Authority design method and system based on SaaS multi-tenant, equipment and storage medium
A design method and multi-tenant technology, applied in the field of authority management, can solve problems such as the influence of subjective factors, and achieve the effect of easy expansion and maintenance, scientific and reasonable authority allocation method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
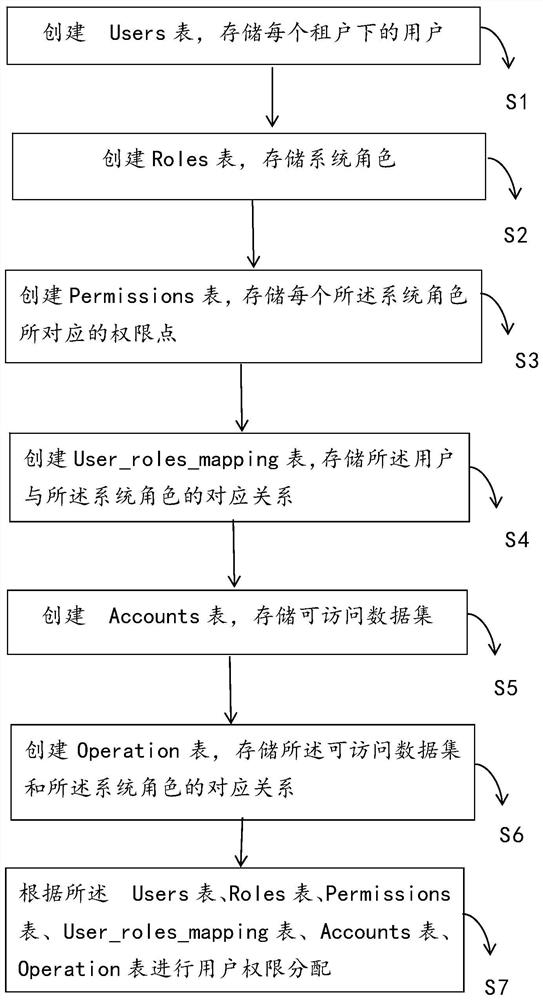
[0053] refer to Figure 1 to Figure 2 As shown, this example discloses a specific implementation of a SaaS multi-tenant-based permission design method (hereinafter referred to as "method").
[0054] Specifically refer to figure 1 and figure 2 As shown, the method disclosed in this embodiment mainly includes the following steps:
[0055] Step S1. Create a Users table to store users under each tenant.
[0056] Specifically, tenants can be understood as customers deployed on the cloud. For example, the school’s one-card management is usually done by a company. The school does not need to do any local deployment, and this company serves many schools. Then the school It is a tenant for the company.
[0057] Specifically, there are three types of SaaS multi-tenant architecture: independent database; shared database, isolated data architecture; shared database, shared data architecture. Independent databases are stored in different databases for different tenants' data; shared ...
Embodiment 2
[0074] In combination with the SaaS multi-tenant-based authority design method disclosed in Embodiment 1, this embodiment discloses a specific implementation example of a SaaS multi-tenant-based authority design system (hereinafter referred to as "system").
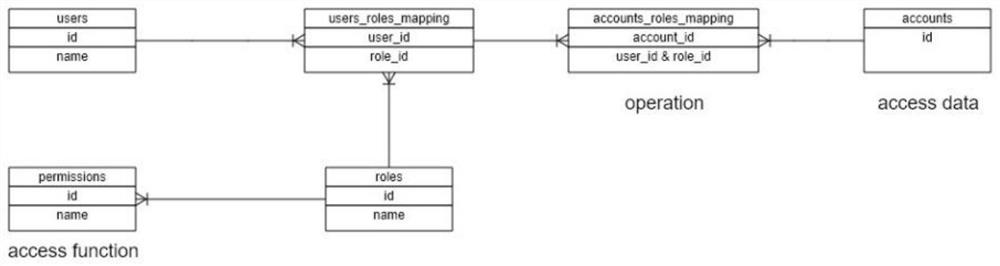
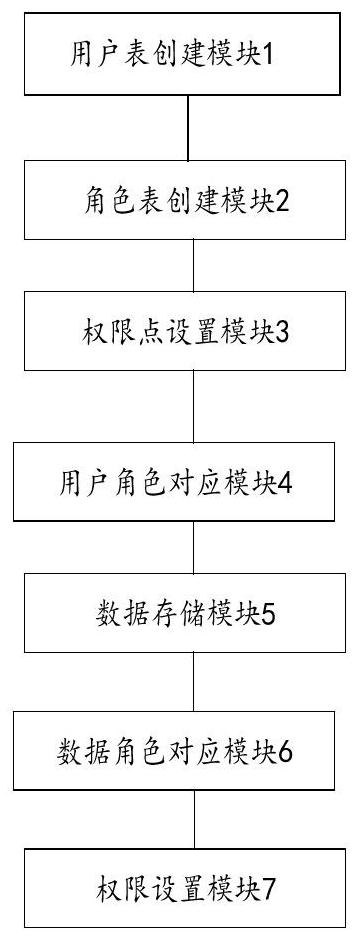
[0075] refer to image 3 As shown, the system includes:
[0076] User table creation module 1, creating a Users table to store users under each tenant;
[0077] Role table creation module 2, creating a Roles table to store system roles;
[0078] Permission point setting module 3, create Permissions table, store the corresponding permission point of each described system role;
[0079] The user role correspondence module 4 creates a User_roles_mapping table to store the correspondence between the user and the system role;
[0080] Data storage module 5, creating an Accounts table to store accessible data sets;
[0081] The data role correspondence module 6 creates an Operation table to store the correspondence between ...
Embodiment 3
[0086] combine Figure 4 As shown, this embodiment discloses a specific implementation manner of a computer device. The computer device may comprise a processor 81 and a memory 82 storing computer program instructions.
[0087] Specifically, the processor 81 may include a central processing unit (CPU), or an Application Specific Integrated Circuit (ASIC for short), or may be configured to implement one or more integrated circuits in the embodiments of the present application.
[0088]Among them, the memory 82 may include mass storage for data or instructions. For example without limitation, the memory 82 may include a hard disk drive (Hard Disk Drive, referred to as HDD), a floppy disk drive, a solid state drive (SolidState Drive, referred to as SSD), flash memory, optical disk, magneto-optical disk, magnetic tape or universal serial bus (Universal Serial Bus, referred to as USB) drive or a combination of two or more of the above. Storage 82 may comprise removable or non-re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com