Method for early alarming by-path attack in safety chip
A security chip, early warning technology, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
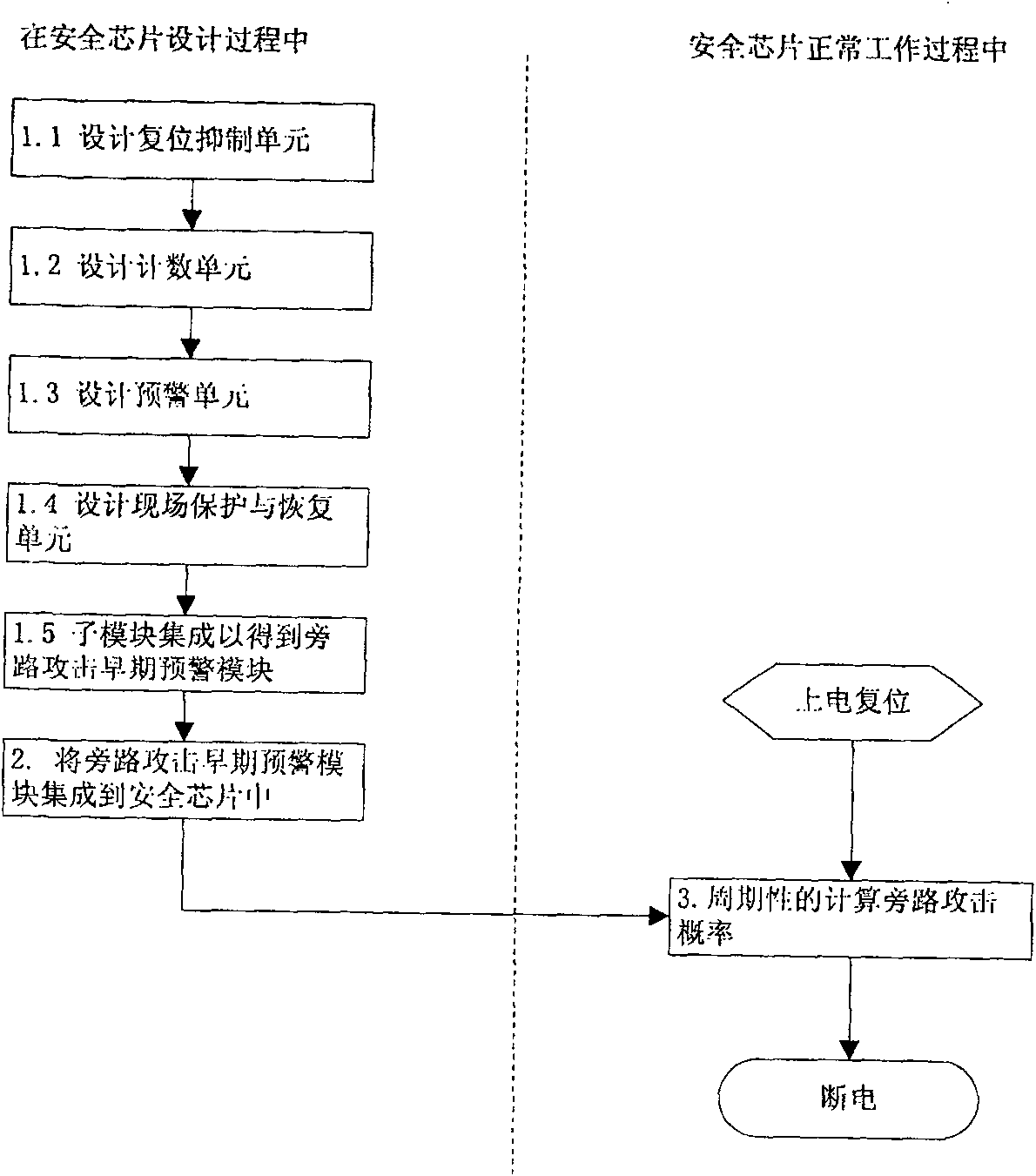
[0087] figure 1 The overall flow chart for early warning of bypass attacks in the security chip mainly includes the following steps:
[0088] 1. Design side channel attack early warning module, the specific design method is:
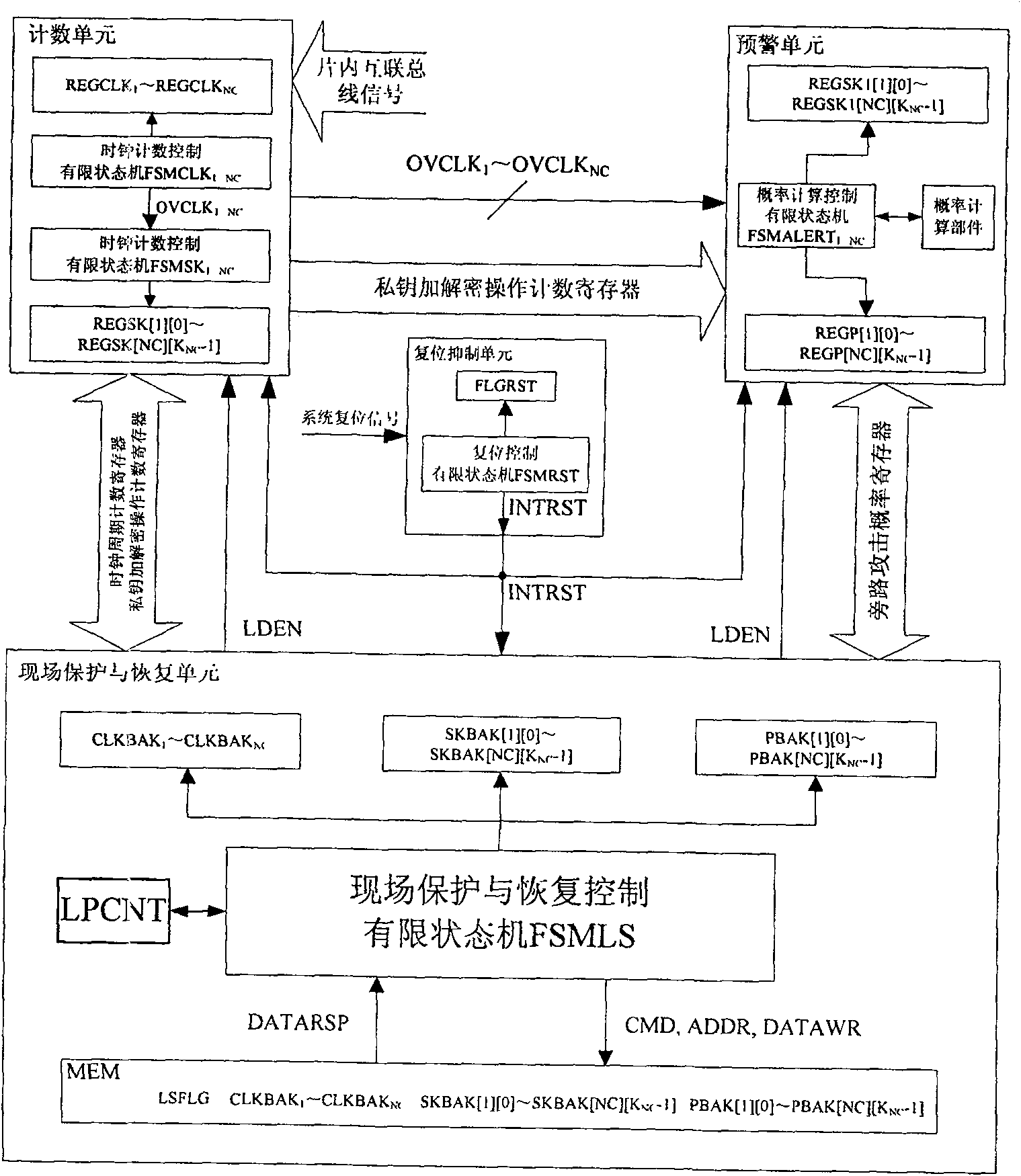
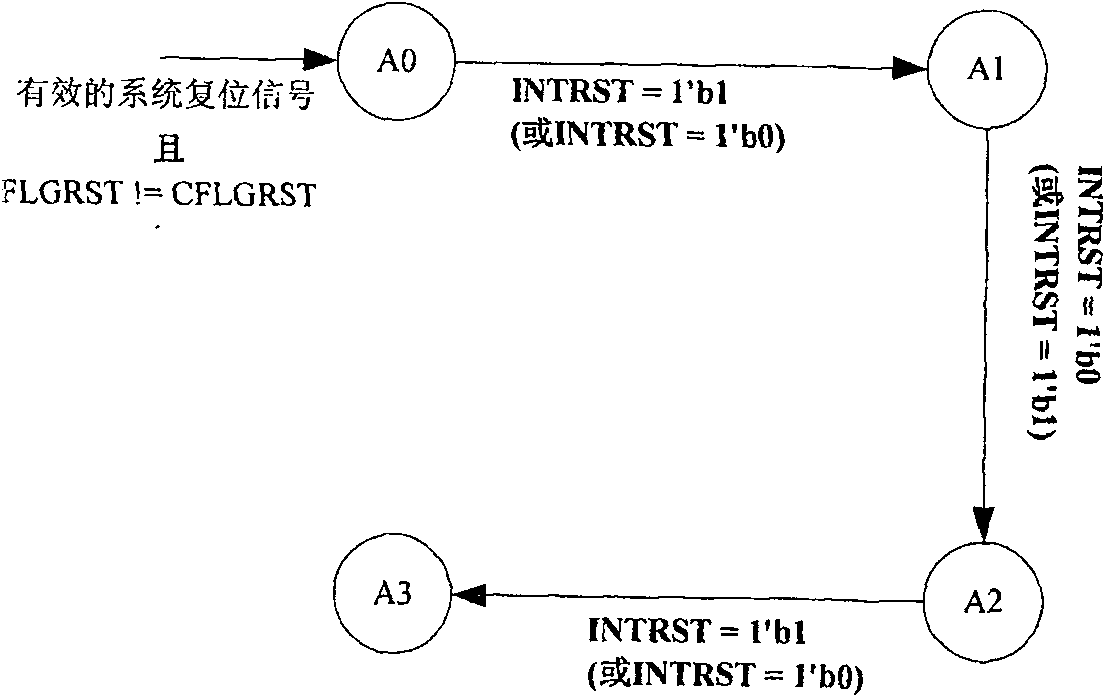
[0089] 1.1 Design the reset suppression unit, which uses the system reset signal as input to generate an internal reset signal for the bypass attack early warning module, and ensures that the security chip is reset only once during the period from power-on to power-off;
[0090] 1.2 Design the counting unit, which takes the interconnection bus signal (including address line, data line and control line) of the security chip as input, that is, monitors the interconnection bus in the chip, and counts the number of private key encryption and decryption operations performed by the security chip within a certain period of time;
[0091] 1.3 Design an early warning unit to determine the current probability of the chip being subjected to a side channel attack a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com