Encryption/decryption and signature method and system
A decryption algorithm and encryption algorithm technology, applied in the field of e-commerce applications, can solve problems such as insecurity, large amount of key calculation, and slow operation speed of non-knapsack cryptosystem
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
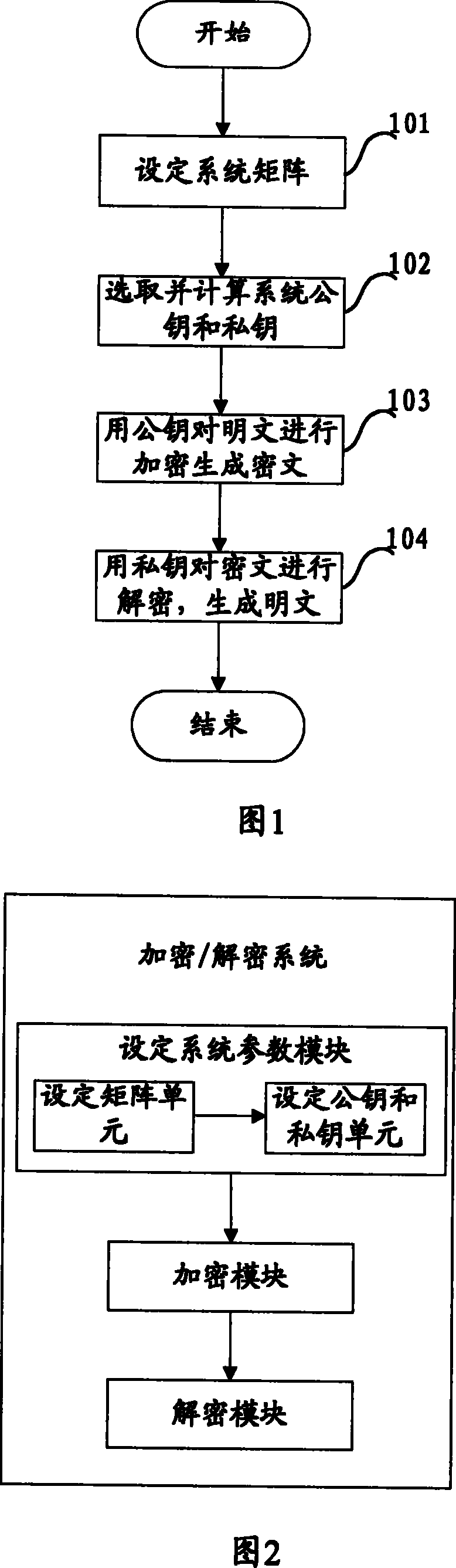
[0086] Referring to Fig. 1, the present invention provides a kind of encryption / decryption method, described method step is as follows:
[0087] Set system parameters and generate public key and private keys W, m, M, where is an n-order matrix; the specific execution steps are as follows:
[0088] Step 101: Set up the system matrix, let Z and N be sets of integers and positive integers respectively, and M(Z) and M(N) respectively represent the matrix classes whose elements belong to Z and N. Randomly select two matrices B and C of order n×n, satisfying B∈M(Z), C∈M(N).
[0089] Wherein, the larger the dimension of the matrix is, the higher the security is. Generally, when n>100, sufficient security is guaranteed. In this embodiment, the dimension n=128 of the matrix can be determined;
[0090] Select B as a matrix in which each element is an integer whose absolute value is less than 8;
[0091] Select C as a matrix in which each element is a positive integer...
Embodiment 2
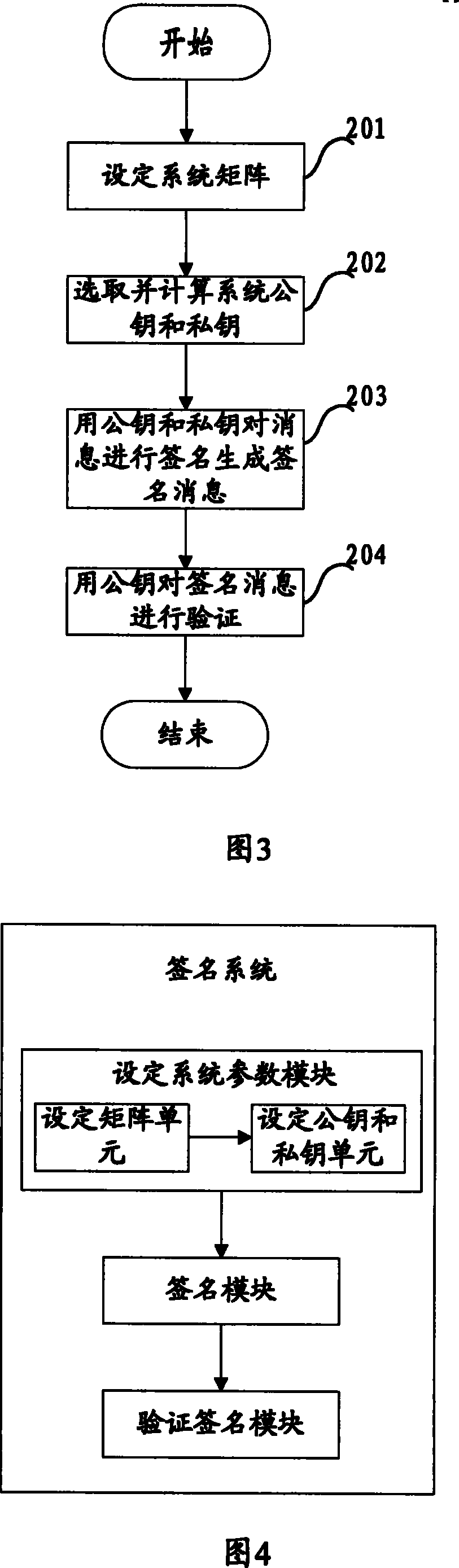
[0149] Referring to Fig. 2, the present invention also provides an encryption / decryption system, the system includes a system parameter setting module, an encryption module and a decryption module;
[0150] The module for setting system parameters generates a public key by setting system parameters and private keys W, m, M, where is an n-order matrix;
[0151] The encryption module is used to use the public key To encrypt the plaintext x, the encryption algorithm uses the quadratic knapsack algorithm: , generate ciphertext y;
[0152] The decryption module is used to decrypt the ciphertext y with the private key W, m, M, and the decryption algorithm is:
[0153] calculate M =y 1 , and then calculate z=-1 the y 1 > m , then by z = Σ i = 1 n x i · 2 i - ...
Embodiment 3
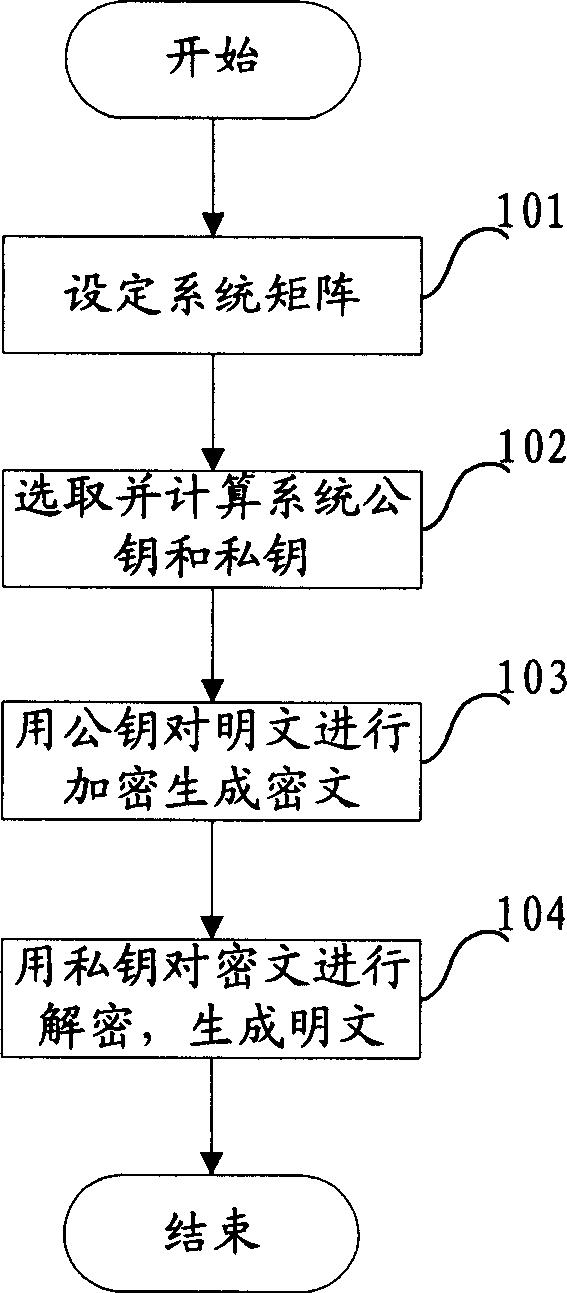
[0165] Referring to Fig. 3, the present invention also provides a kind of signature method, described method comprises the following steps:
[0166] Set system parameters and generate public key , m, M and private key W, where is an n-order matrix, and the specific steps are as follows:
[0167] Step 201: Set the system matrix.
[0168] Step 202: Select and calculate the system public key , m, M and private key W.
[0169] The specific parameter setting process in step 201 to step 202 is the same as step 101 to step 102 in embodiment 1, and will not be repeated here, wherein, there is no limit to the selection of each element in B and C. When signing, select the absolute value of the element The value should be increased accordingly to avoid cracking the private key through exhaustive methods.
[0170] Step 203: Sign the message with the public key and private key, and the signature algorithm is as follows:
[0171] For any message y, calculate the Ha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com