A method, apparatus, storage medium and electronic device for detecting slow attack
A slow attack and to-be-detected technology, applied in the field of network security, can solve the problem of inflexible methods for detecting slow attacks, and achieve the effect of precise protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The technical solutions in the embodiments of the present application will be described below with reference to the accompanying drawings in the embodiments of the present application.
[0030] It should be noted that like numerals and letters refer to like items in the following figures, so once an item is defined in one figure, it does not require further definition and explanation in subsequent figures. Meanwhile, in the description of the present application, the terms "first", "second", etc. are only used to distinguish the description, and cannot be understood as indicating or implying relative importance.
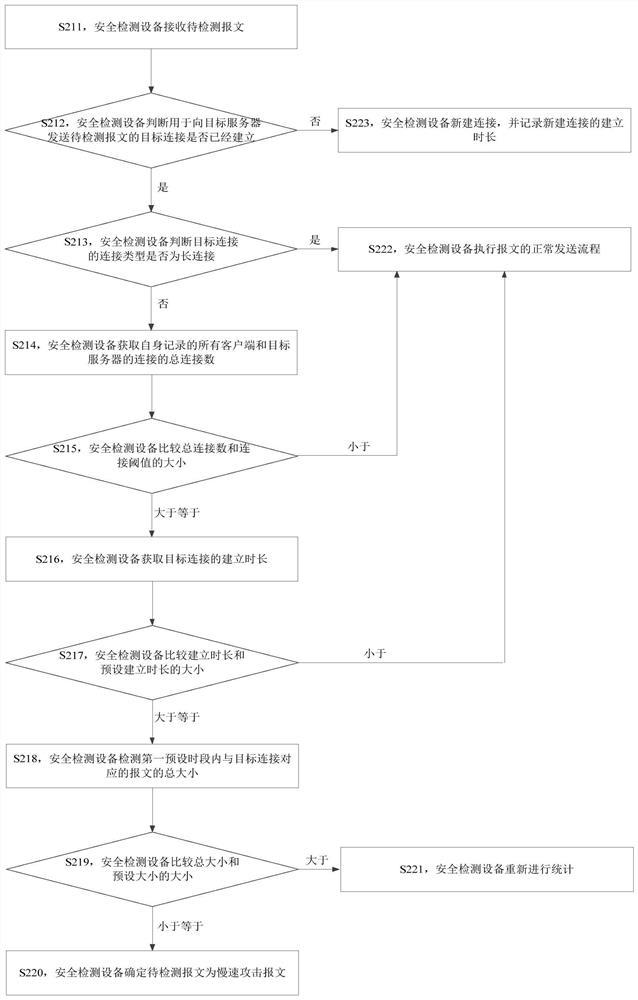
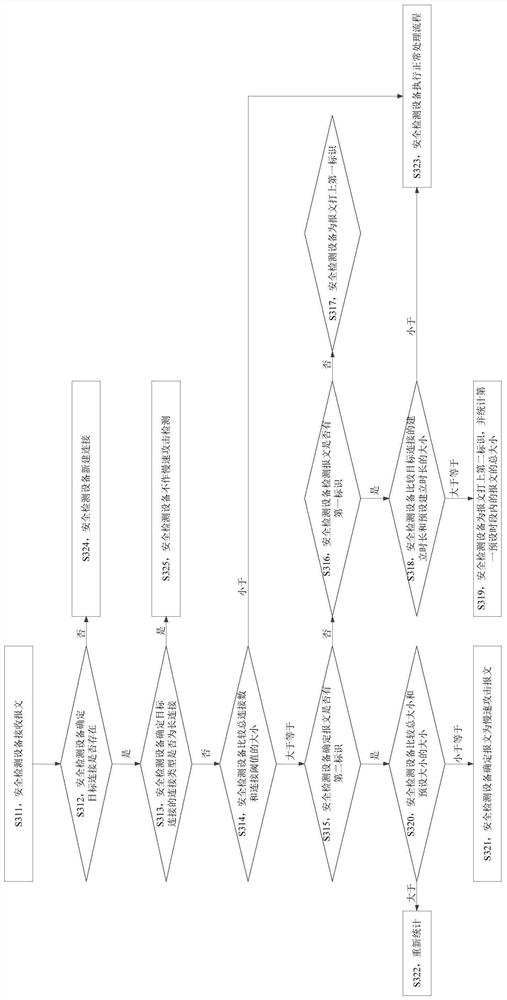
[0031] Existing methods for detecting slow attacks mainly include the following two methods: one is to establish a behavior signature database, and then match the extracted packet features with the behavior signature database. The packet is a slow attack packet, and the packet is discarded; the other is to periodically obtain the number of empty connections on...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com