Dynamic application protection system and method based on attack load and attack behavior
A technology of dynamic application and protection system, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as user A's inability to access successfully, web application system damage, etc., to improve work efficiency and user experience, and alleviate attack pressure. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
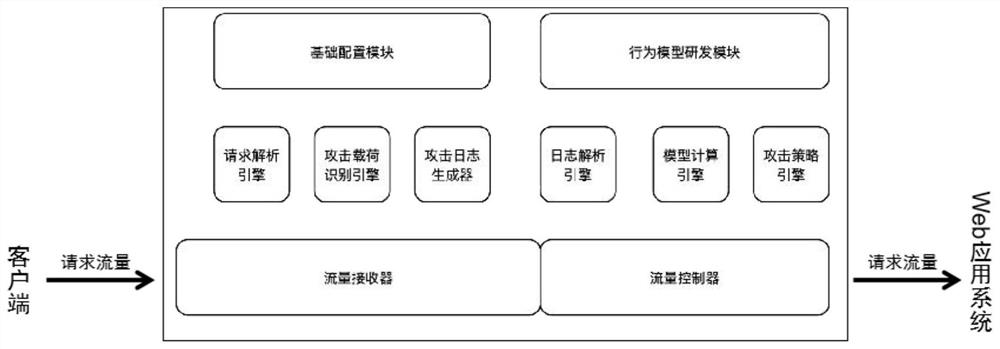
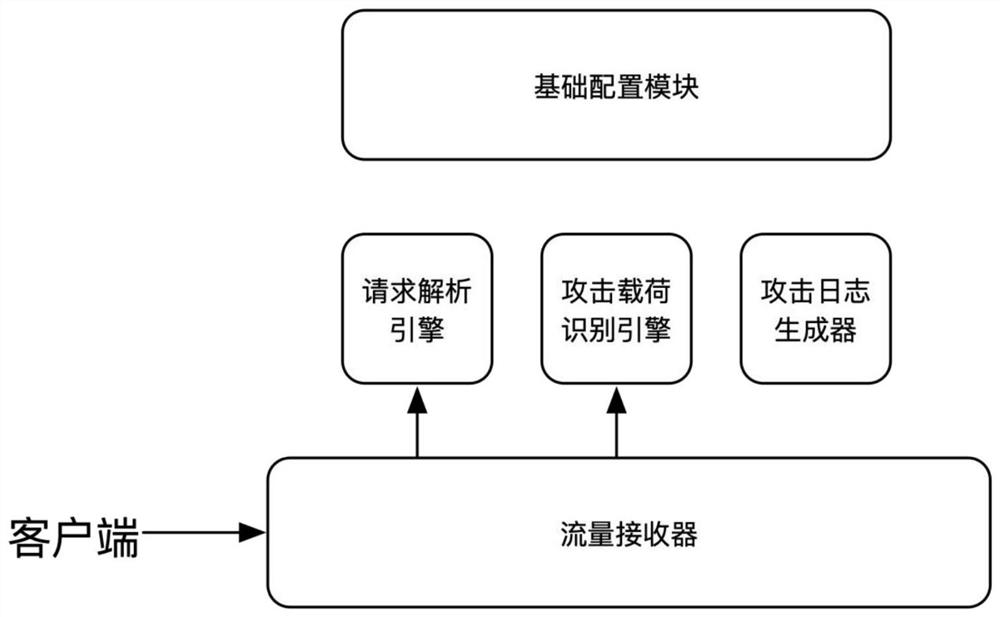
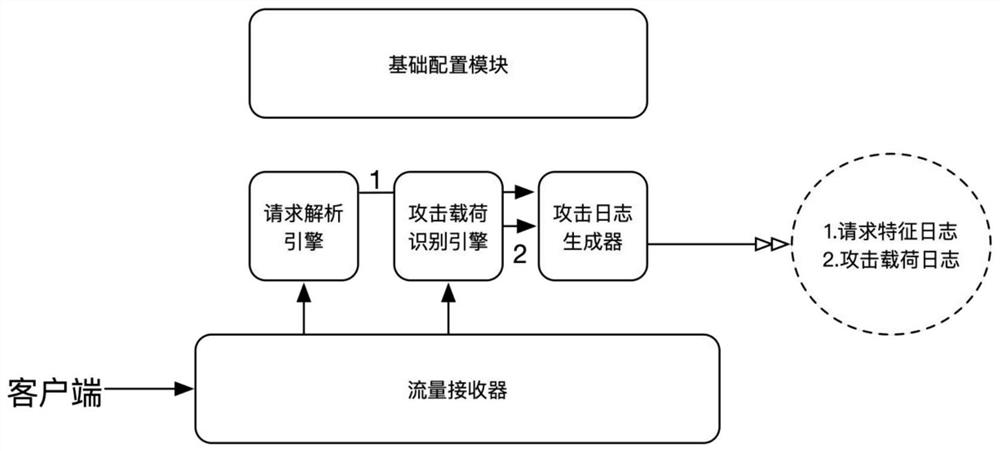
[0050] The protection system as a whole consists of two parts: basic attack identification function and behavior model function. External request traffic passes through the traffic receiver, and the attack load matching and request characteristics of the request are identified through the basic attack identification function to form attack load logs, request Feature logs, through model analysis, research and development, establish models and issue them, calculate and match user behaviors and risk levels in real time, match defense strategies, and obtain results and issue them to the controller.
[0051] Such asfigure 1 As shown, a dynamic application protection system based on attack load and attack behavior, including a flow receiver, a flow controller, a basic configuration module, a behavior model development module, a first analysis module, and parameter setting through the behavior model development module The second parsing module, where,
[0052] The traffic receiver is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com