Method and system for safely accessing specified storage area and medium
A storage area and secure access technology, applied in the field of server data access, can solve the problems of data access lag, consumption of manpower and material resources, time-consuming and laborious, and achieve the effect of ensuring security and reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment 1
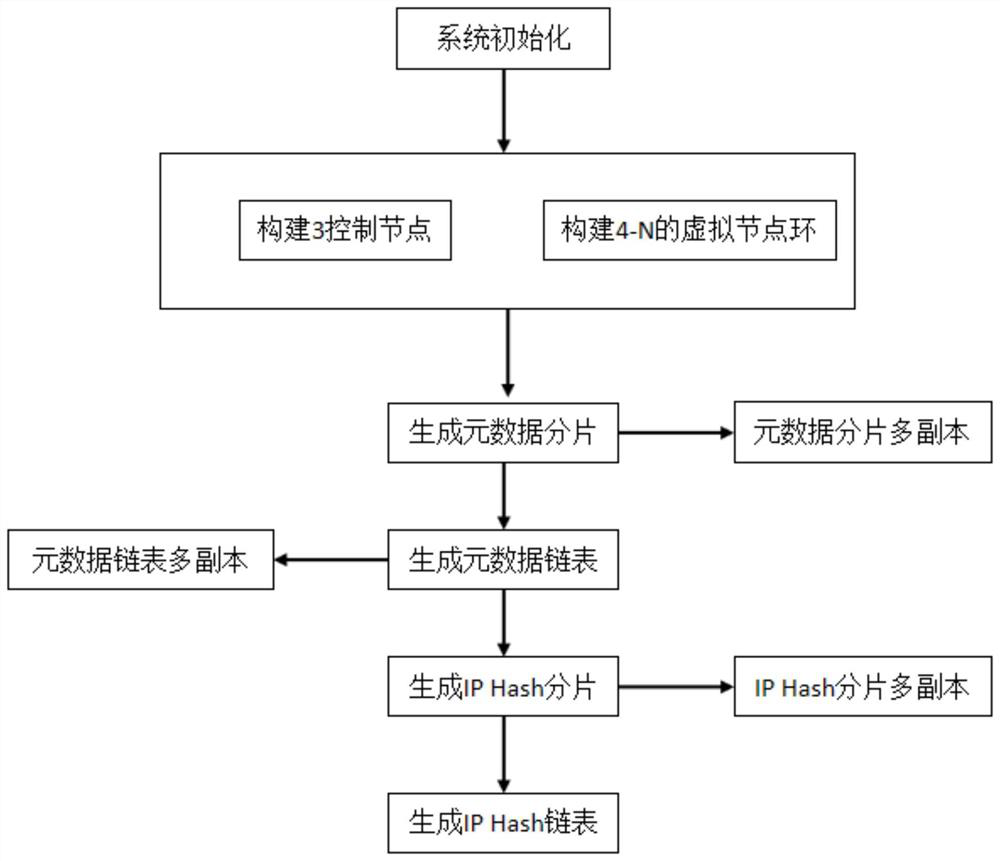
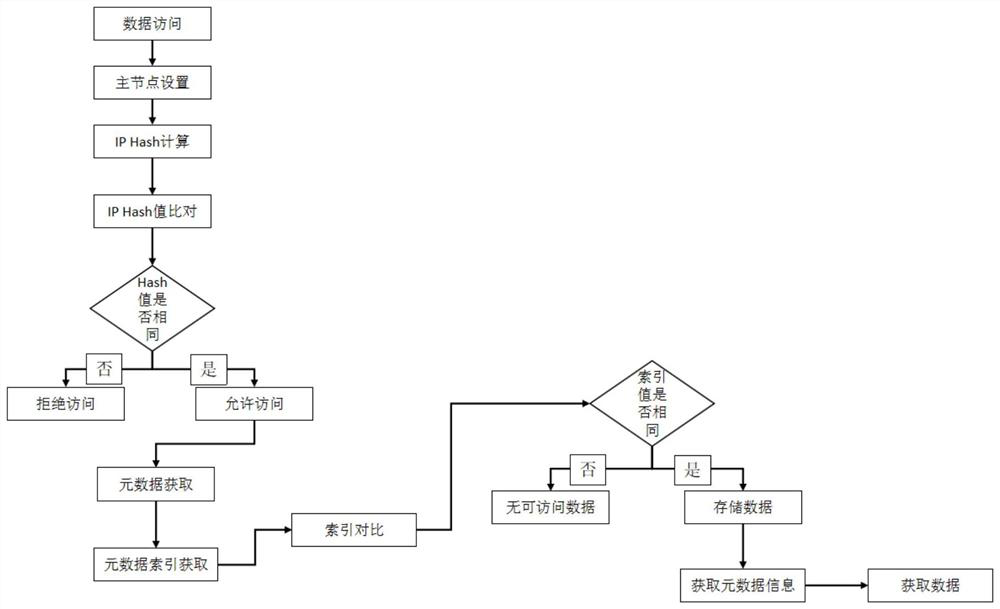
[0036] An embodiment of the present invention provides a method for securely accessing a designated storage area, see figure 1 and figure 2 , including the following steps:
[0037] S11. Firstly, in the first storage cluster, three nodes are selected and deployed as control nodes, and the principle of three copies is adopted, and the contents of the deployment of the three control nodes are consistent.
[0038] S12. The three control nodes are numbered and sorted according to the IP addresses of the nodes, and are divided into No. 1, No. 2 and No. 3. Because No. 1, No. 2 and No. 3 control nodes adopt the principle of three copies, so through No. 1 control node to read Take the / etc / hosts file, because all nodes are connected to each other, and the number of nodes in the first server cluster is set to N, so No. 1 control node reads the IP addresses of the remaining N-3 nodes and calculates them according to the size of the IP addresses Number the remaining nodes as metadata ...
Embodiment 2
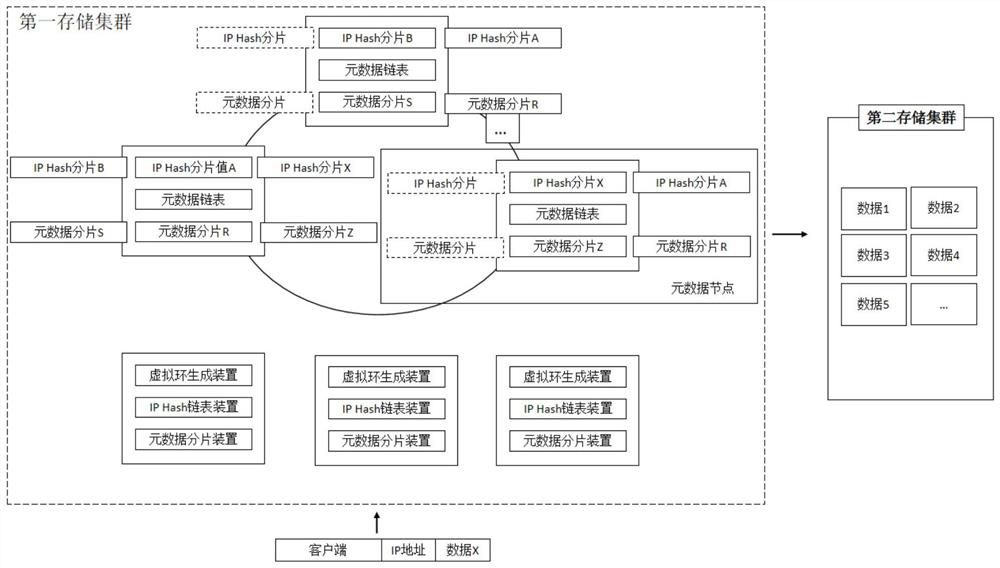
[0046] The embodiment of the present invention also provides a system for safely accessing a designated storage area, please refer to image 3 , including: a virtual ring generation device, an IP hash linked list device, and a metadata fragmentation device;
[0047] The virtual ring generation device is deployed on the three nodes of the first storage cluster. These three nodes are named as the first control node, the second control node and the third control node, and the remaining nodes are named as metadata nodes. The three control nodes The content of the nodes is the same, the / etc / hosts of the three storage nodes save the IP information of the remaining metadata nodes, the three control nodes sort and number the IPs of the remaining nodes in the first storage cluster according to their size, and assign the IP information of the control nodes Connected according to the first number to form a logical node ring, when the logical node ring increases or decreases the metadata...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com