Cross-site request forgery attack defense method and device, electronic device and storage medium
A cross-site request forgery and business request technology, applied in the field of information security, can solve problems such as poor stability of business requests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
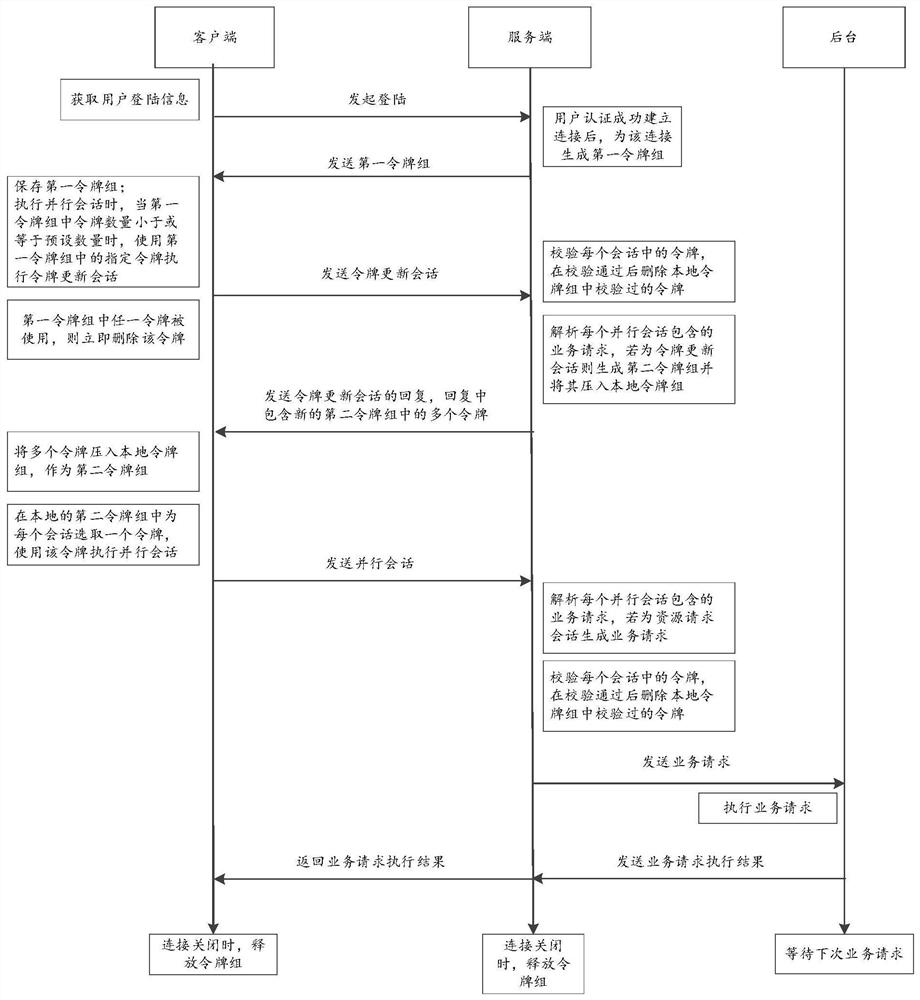
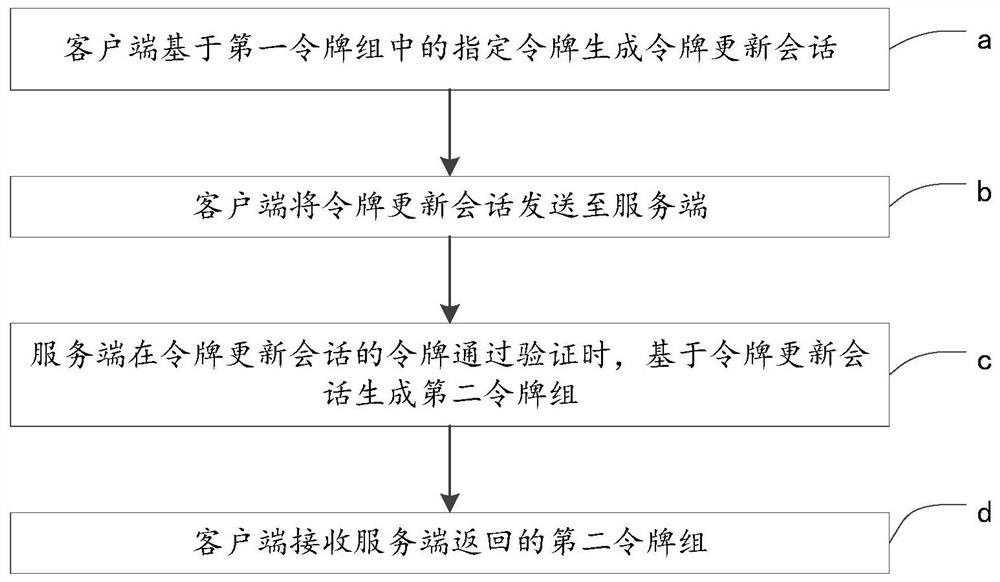
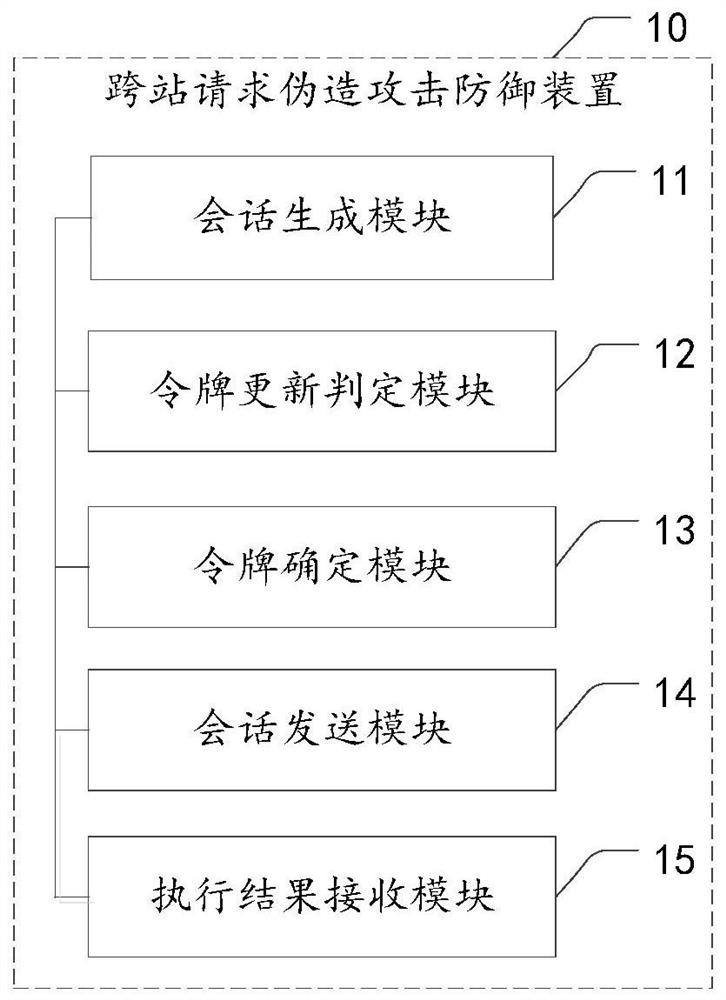
[0046] The technical solutions in the embodiments of the present application will be described below with reference to the drawings in the embodiments of the present application.
[0047] According to the applicant's research, it is found that the existing cross-site request forgery attack defense method uses a one-time valid verification value to be verified by the backend when constructing the request. After the verification is successful, the backend will be the next time Request to assign a new valid check value, and cycle like this. Since the attacker cannot forge the verification value, and the life cycle of the verification value is very short, or the attacker obtains the verification value by intercepting the interaction between the front end and the back end, the verification value has also expired, and the attacker will not be able to pass the website's check. The disadvantage of the prior art is that when any background program of the backend is blocked, the backen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com