A satellite network terminal security access authentication method, device and system
A satellite network and access authentication technology, applied in the field of satellite communications, can solve problems such as limited satellite resources, complex data transmission, and difficulty in ensuring security strength
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0057] refer to figure 1 , which shows an interactive schematic diagram of a satellite network terminal security access authentication provided in Embodiment 1 of the present invention. In this embodiment, the method includes:
[0058] S101: If the terminal is applying for network access for the first time, generate registration request information, and send the registration request information to the security control center;
[0059] In this embodiment, the registration request information of the terminal includes relevant information that characterizes the identity of the terminal, for example including: terminal device number ID e and terminal verification information info, but the registration request information of the terminal is not limited to these two kinds of information.
[0060] In this embodiment, the channels for the terminal to send the registration request information to the security management and control center may include various channels, such as a satelli...
Embodiment 2
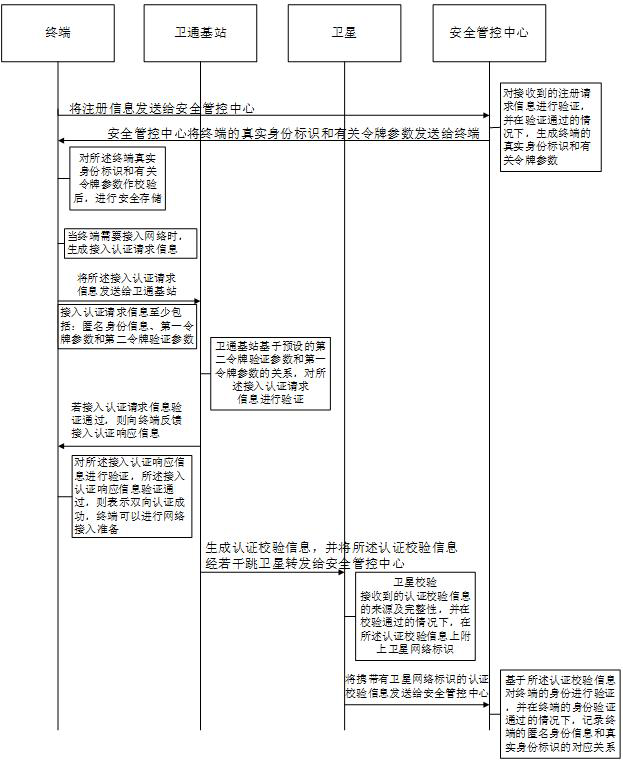
[0151] refer to figure 2 , which shows a schematic flowchart of a satellite network terminal security access authentication method provided in Embodiment 2 of the present invention. In this embodiment, the satellite network system includes:
[0152] Terminals, satellite communication base stations, satellites and security control centers;
[0153] The method includes:
[0154] S201: After the terminal successfully registers with the security management and control center, when the terminal needs to access the satellite network, generate access authentication request information, and send the access authentication request information to the Satcom base station; the access authentication request information is at least Including: anonymous identity information, a first token parameter and a second token verification parameter, wherein the anonymous identity information and the first token parameter are generated according to the real identity of the terminal, and the second to...
Embodiment approach
[0156] In this embodiment, the access authentication request information includes at least anonymous identity information, a first token parameter, and a second token verification parameter, wherein the anonymous identity information can be generated according to the real identity of the terminal. In one embodiment, The real identity of the terminal and the second random number generated by the terminal can be used as parameters for calculating the anonymous identity information, for example, the anonymous identity information can be calculated through the above formula 7). The first token parameter is also calculated based on the real identity. In one embodiment, the first token parameter can be calculated based on the real identity of the terminal, the public parameters of the authentication token, and the validity period corresponding to the public parameters of the authentication token. , for example, the hash operation can be performed on the real identity, public paramete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com