Conversation control method and control device
A control method and legal technology, applied in the field of information security, can solve the problems of aggravated consequences of denial of service attacks, occupation, and the total number of IKE sessions is full, so as to achieve the effect of reduced occupation and guaranteed processing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
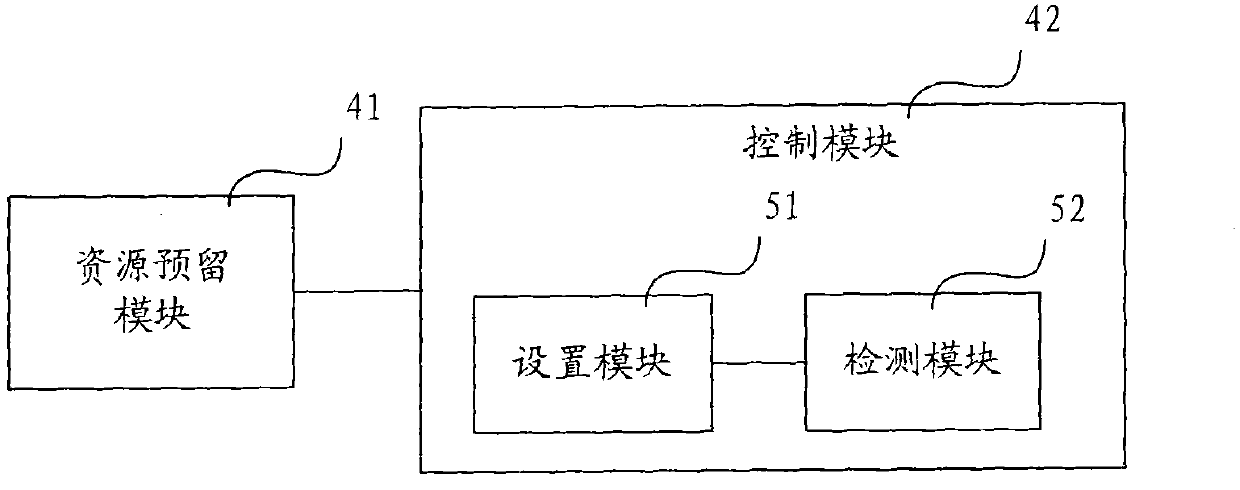
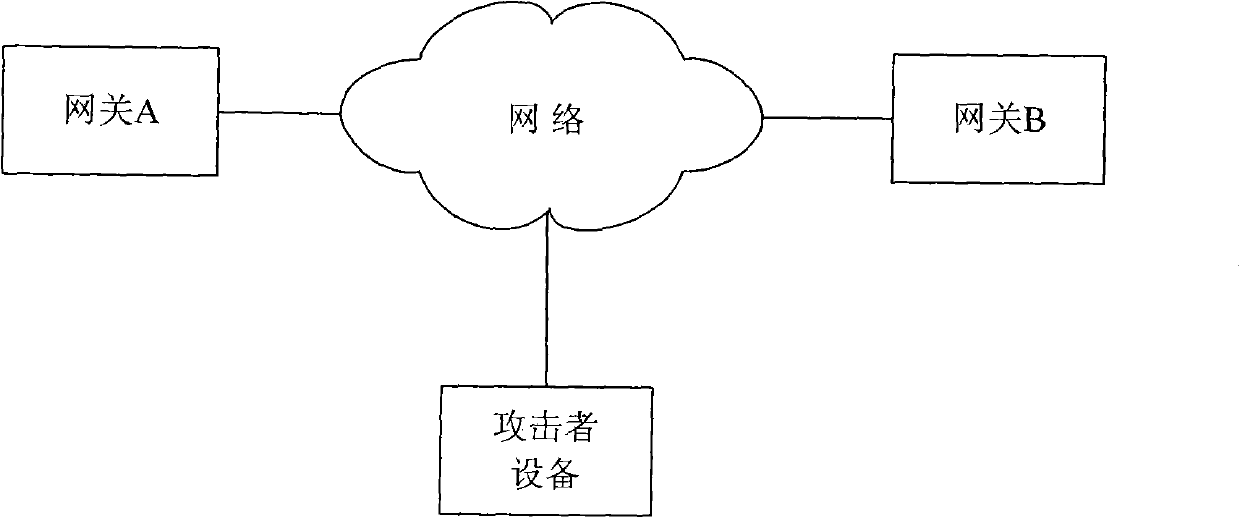
Image
Examples
Embodiment Construction
[0031] The technical solutions of the present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
[0032] In the prior art, the Internet Key Exchange Protocol (IKE for short) adopts the Cookie mechanism, uses the Cookie contained in the IKE message to identify an IKE session, and sets the total number of connections of the IKE session. Although this Cookie mechanism can effectively counter the denial-of-service attack that the attacker tries to exhaust system resources by sending a large number of IKE request messages including fixed Cookie values, it cannot effectively counter the attacker's attack by sending a large number of A denial-of-service attack that exhausts system resources by using IKE request packets with a large value. In addition, in addition to DoS attacks, there are other attacks that may exhaust system resources, causing other IKE negotiation initiators to fail to perform normal IKE negotiations ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com