Convergence behavior user identification method and system based on application log
A user identification and user technology, applied in the field of network security, can solve the problems of automatic detection of user convergence behavior and detection technology relying on manual analysis, etc., to achieve the effect of strengthening identification ability building, realizing automatic mining, increasing difficulty and cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
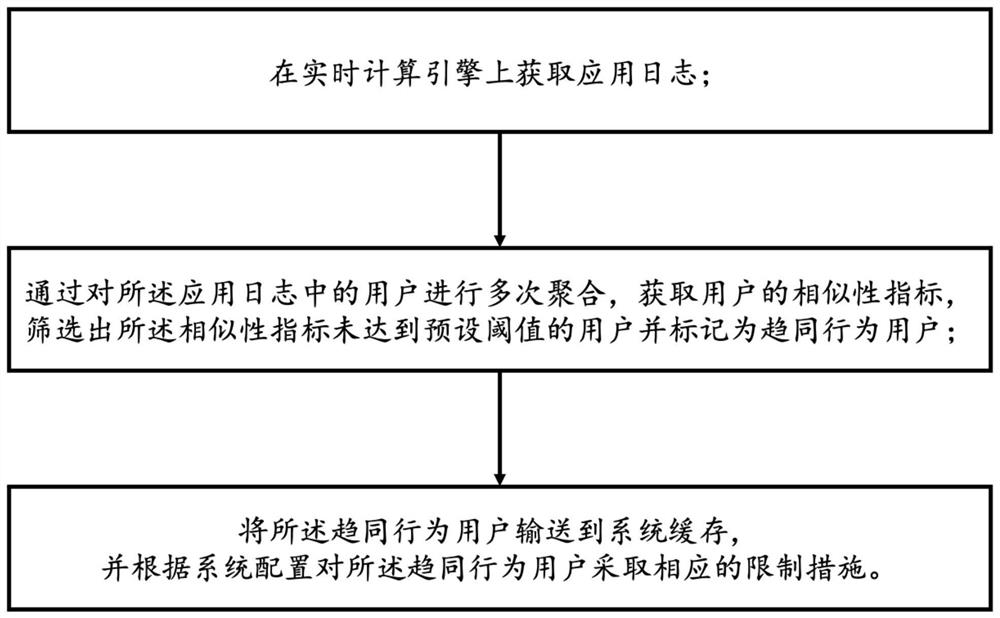
[0051] see figure 1 , a method for identifying users with convergent behavior based on application logs, including:
[0052] Obtain application logs on the real-time computing engine;
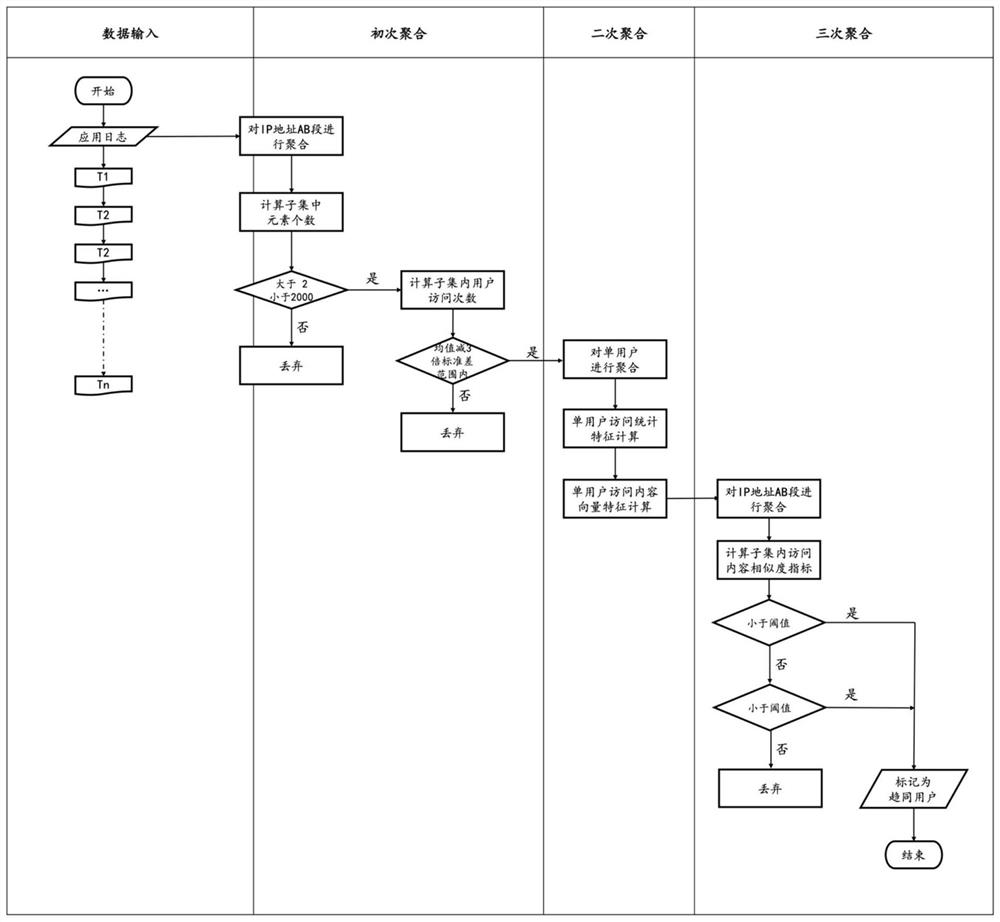
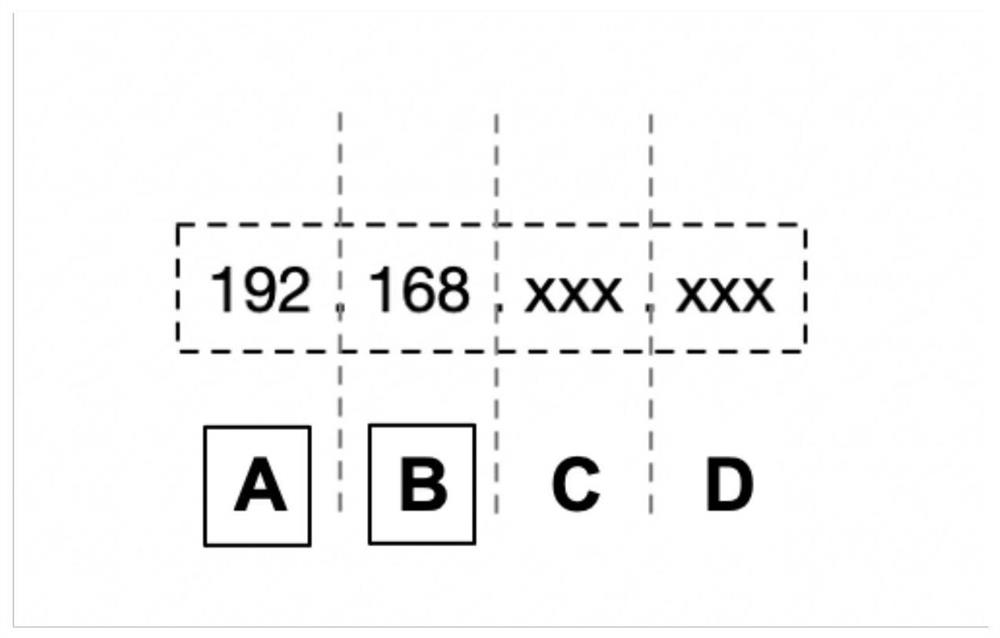
[0053]Through multiple aggregations of users in the application log, the similarity index of the user is obtained, and the users whose similarity index does not reach the preset threshold are screened out and marked as users with similar behaviors;
[0054] Send users with similar behaviors to the system cache, and take corresponding restrictive measures for users with similar behaviors according to the system configuration.
[0055] The method for identifying users with convergent behavior based on application logs provided by the present invention aims at the technical shortcomings of the existing processing methods for convergent behavior, and automatically abstracts and quantifies the access behavior of a single user to effectively reflect the profile of a single user's access behavior. B...
Embodiment 2
[0137] An application log-based convergent behavior user identification system, including an application log acquisition module, an aggregation module, and an output module, wherein: the application log acquisition module is used to obtain application logs on a real-time computing engine; The user is aggregated multiple times to obtain the similarity index of the user, and the user whose similarity index does not reach the preset threshold is screened out and marked as a user with similar behavior; the output module is used to transport the user with similar behavior to the system cache, and according to the system configuration Take corresponding restrictive measures for users with similar behaviors.
[0138] The application log-based convergent behavior user identification system provided by the present invention adopts the application log-based convergent behavior user identification method in the first embodiment above to realize automatic convergent behavior group mining, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com