Post-loan supervision method based on privacy calculation
A privacy and numerical technology, applied in the information field, can solve problems such as the lack of post-loan supervision programs, and achieve the effects of improving efficiency, protecting business privacy, and protecting privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
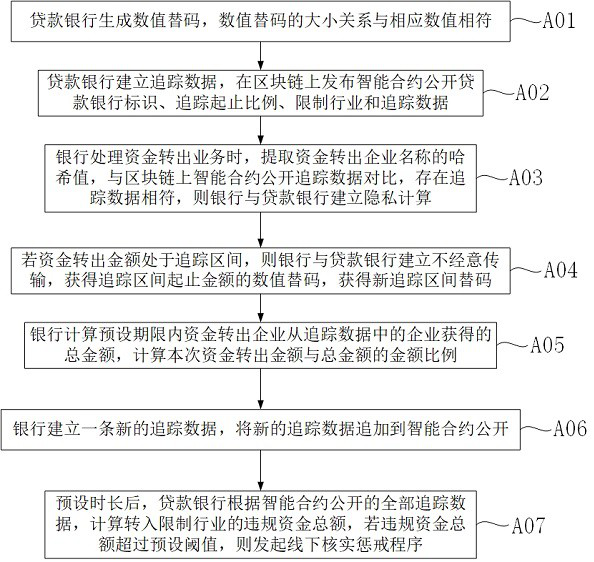
[0025] A post-loan supervision method based on privacy calculation, please refer to the appendix figure 1 , including: Step A01) The loan bank generates a numerical replacement code, and the size relationship of the numerical replacement code is consistent with the corresponding value. The numerical substitution code is used when the numerical value needs to be compared in the subsequent steps, and the numerical value is not used directly, so that the specific amount of the transaction in the enterprise account can be kept secret, and the security of the enterprise's business data can be effectively protected. Step A02) The loan bank establishes tracking data, records the hash value of the ID of the issuing bank and the name of the enterprise, and publishes the smart contract on the blockchain to disclose the ID of the loan bank, the tracking start and end ratio, the restricted industry and the tracking data. The enterprise is referred to by the hash value of the enterprise na...
Embodiment 2
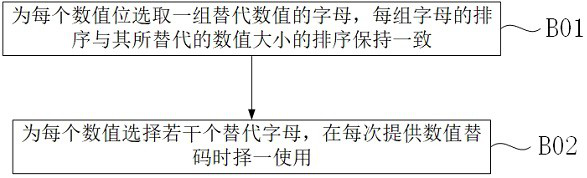
[0062] A post-loan supervision method based on privacy calculation, this embodiment provides a new method for establishing inadvertent transmission between a bank and a loan bank on the basis of the first embodiment. Including: Step F01) The lending bank generates a random integer for each possible value of each numerical bit, and associates the cosine value of the random integer with the corresponding value and discloses it; Step F02) The bank generates a second random The cosine value of the second random integer is sent to the lending bank; step F03) The bank uses the double angle formula to calculate the cosine value of the product of the random integer and the second random integer corresponding to the numerical value to be replaced by the code, and takes the absolute value of the cosine value of the product. The pre-set bit is used as the secret key, the bank releases the decryption smart contract, and uploads the secret key and the value to be replaced by the numerical c...
Embodiment 3
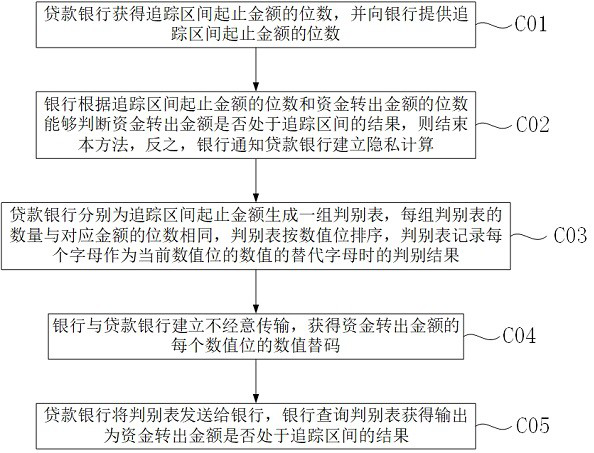
[0068] A post-loan supervision method based on privacy calculation, please refer to the appendix Image 6 , in this embodiment, the method for the loan bank to generate an asymmetric key for the value value is: step G01) to generate a private key value and a public key value, the product of the private key value and the public key value is equal to an integer multiple of 2π plus 1, The value of the private key is a positive odd number; the method for the bank to use the public key to encrypt the secret key is: Step G02) Generate an intermediate number so that the cosine value of the intermediate number retains the previous specified decimal place, and the value of the reserved decimal place is exactly the secret key Key , and at the same time ensure that the number of decimal places of the intermediate number is less than or equal to the integer number of digits of the product of the private key value and the public key value, and calculate the cosine value of the product of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com