A method for managing a security program library supporting data storage and an electronic device
A technology of security program and electronic device, which is applied in computer security device, input/output process of data processing, electronic digital data processing, etc., can solve problems such as data destruction and tampering, and achieve the effect of optimizing performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
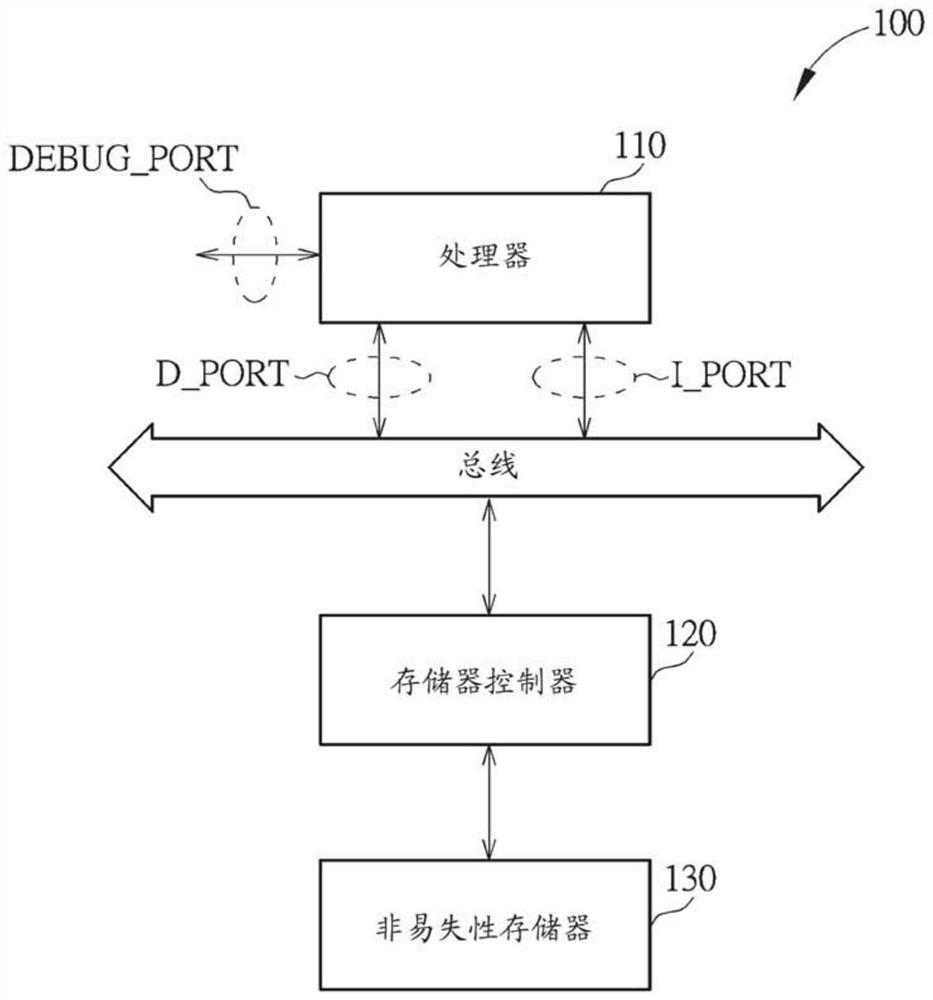
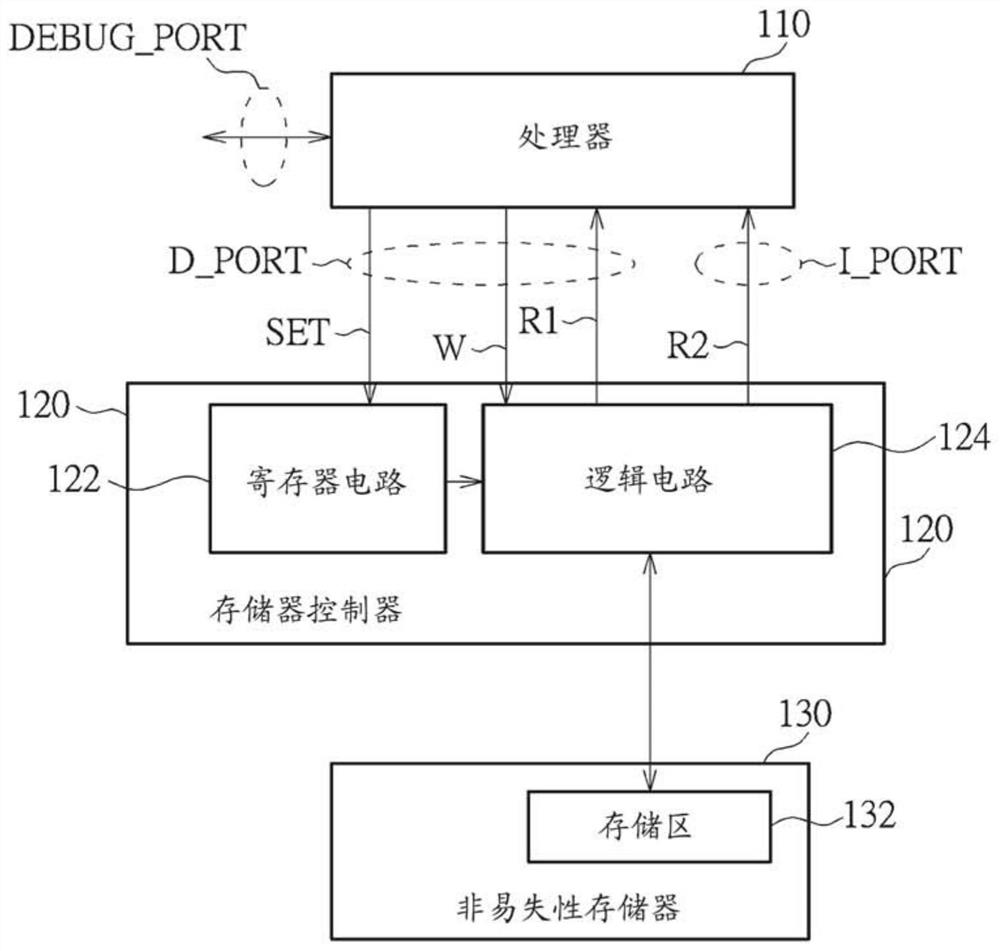
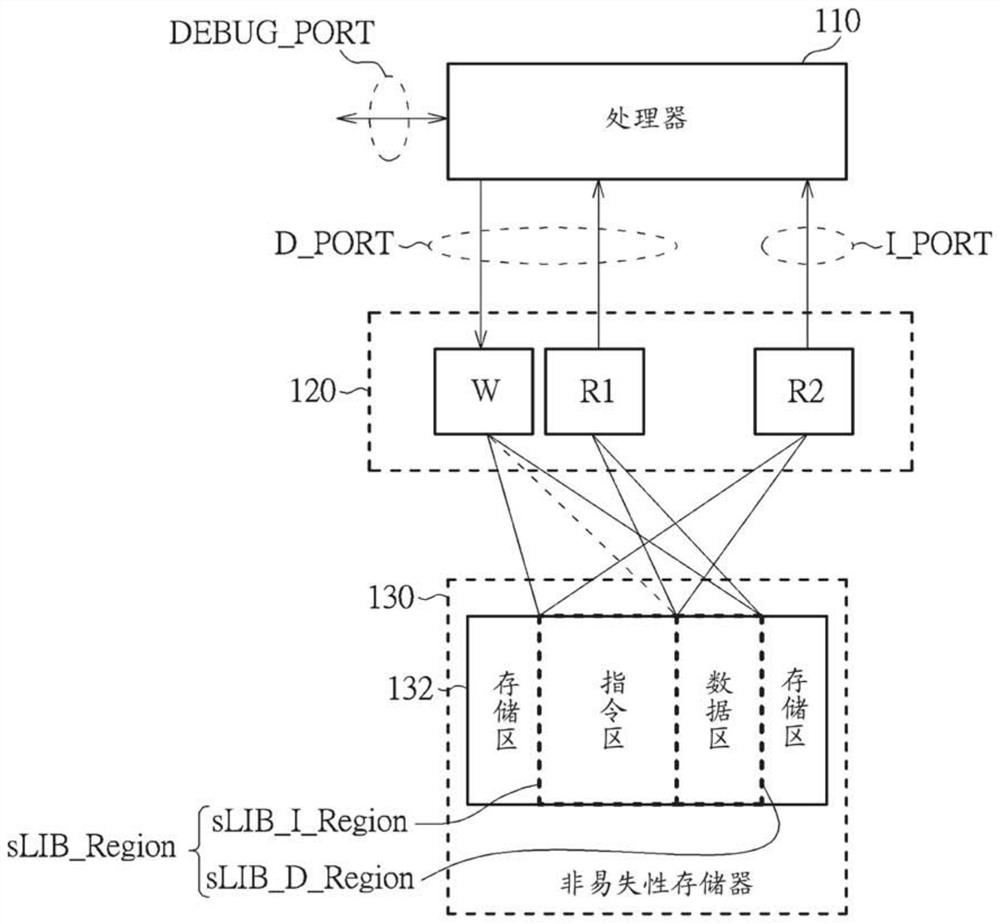
[0031] figure 1 It is a schematic diagram of an electronic device 100 according to an embodiment of the present invention. The electronic device 100 may include at least one processor (for example, one or more processors) such as a processor 110, a memory controller 120, and a non-volatile memory 130, wherein the at least one processor such as the processor 110 may have a A debug port (debug port) DEBUG_PORT, a data port D_PORT and an instruction port I_PORT. For example, the non-volatile memory 130 can be a flash memory (Flash memory), but the invention is not limited thereto. In addition, the memory controller 120 may be coupled to at least one processor such as the processor 110 and the non-volatile memory 130 . In particular, the processor 110 can be coupled to the memory controller 120 through a bus to access the non-volatile memory 130 under the control of the memory controller 120 . based on figure 1 In the architecture shown, the processor 110 can respectively perf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com