Method, system and application for checking multicast user underling terminal device validity
A technology of terminal equipment and legitimacy, applied in the field of network communication, can solve problems such as damage to the rights and interests of legitimate multicast users, inability to identify multicast user terminal equipment, and difficulty in implementing multiple billing methods, so as to improve adaptability, prevent The effect of the problem of misappropriation of network resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
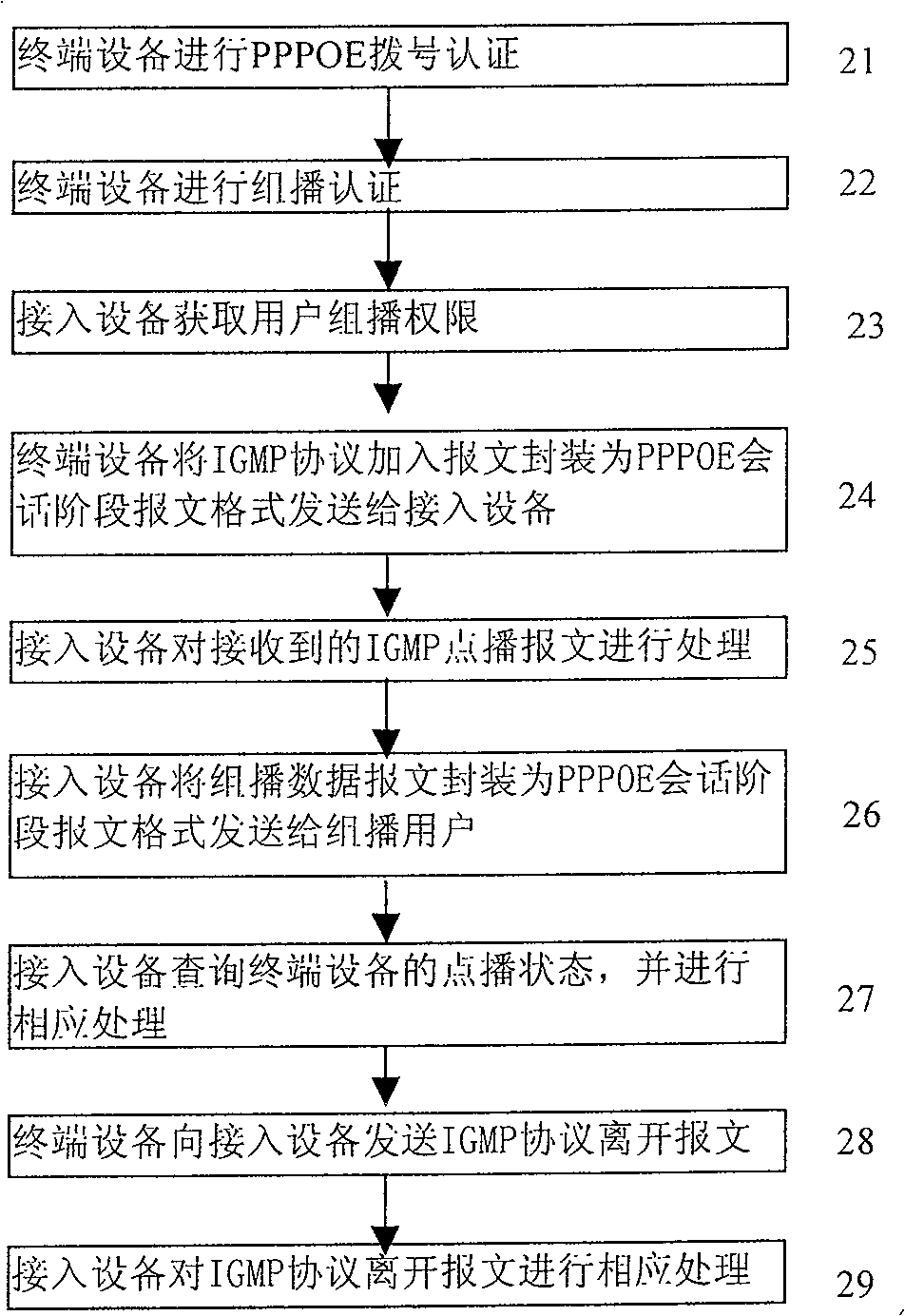
[0099] The core idea of the present invention is: the terminal equipment subordinate to the multicast user performs PPPOE dial-up authentication. After the authentication is successful, the IGMP join message is encapsulated into a PPPOE session phase message format and sent to the access device. The IGMP join message in the phase message format determines that the terminal device sending the message is a legal terminal device.
[0100] The reasons for encapsulating the IGMP join message into the PPPOE protocol message format are:
[0101] If the IGMP join message is still sent according to the general Ethernet message, the access device does not know whether the terminal device has passed the PPPOE dial-up authentication; and the method of encapsulating the IGMP join message into the PPPOE protocol message format ensures that the terminal The device must pass PPPOE authentication, and it can be seen from this process that the IGMP join message must be encapsulated into the d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com