Enterprise network security management method
A security management and enterprise network technology, applied in the field of enterprise network security management, can solve problems such as enterprise network use and enterprise information security risks, lack of system planning and long-term planning, and overall network design is not clear enough to reduce broadcast storms and prevent The effect of illegal device accessing the network and preventing connection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
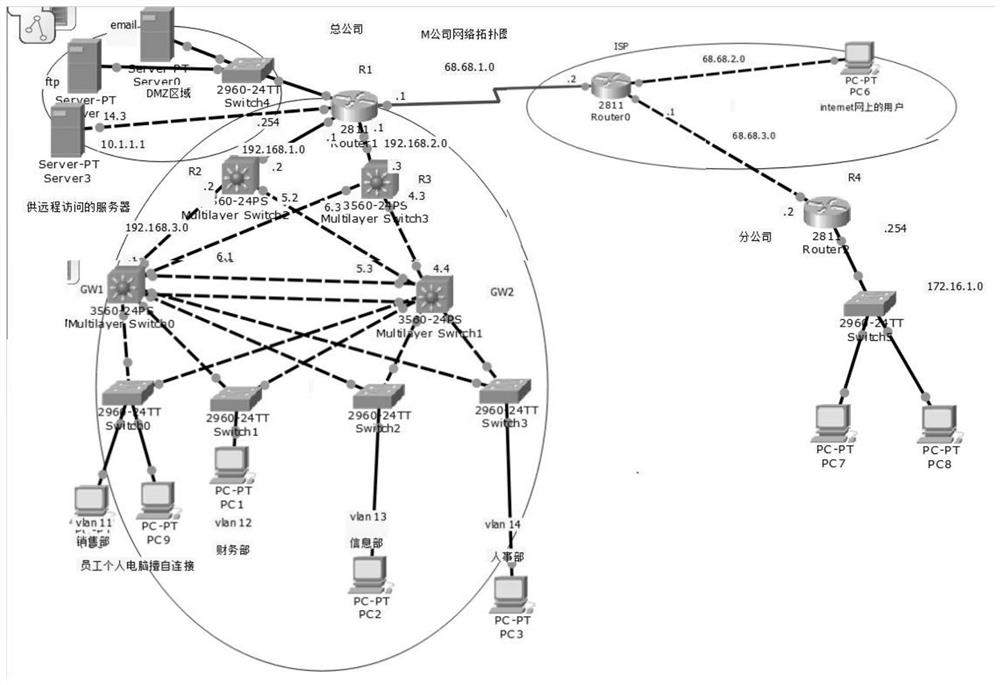
[0033] Embodiment: a kind of enterprise network security management method, comprises constructing DMZ firewall between enterprise network and external network, realizes the function of hiding and access control of real IP, and establishes IPSec VPN between head office and branch office to realize intranet in different areas secure information transmission;
[0034] Among them, the enterprise LAN is connected to the internal trusted port, and port security is configured on the layer 2 switch. The threshold of data packets passing through the port is preset or the MAC address allowed to connect to the switch port is recorded through the MAC address table. At the same time, the PVST spanning tree protocol is adopted. Create a spanning tree for each vlan of the enterprise.
[0035] Such as figure 1 As shown, it is a network topology diagram. Specifically, build a DMZ firewall to realize the function of hiding real IP and access control through address translation and implementin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com