File security storage and sharing system and implementation method based on hybrid blockchain
A technology of secure storage and sharing system, applied in the field of file security storage and sharing system based on hybrid blockchain, it can solve the problems of network congestion, malicious spread of files, low throughput, etc., to improve the speed and prevent content from being tampered with. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
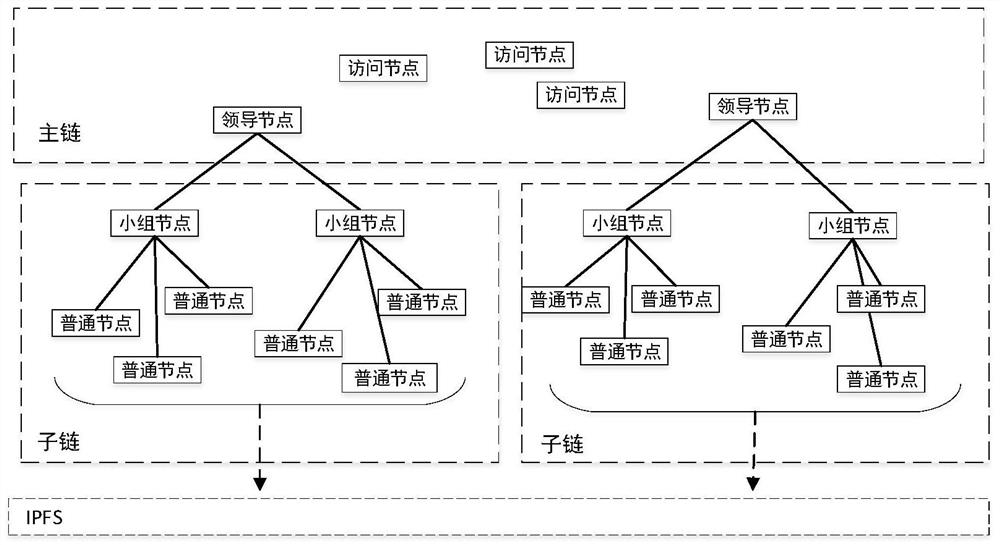
[0068] as attached figure 1 As shown, the hybrid blockchain-based archive security storage and sharing system of the present invention includes,
[0069] Storage layer, the storage layer is used to store shared files and protect the non-tampering of files; the storage layer adopts IPFS;
[0070] The shared layer is used to record the transaction information that occurs, to provide proof for the traceability of the file sharing process, and to automatically perform identity authentication to ensure the secure sharing of files without the participation of a third party; the shared layer includes multiple layers of blocks Chain model and smart contracts on the blockchain;
[0071] The user layer is used to manage, update, view and share files; the user layer consists of participants. Participants include file management agencies, file managers, file owners and file visitors; among them, the file management agency manages the files of multiple file owners, and the file managemen...
Embodiment 2
[0080] The method for realizing the secure storage and sharing of archives based on the hybrid block chain of the present invention is as follows:
[0081] S1. Initialization: Build a multi-layer blockchain model based on Ethereum, initialize a main chain including the participation of leading nodes, and access nodes, group nodes and ordinary nodes to join the main chain through identity authentication;
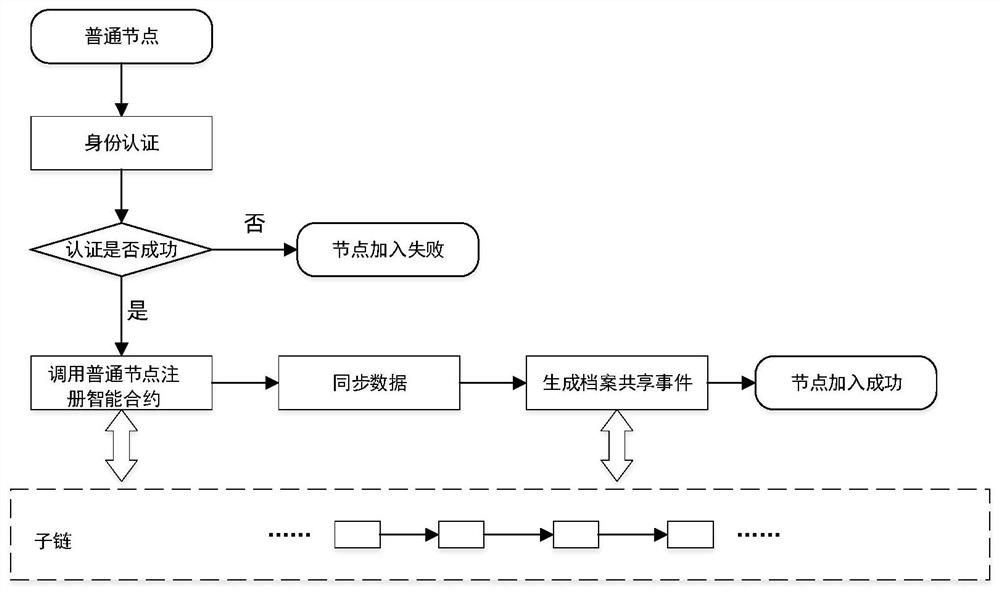
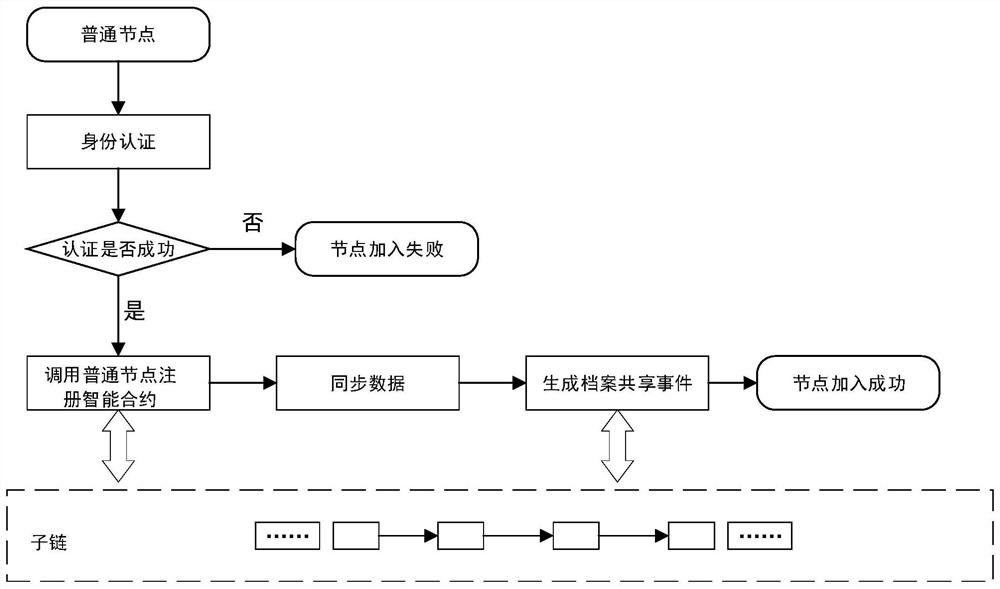
[0082] S2. Identity registration and authentication: The leader node registers and authenticates the group node, access node and ordinary node respectively. After the legal node is successfully registered, it obtains the corresponding node id, joins the corresponding chain, and obtains the private data distributed by Ethereum. key and public key; among them, the private key is stored locally;
[0083] S3. File encrypted storage: first encrypt the file and then store the file to double protect the storage of the file;
[0084] S4. File sharing: The access node sends a file ac...
Embodiment 3
[0113] as attached Figure 5 As shown in the figure, this embodiment takes the student file scene as an example to introduce the entire file sharing process as follows:
[0114] (1) The file access unit issues a visit application;
[0115] (2) Trigger the identity verification smart contract. After the verification is successful, the verification certificate and the access application trigger the leader node license smart contract together;
[0116] (3) After the corresponding leader node (school file management office) agrees, call the master file sharing contract to send the access application, verification certificate, and leader permission to the corresponding group node (the department manager corresponding to the student file) ;
[0117] (4) The access application, verification certificate, and leader Xu trigger the file sharing smart contract on the sub-chain through the group node, and send the information to the corresponding ordinary node (student whose file is acc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com