Imformation providing and user verifying device and method
A technology for user authentication and equipment, applied in the direction of user identity/authority authentication, digital data authentication, instruments, etc., can solve problems such as increased working hours
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] Preferred embodiments of the present invention will now be described with reference to the accompanying drawings.
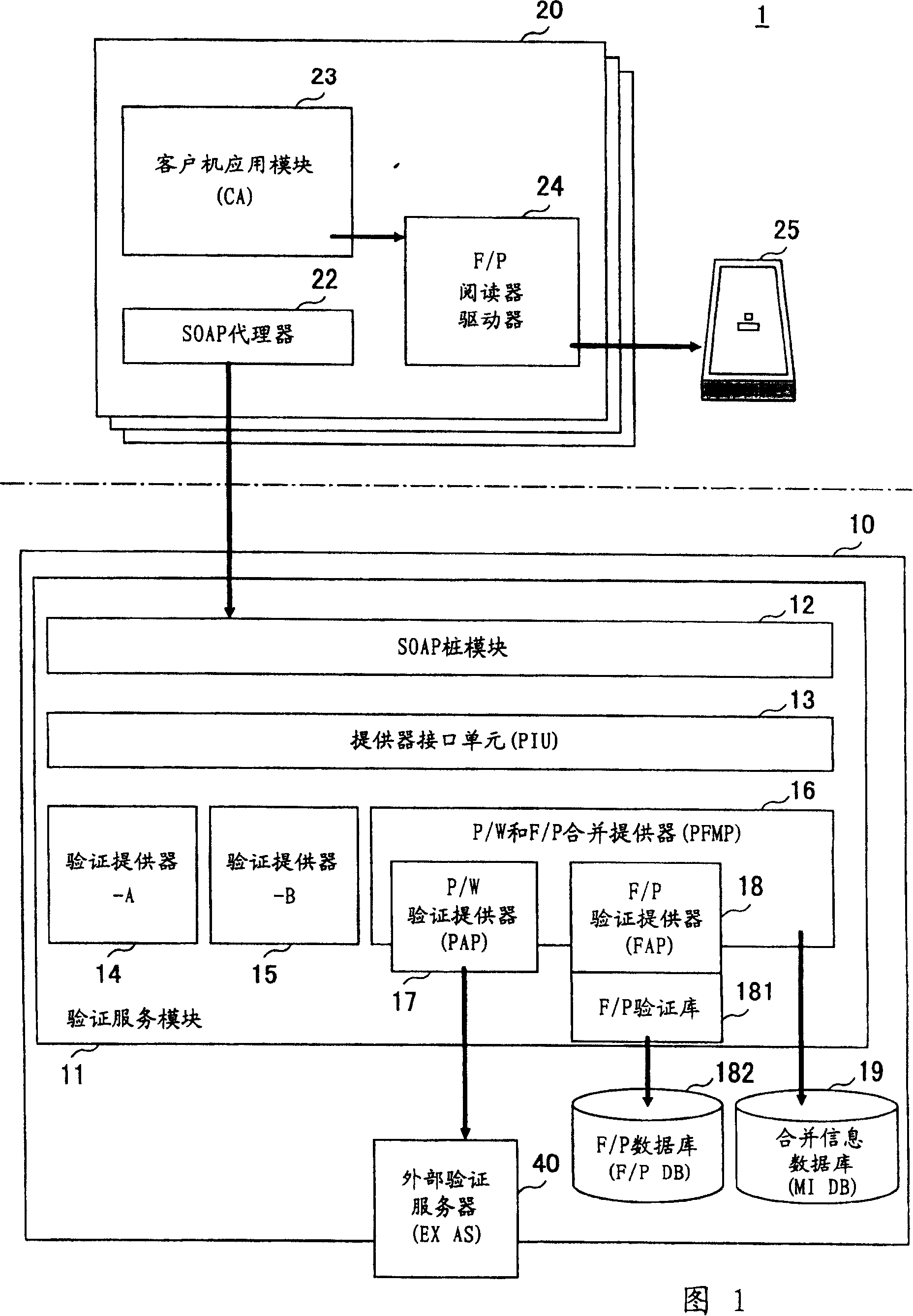
[0053] FIG. 1 is a block diagram of a first preferred embodiment of the user authentication system of the present invention.
[0054] As shown in FIG. 1 , an authentication system 1 in this embodiment includes an authentication server 10 and a terminal 20 connected through a network such as the Internet and a LAN (Local Area Network).
[0055] The terminal 20 is a terminal such as a PC (Personal Computer) used by a user. The terminal 20 is equipped with a SOAP proxy 22 , a client application module 23 , and a fingerprint reading device driver 24 .
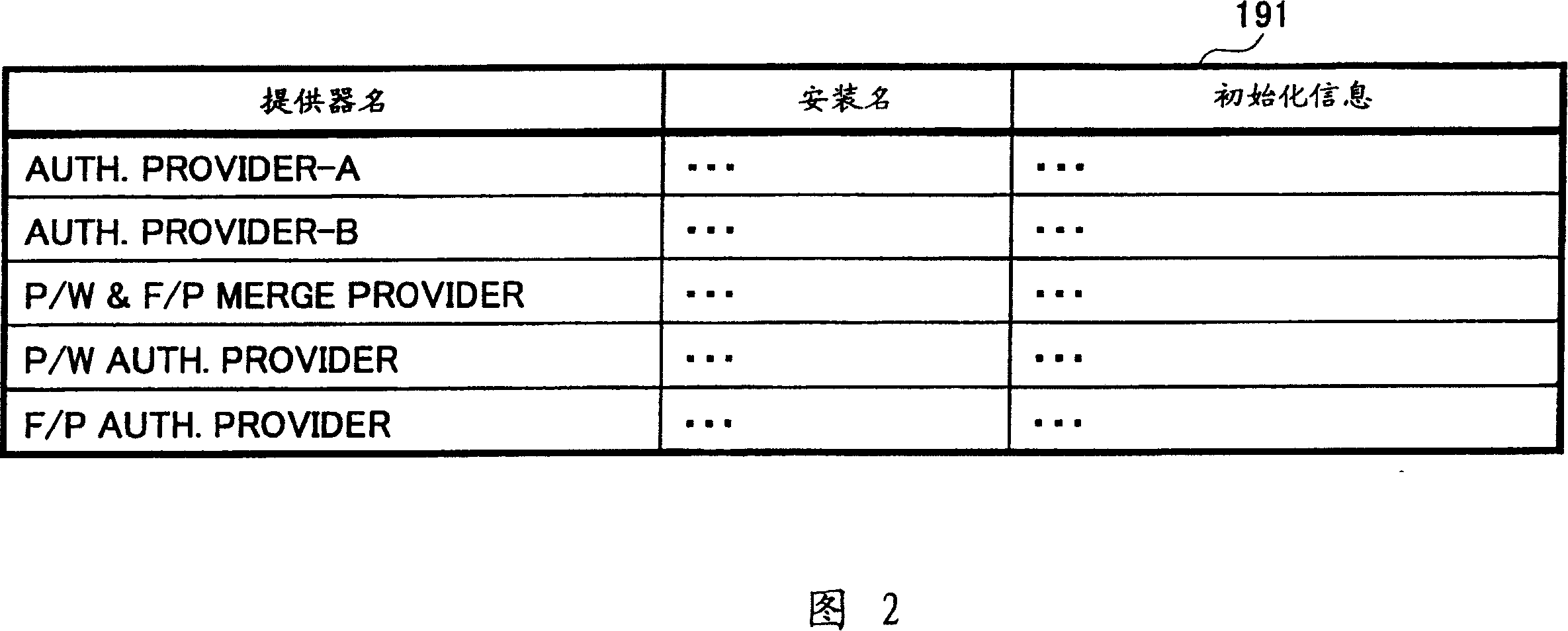
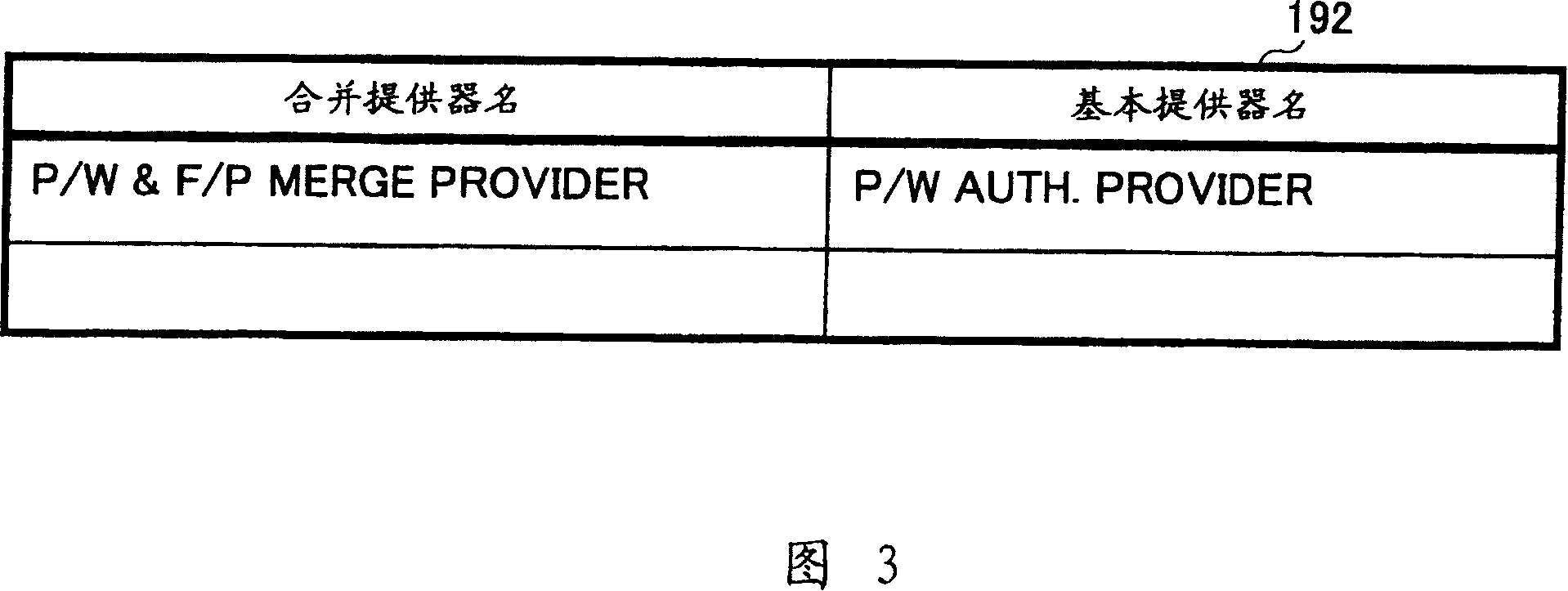
[0056] The SOAP agent 22 is a module that utilizes SOAP (Simple Object Access Protocol) to realize communication between the terminal 20 and the verification server 10, and as a functional interface transparent to the client application module 23, provides the function of the verification server 10 to Client ap...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com