Network control method and equipment
A technology for controlling equipment and control algorithms, applied in the field of communication control, can solve problems that cannot be solved at the same time, and data packet filtering technologies are incompatible with each other
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0027] Hereinafter, preferred embodiments of the present invention will be specifically described.
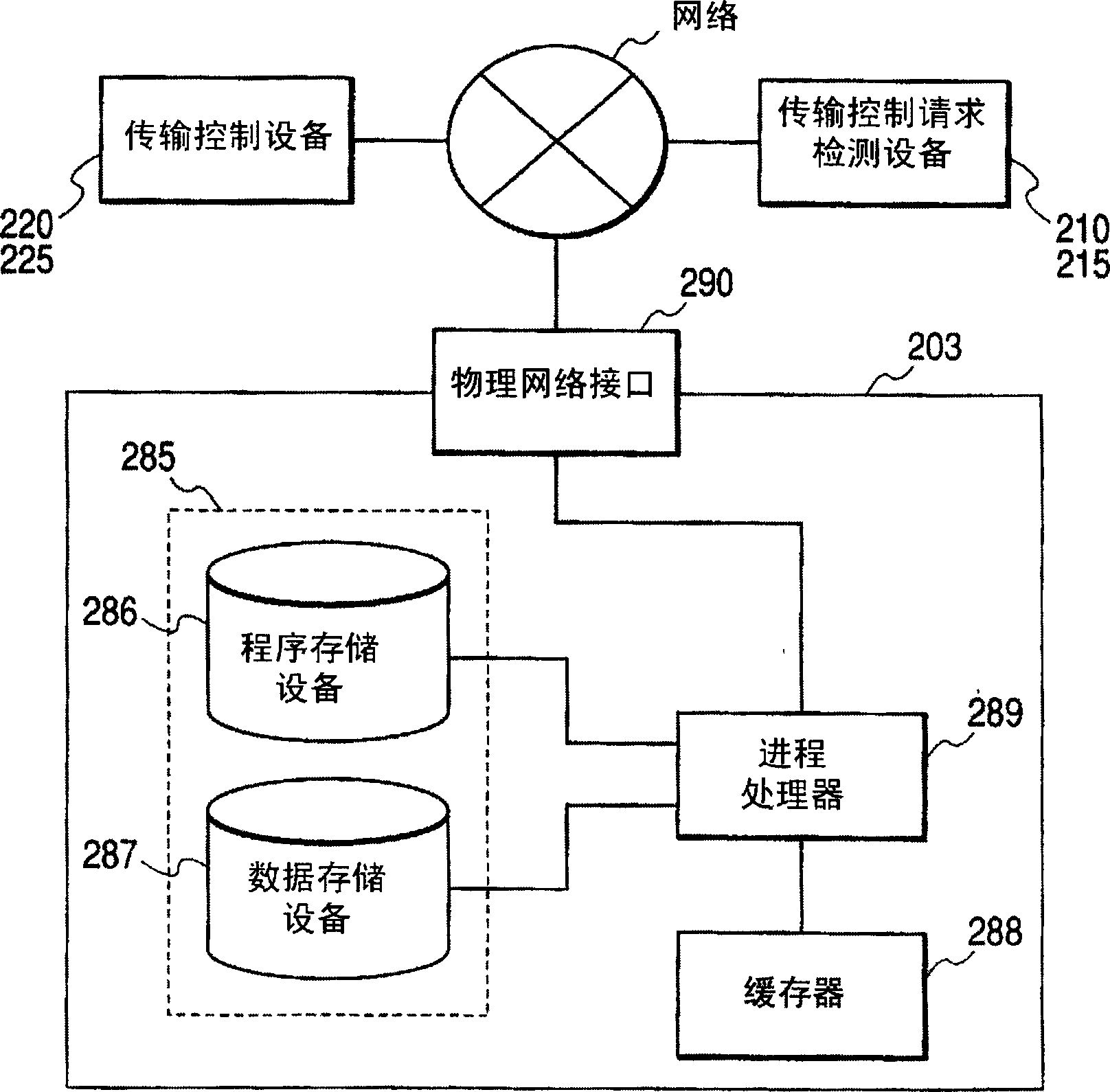
[0028] Specific examples of the transmission control request detection device in this embodiment will be described hereinafter, such as an intrusion monitoring system for detecting abnormal transmission, a user authentication server for user firewall authentication, and a user authentication server for distribution The firewall's policy server is available. Specific examples of transmission control devices, such as packet filters, bandwidth managers, application gateways, and personal firewalls, are available. Preferably, the transmission control computing device can communicate with the transmission request detection device and the transmission control device in a reliable communication state by using the network for management, encapsulation of information, and the like. The network is usually owned by a telecommunications company or by the operator of the corporate network. ...
Embodiment 2
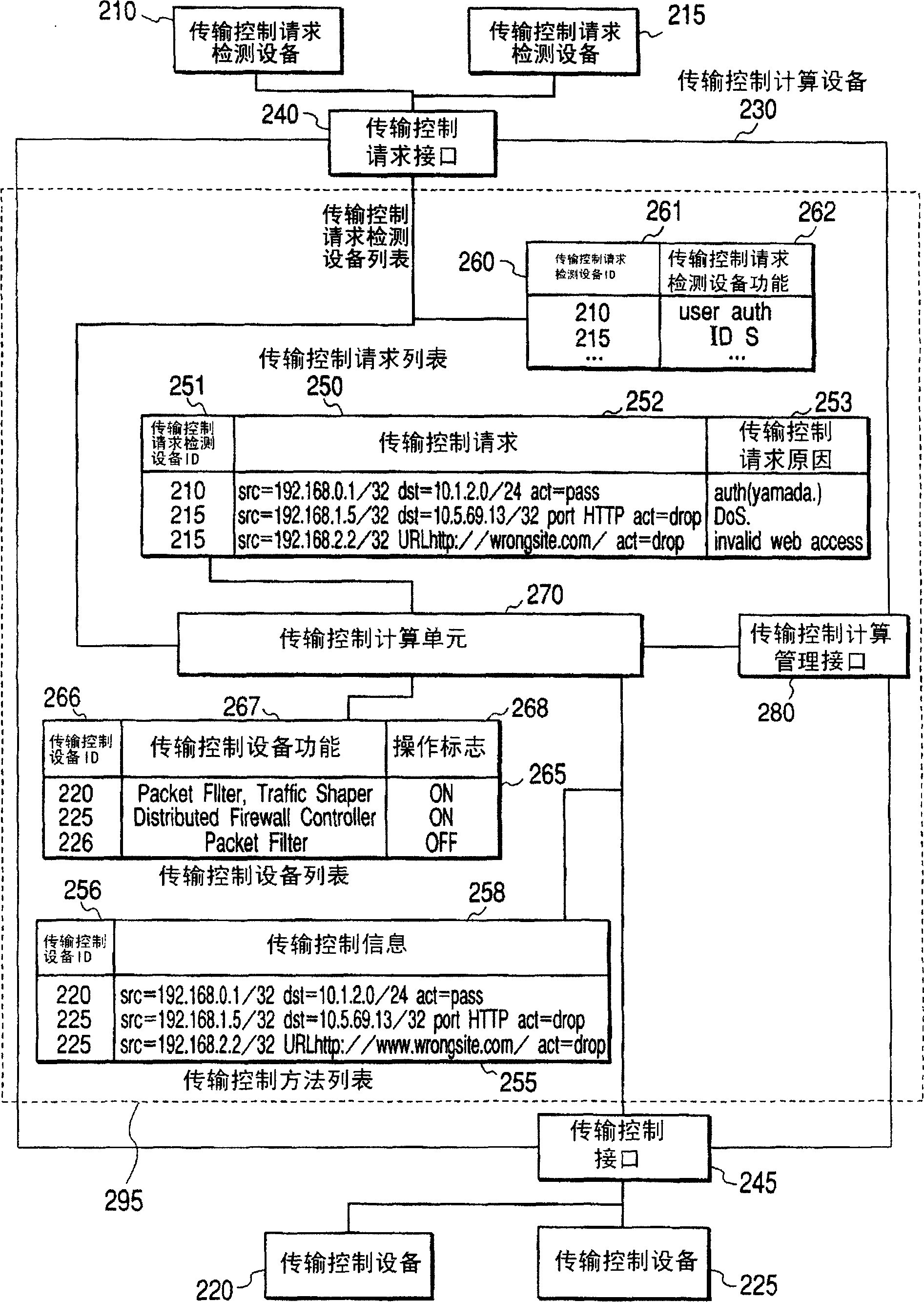
[0053] According to the present invention, Figure 5 An example of a network configuration is shown. The corporate network 500 includes a backbone egress router 510, a transmission control router 520, an authentication server 530, an intrusion detection system 540, a distributed firewall policy server 550, and a terminal 560 at the ingress of the distributed firewall. The transmission control computing device 230 is connected to the authentication server 530, the intrusion monitoring system 540, and the terminal 560 at the ingress of the distributed firewall through the transmission control request interface 240, and to the backbone egress router 510, the transmission control router 520, and the transmission control interface 245. Distributed Firewall Policy Server 550.
[0054] When a user of the terminal 570 located outside the company network wants to access the terminal 560 inside the company network, first, the user must log in to the authentication server 530 . When lo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com