Network security test generation method based on knowledge graph
A knowledge graph, network security technology, applied in the field of network security test generation, can solve problems such as inefficiency, inefficiency, inability to correlate experience and knowledge, and achieve the effect of improving integrity and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
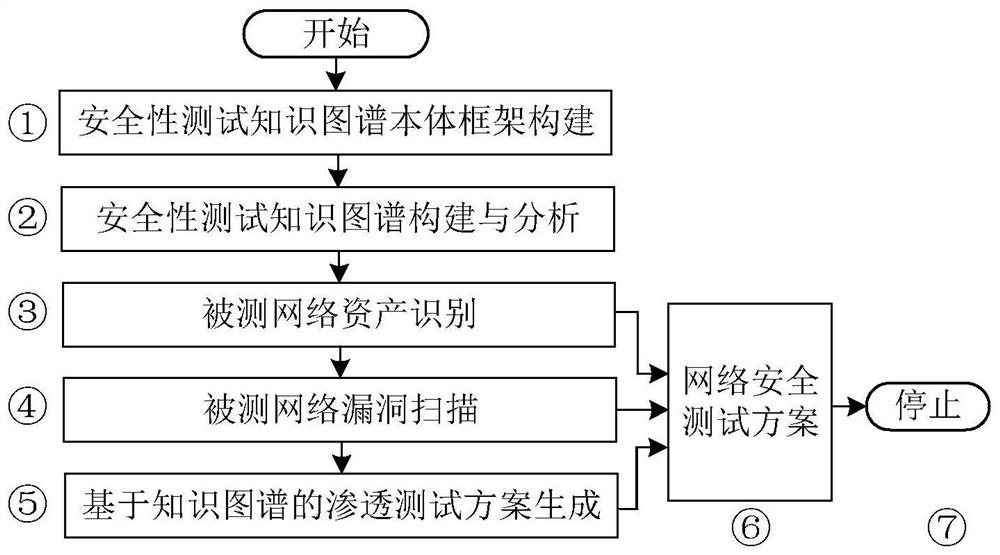
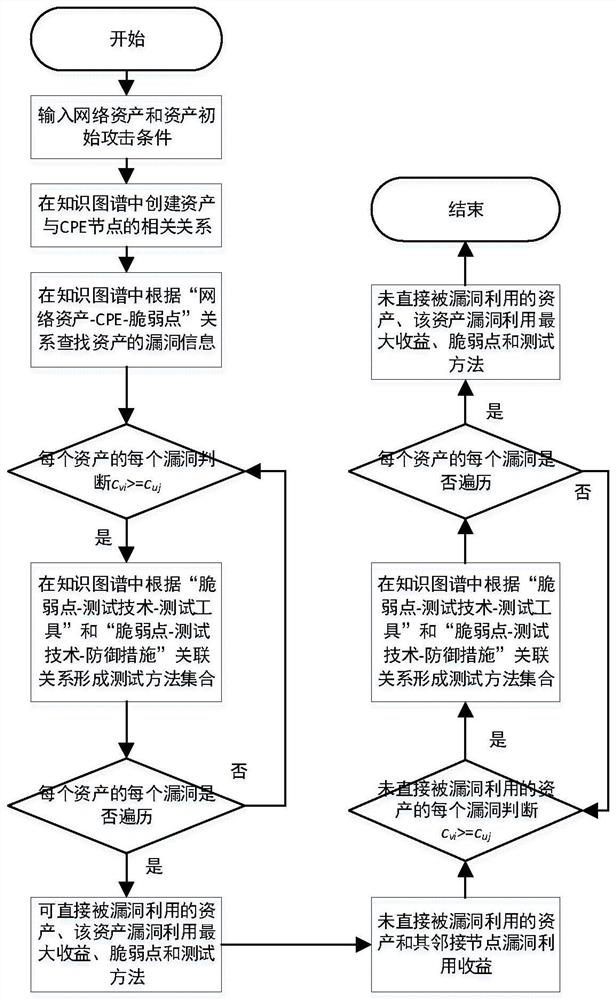
[0080] like figure 1 , 2 As shown in , 3, a generation method of network security testing based on knowledge graph, firstly, the ontology framework related to asset model, vulnerability point model and attack technology model in the field of security testing is designed; then, the historical data of network security is extracted, A graph database is used to build a network security test knowledge graph; finally, a method for generating a network security test based on a knowledge graph is proposed, which includes the following detailed steps:
[0081] Step 1. Construction of security test knowledge map ontology framework
[0082]The ontology in the field of cyberspace security is the semantic basis of the knowledge graph. It is mainly composed of entities, relationships between entities, and attributes of entities and relationships. It can be used to organize, represent, and share knowledge related to network security. For the field of security testing, build a network secur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com