Anti-quantum-attack electronic contract signing method and system
An anti-quantum attack and electronic contract technology, applied in data processing applications, instruments, digital data authentication, etc., can solve security risks, security risks and other issues, and achieve the effect of ensuring fairness and small amount of mathematical calculations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0047]Symmetric key algorithm is a cryptographic algorithm that uses the same secret key for encryption and decryption. The characteristics of this cryptosystem are that the amount of mathematical operations is small, the encryption speed is fast, and it is easy to handle, but the distribution of symmetric keys is difficult. The emergence of quantum cryptography network solves the problem of symmetric key distribution. Through quantum cryptography network, both encryption parties can easily obtain a shared symmetric key by means of quantum key distribution.
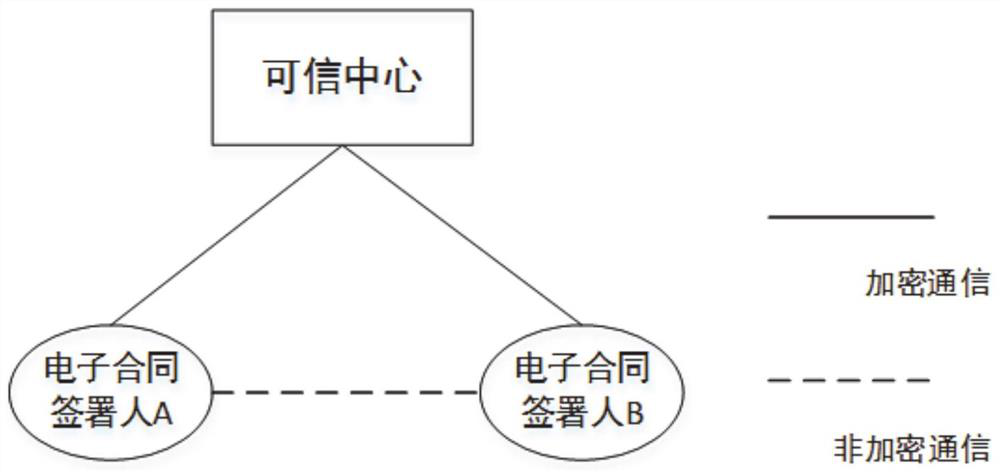
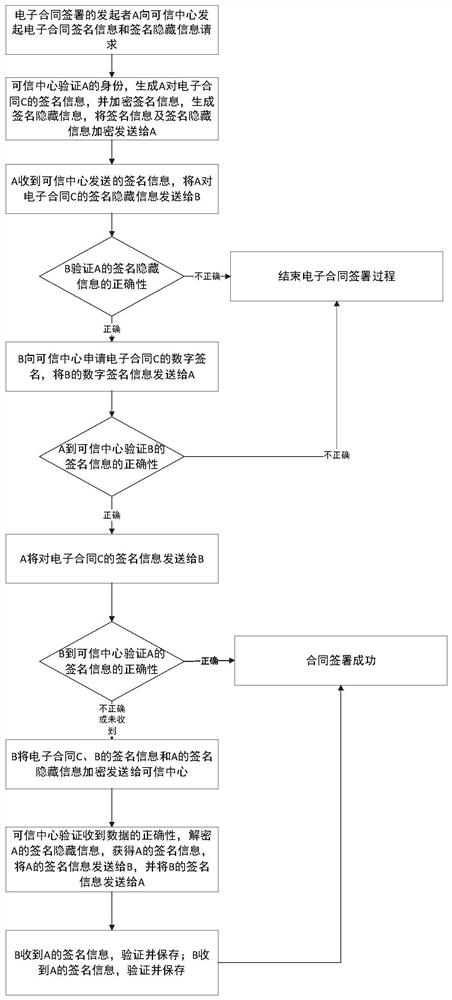
[0048] This embodiment relies on the abundant symmetric key resources of the quantum cryptography network to implement an electronic contract signing method that is resistant to quantum attacks. attached figure 1 For the relationship between the signatory and the trusted center, the functions of each component are detailed as follows:
[0049] The trusted center is a third-party trusted organization, which is used for d...
Embodiment 2
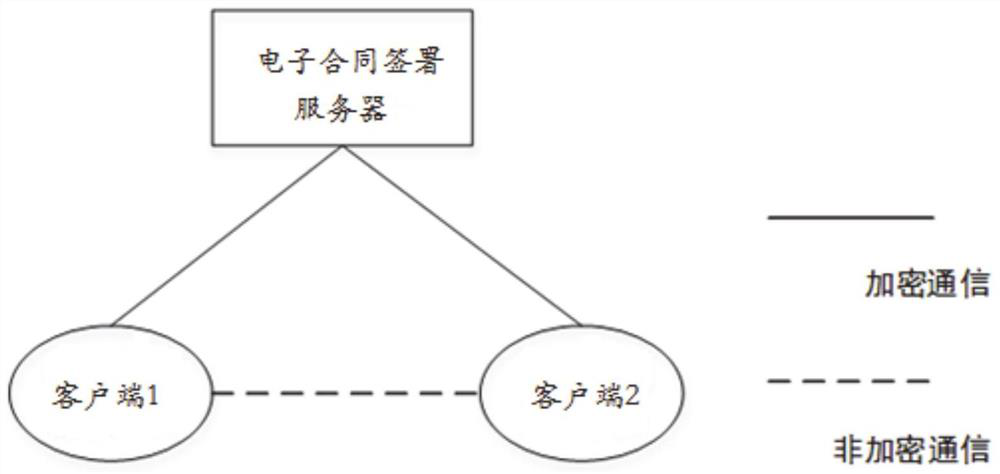
[0073] In this embodiment, a quantum-attack-resistant electronic contract signing system is provided, including:
[0074] The electronic contract signing server is configured as a trusted third party in the electronic contract signing process, distributes the shared key to the signers of each client through the quantum cryptography network, performs symmetric key signature on the electronic contract, and encrypts the digital signature Obtain the signature hidden information, divide the key of the true random number digital signature keystore according to the length used for each digital signature, and perform sequential labeling to verify the electronic contract signature;
[0075] Several clients are configured to provide each signer with information services in the process of contract signing, and use the shared key to communicate with the electronic contract signing server.
[0076] The electronic contract signing server distributes the shared key to the certified signers o...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap