Networking phishing susceptibility prediction method based on eye motion tracking and social worker parts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
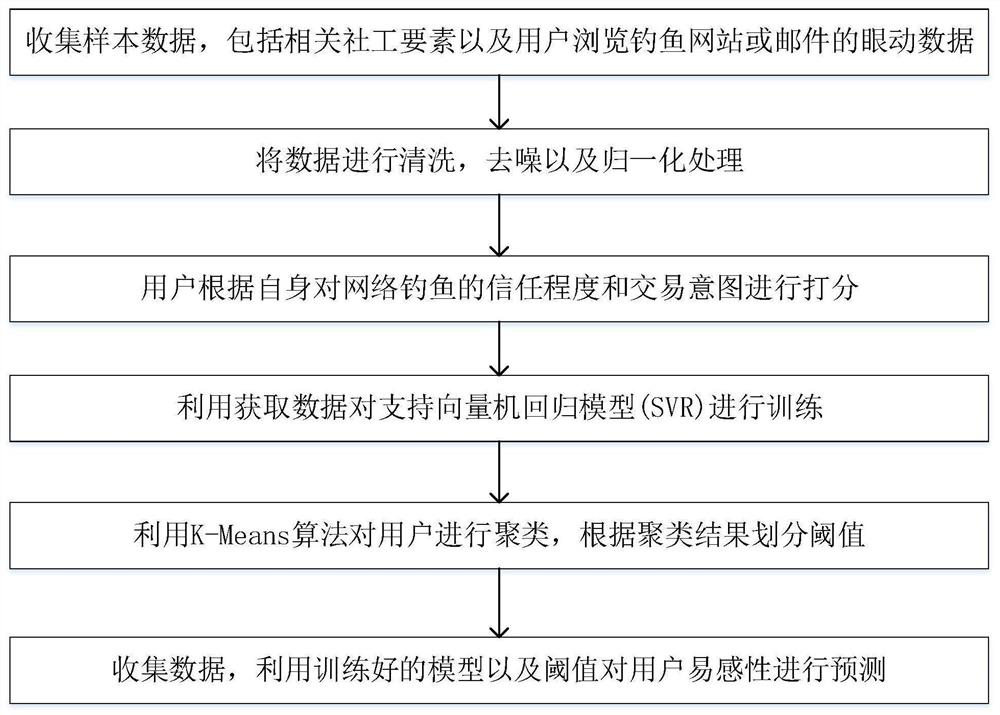
[0063] 1) Information collection
[0064] First, the user’s basic characteristic information is collected in the form of a questionnaire, and the user’s personality information is analyzed according to the Big Five personality scale combined with the survey information. Then quantify the user's experience and knowledge of phishing, and provide an information basis for the subsequent training model.
[0065] Then, provide some phishing attacks to the user, and record the eye movement data of the user while browsing.
[0066] The eye movement data mainly records the user's stay time, gaze times, and return times on the website URL, lock, and browser security indicators such as http / https.
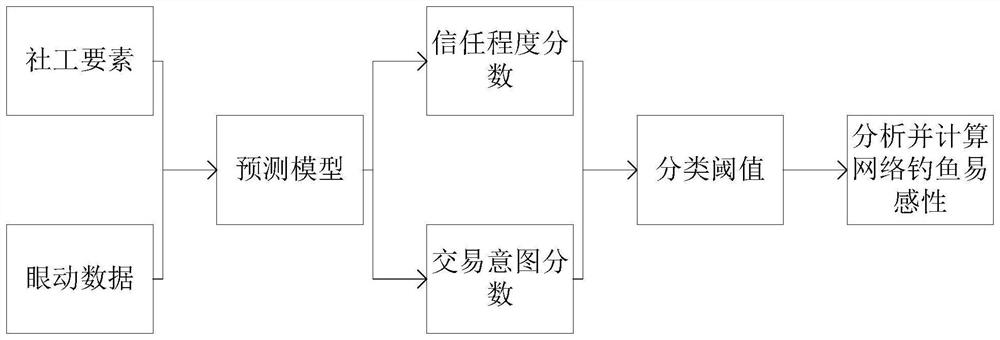
[0067] Finally, users are asked to score the degree of trust in all phishing attacks and their own transaction intentions, with the scores set between 0 and 1.
[0068] 2) Prediction of user trust
[0069] Score and quantify the user trust degree, the score is between 0 and 1; the support ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com