Network safety integrated estimation system
A comprehensive assessment and network security technology, applied in the field of information security, can solve the problems that network security assessment methods and tools cannot give scientific and objective technical judgments
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
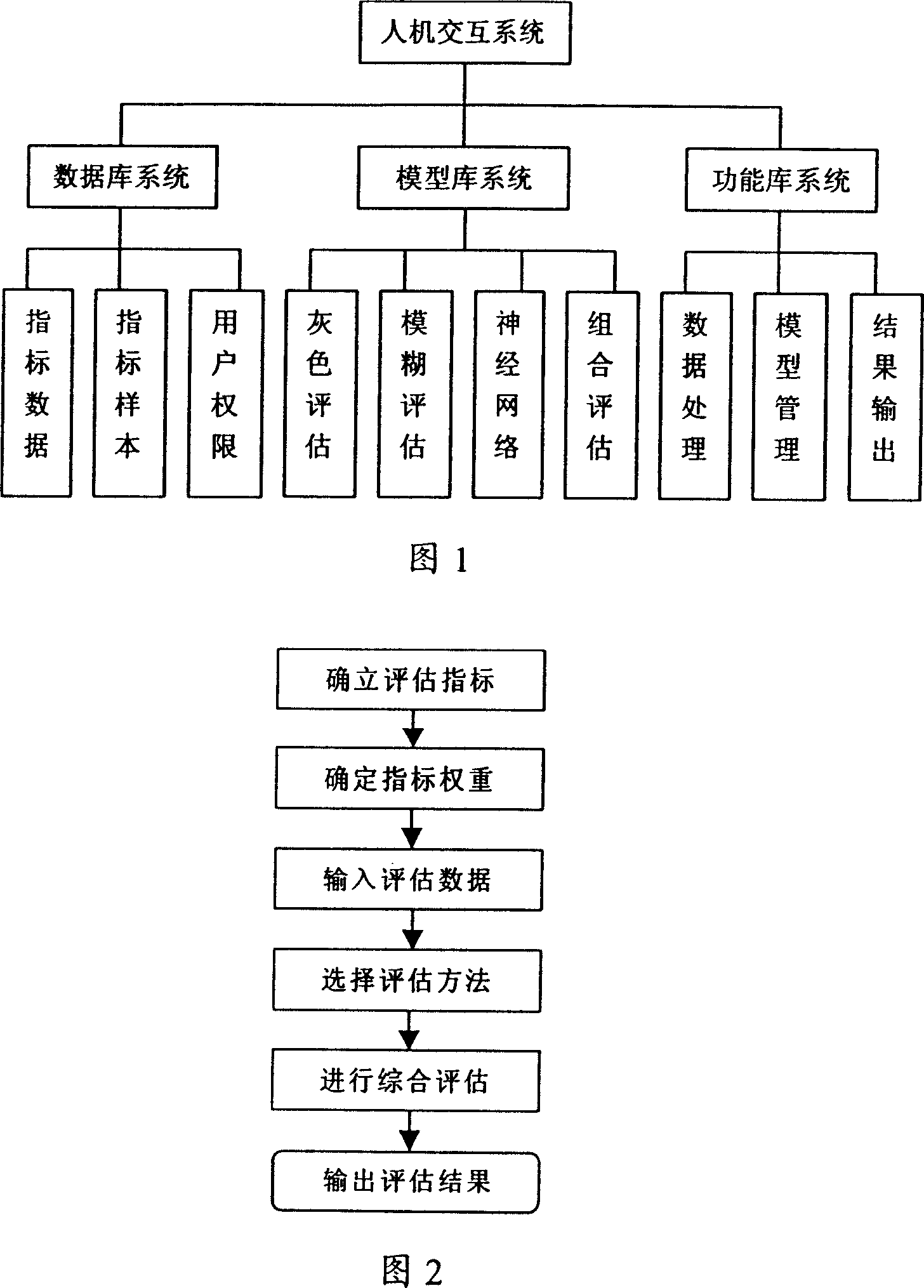
[0029] As shown in Figure 1, a network security comprehensive evaluation system is characterized in that it includes three subsystems: database, model library, and function library. The database system includes an index database, an index sample library, and a user authority library. The index database is used to record Each specific indicator value; the indicator sample library is used to record the standards for evaluating sample values and the names and connotations of each indicator; the user authority library is used to record the user's name and corresponding authority; the model library system includes gray evaluation, fuzzy evaluation, neural network evaluation , combined evaluation four modules; the function library system includes a data processing module, a model management module, and a result output module. The data processing module realizes the calculation process of various indicators under different models; The goal is to formulate corresponding standards and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com