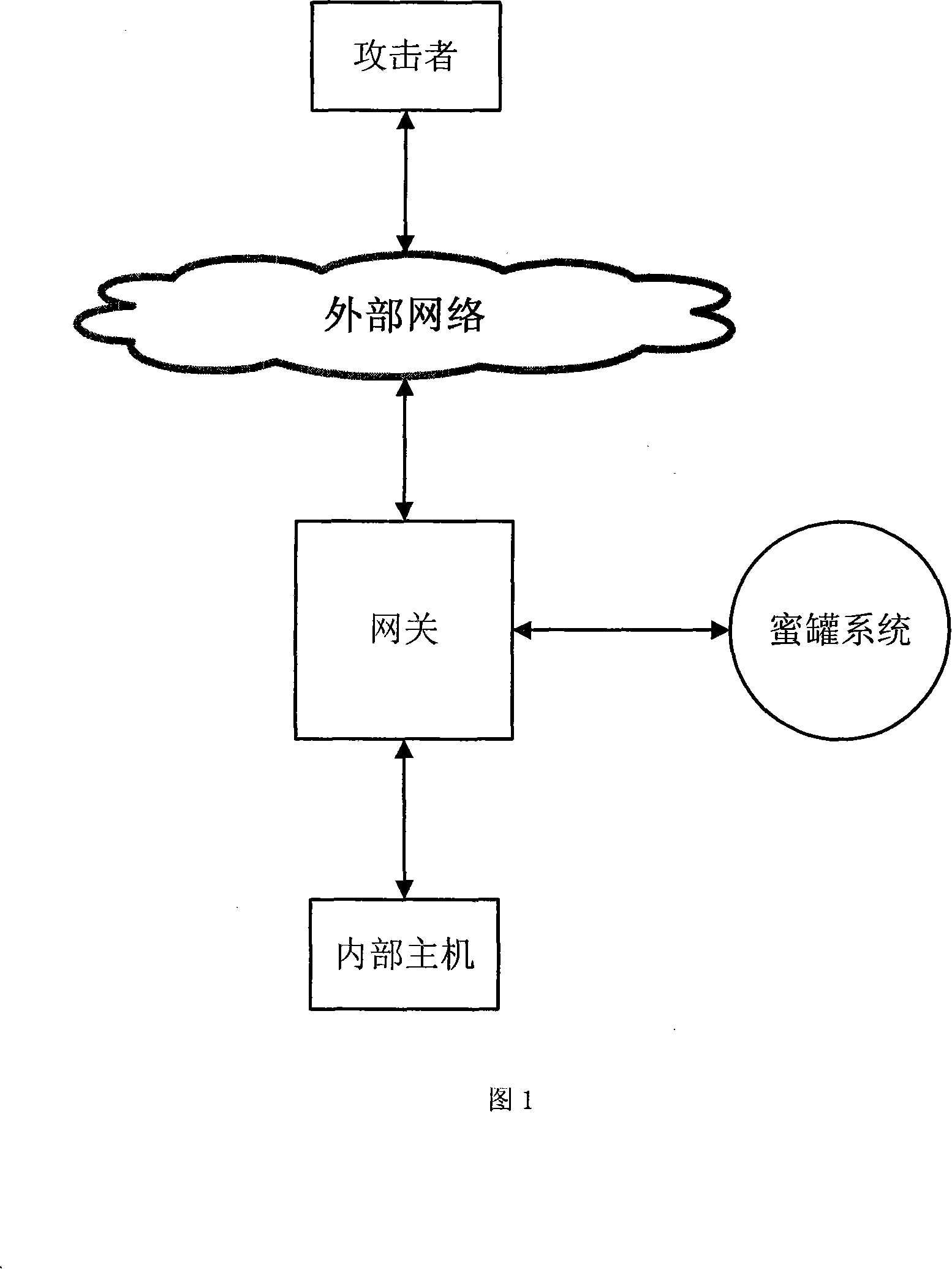
[0044] As shown in Figure 1, it is a schematic diagram of the gateway connecting the external network, the internal network host and the honeypot system. In this implementation, the gateway uses a computer system with three network cards, which are respectively connected to the external network, the internal network host, and the honeypot system.
[0045] As shown in FIG. 2, it represents a flow chart of the method of the present invention.
[0046] (1) The gateway judges that a certain data flow may be dangerous according to the following methods:
[0047] A. The characteristics of a certain data flow conform to the gateway’s dangerous data flow matching rules;
[0048] B. One end of the data flow is on the blacklist, or the data flow accesses restricted internal host resources;
[0049] C. One end ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com