Network behaviour alarming system and method for network auditing
An alarm system and network technology, applied in the field of network information security, can solve problems such as difficult real-time notification and single alarm method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
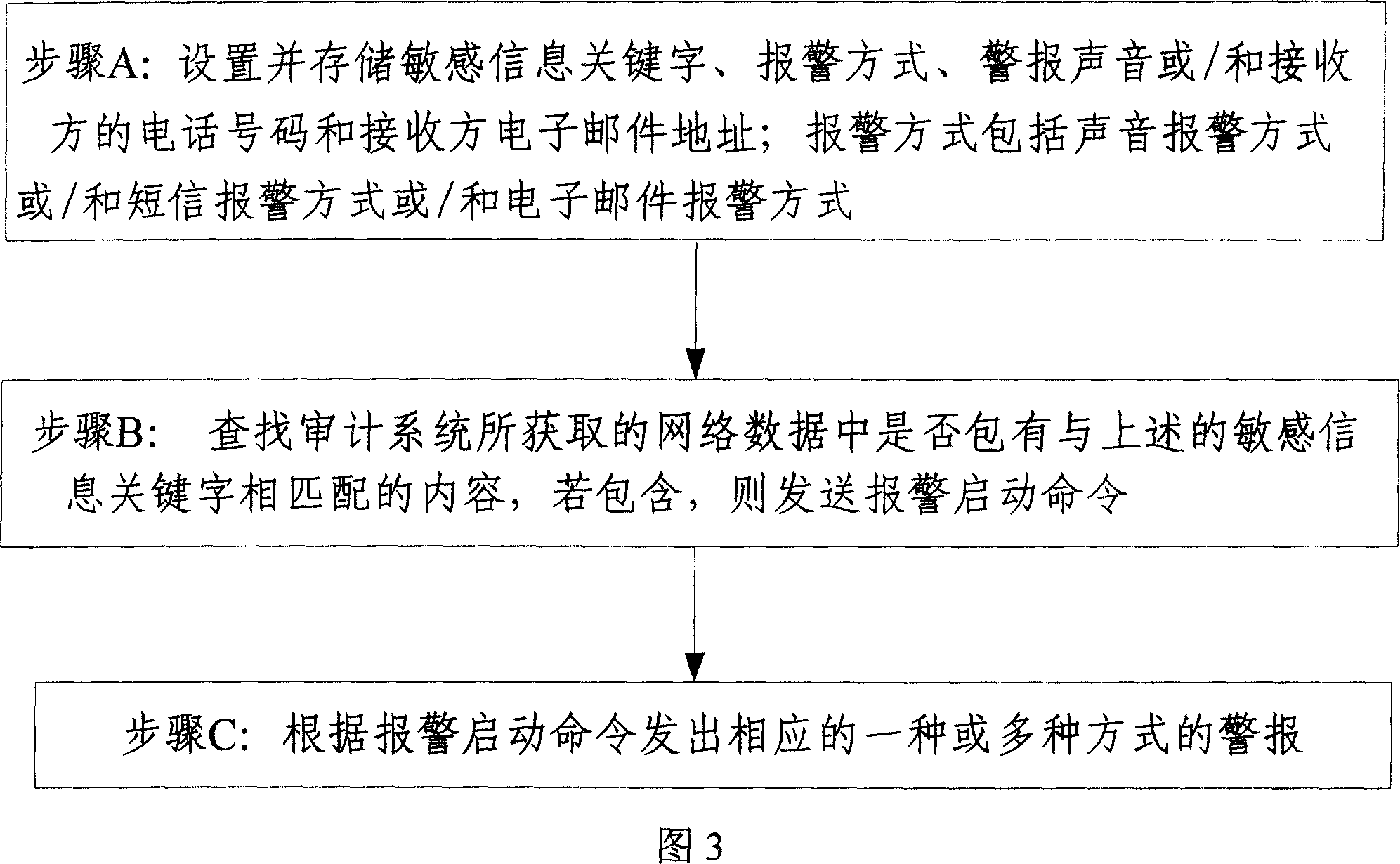
[0023] As shown in Figure 1, the network behavior alarm system of the present invention comprises an alarm policy management module, a data analysis module and an alarm module; Phone number, where the alarm method includes sound alarm method or / and text message alarm method;
[0024] The data analysis module is used to store the sensitive information keywords set by the above-mentioned alarm policy management module, and analyze the network data obtained by the audit system to find out whether there is content matching the sensitive information keywords, and if so, send Alarm start command to alarm module;
[0025] The alarm module is configured to issue an alarm in one or more corresponding alarm modes according to the above-mentioned alarm start command, and store the alarm sound or / and the receiver's phone number set by the above-mentioned alarm policy management module.
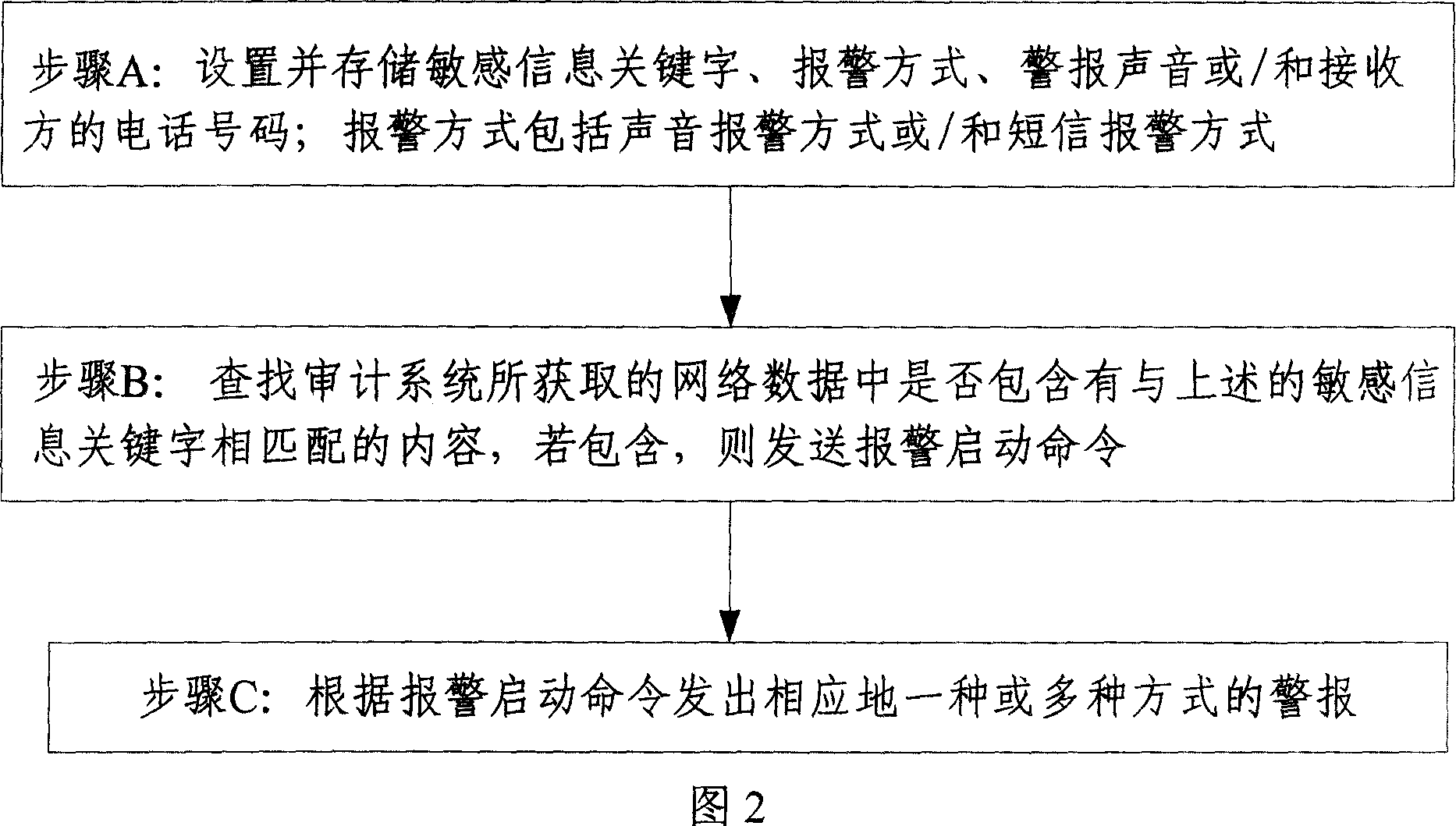
[0026] As shown in Figure 2, the network behavior warning method of the present invention comprises t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com