Data security protection method based on tablet computer
A tablet computer, data security technology, applied in digital data protection, electronic digital data processing, digital data authentication and other directions, to achieve the effect of enhancing layering, enhancing data security protection capabilities, and realizing multi-level three-dimensional security protection
Active Publication Date: 2022-06-10
SHENZHEN GESHEM TECH CO LTD
View PDF7 Cites 3 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
[0005] For this reason, the invention provides a data security protection method based on a tablet computer to overcome the oversimplification of tablet computer data security verification and the lack of core data in the prior art. The issue of hierarchical protection
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
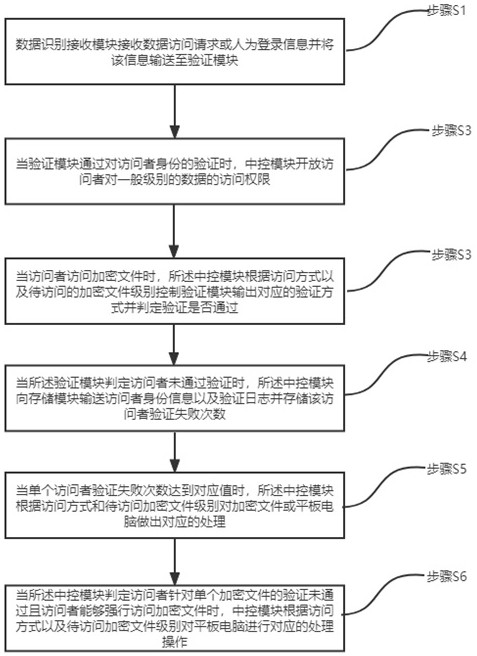
The invention belongs to the technical field of data security protection, and particularly relates to a data security protection method based on a tablet personal computer, which comprises the following steps: a data identification receiving module receives a remote access request or artificial login information and transmits data to a verification module; when the verification module passes verification, the central control module opens general-level data access authority; when the encrypted file is accessed, the central control module controls the verification module to output a corresponding verification mode according to different file levels and judges whether verification is passed or not; when the visitor does not pass the verification, the central control module transmits relevant information of the visitor to the storage module; when the number of times of verification failure reaches a corresponding value, the central control module performs corresponding processing on the encrypted file or the tablet computer according to different levels; and when the visitor does not pass verification and can visit forcibly, the central control module carries out corresponding processing on the tablet computer according to different conditions. Through innovation of the data security protection method, multi-level three-dimensional protection of the data security of the tablet personal computer is realized.
Description
technical field [0001] The invention relates to the field of data security protection, in particular to a data security protection method based on a tablet computer. Background technique [0002] With the rapid development of social economy and the overall progress of science and technology in recent years, the application range of tablet PCs will be more and more extensive. At present, the applications of tablet PCs are mainly concentrated in games, audio-visual entertainment and other aspects. [0003] However, for some special users, data security is extremely important. Once the tablet is lost and data leakage occurs, the consequences will be disastrous. And under the situation that tablet computer application is more and more common at present, some work must be finished with tablet computer again. Therefore, the data security protection of the tablet computer is very important in the new situation. However, there is not much enhancement to the data security protecti...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Applications(China)
IPC IPC(8): G06F21/31G06F21/32G06F21/60
CPCG06F21/31G06F21/32G06F21/602G06F2221/2141G06F2221/2139G06F2221/2107G06F21/1078
Inventor 崔云颀万建华杨宏伟
Owner SHENZHEN GESHEM TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com