Security policy based network security management system and method
A security strategy and network security technology, applied in the field of network security management system based on security strategy, can solve problems such as damage to the organization's image, affect network availability, cannot effectively prevent attacks, etc., and achieve the effect of improving security
Inactive Publication Date: 2005-04-06
沈明峰 +3
View PDF0 Cites 41 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Traditional boundary security technologies (such as firewalls) rely on one (or several) security devices to ensure security for thousands of nodes in the network, which can easily become the performance bottleneck of the entire network
In addition, perimeter security technologies often become a single point of failure in the n
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
 Login to View More
Login to View More PUM
 Login to View More
Login to View More Abstract
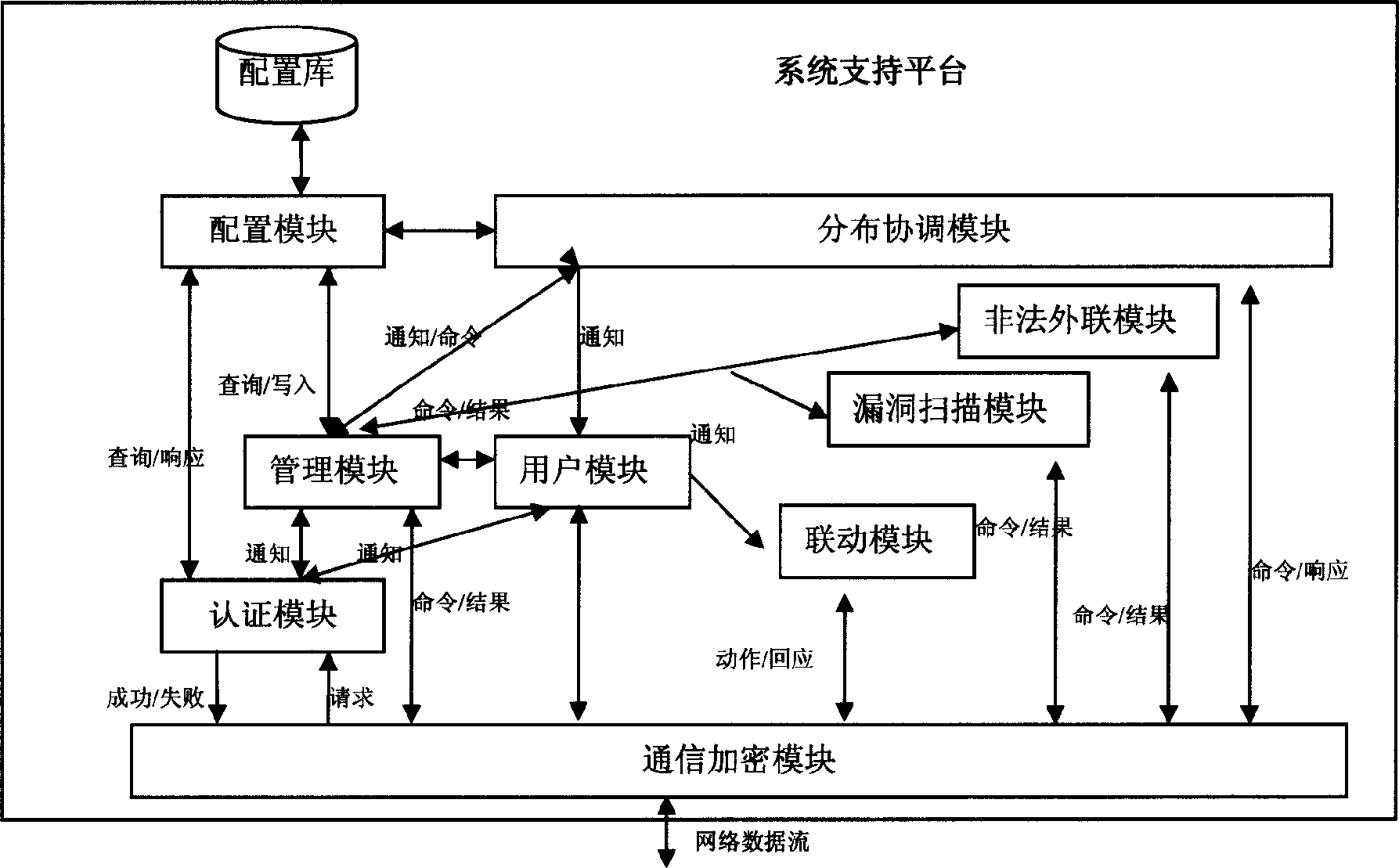
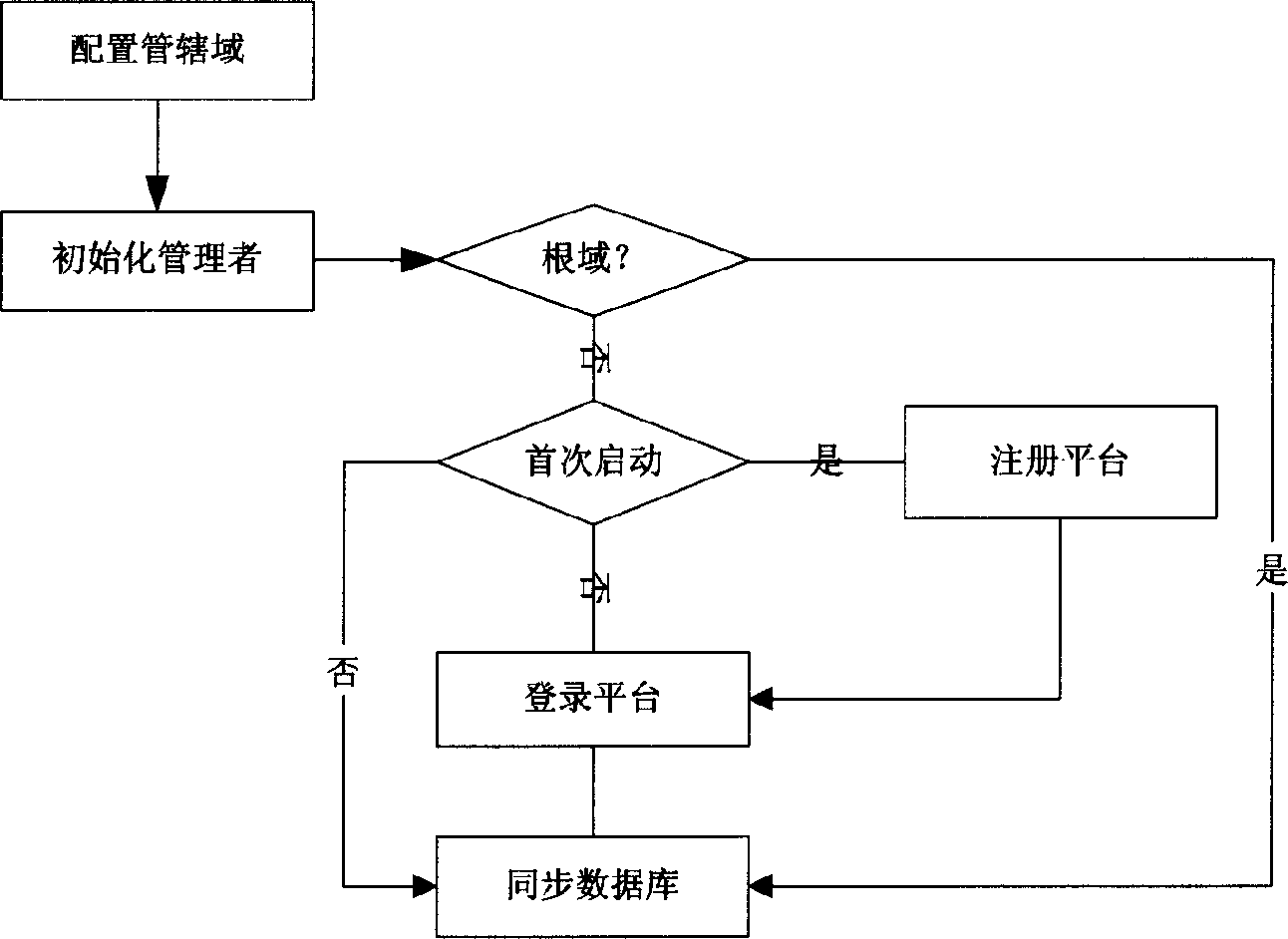
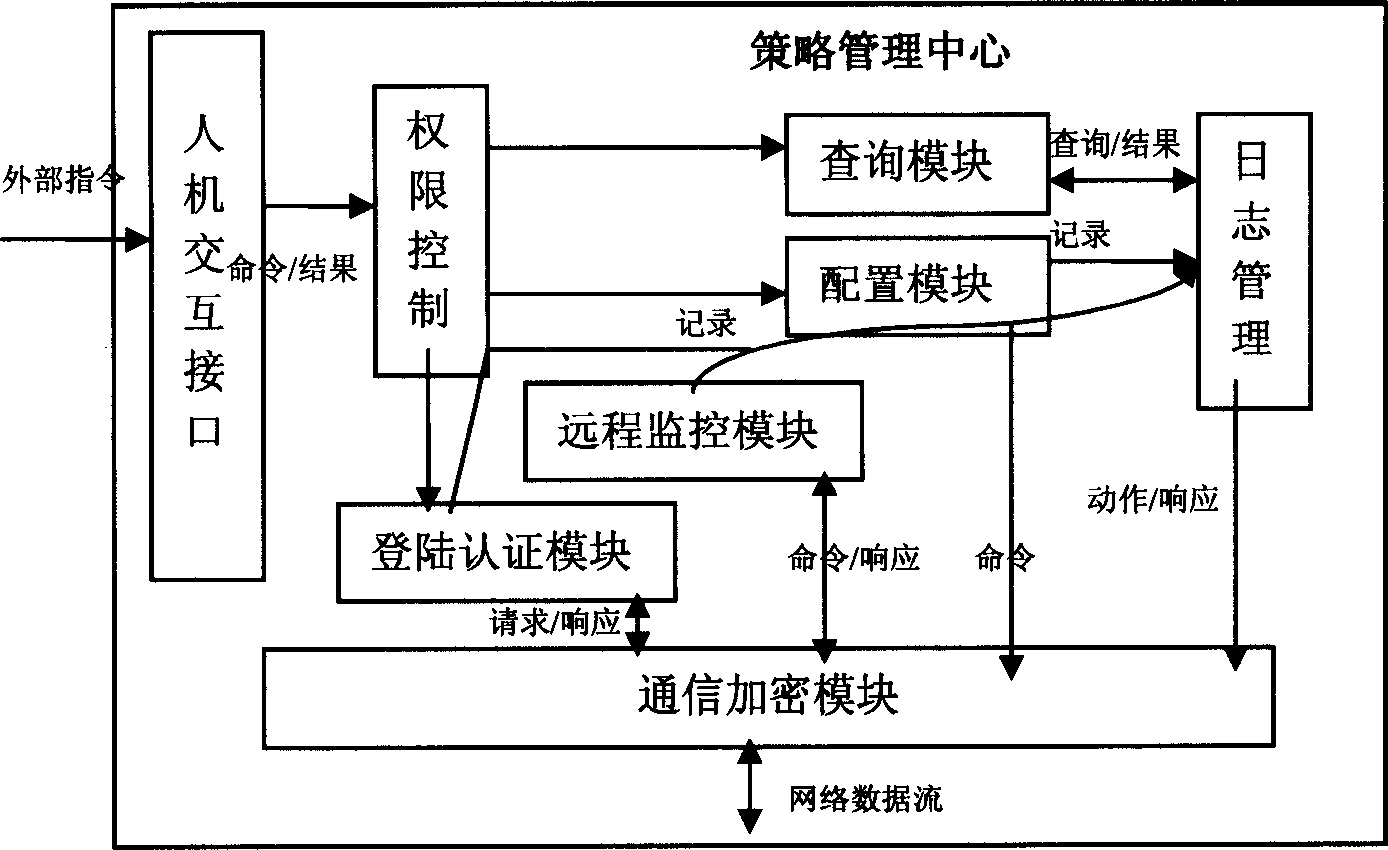
This invention discloses a network safety management system and method, which comprises system supportive platform, strategy management center, strategy executive points and log server. It is first to set protection aim and spreads the strategy to the aim device and system strategy executive through system supportive platform. The strategy executive points executes the strategy and acknowledges the log server with results.
Description
technical field [0001] The invention belongs to the technical field of network security control, and in particular relates to a security strategy-based network security management system and method. Background technique [0002] In order to solve the increasing network security problems, people adopt many technologies, such as firewall, intrusion detection, virtual private network, virus protection, vulnerability scanning and so on. These technologies can guarantee the security of the network to a certain extent, but there are still some shortcomings, mainly: [0003] Does not address attacks from within the organization. Most of the traditional security technologies are oriented to the boundary of the organization, relatively speaking, there is a lack of technical means for desktop security and internal network security; [0004] It is difficult to provide a holistic security solution. The security of a large-scale network is a systematic project that requires the cooper...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04L12/24
Inventor 沈明峰李胜磊张勇王军
Owner 沈明峰
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Patsnap Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com