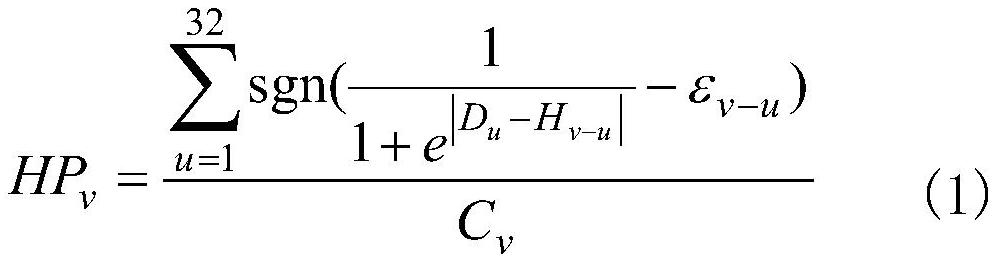An Identity Confirmation Method Based on Overall End-to-End Unsteady Iris Cognitive Recognition
An identity confirmation, non-steady-state technology, applied in the acquisition/recognition of eyes, character and pattern recognition, calculation, etc., to achieve the effect of improving accuracy, reducing the amount of training, and improving the convenience of expansion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
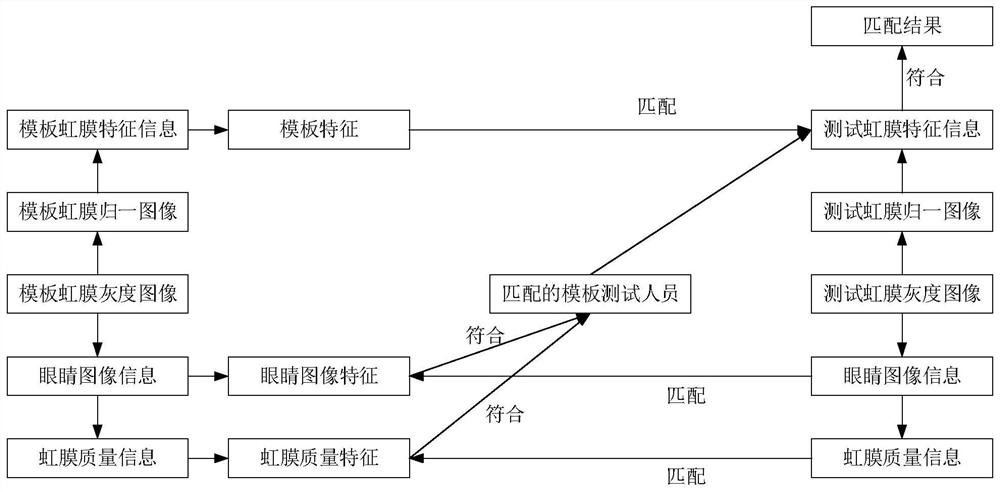
[0116] Under the framework of claim 1, a certain person (named A, the information of A has not been entered before, the test iris and the template iris are collected by the same iris collector, and the computer system has not entered anyone’s information before) The whole process of operation:
[0117]1) Use an iris collector to collect 2000 template iris grayscale images of A.
[0118] 2) The computer system extracts the eye image information of each template iris grayscale image of A, and uses A's 2000 template iris grayscale images to set the characteristics of A's eye image.
[0119] 3) The computer system extracts the iris quality information of each template iris grayscale image of A, and uses A's 2000 template iris grayscale images to set A's iris quality characteristics.
[0120] 4) The computer system converts each template iris grayscale image of A into a 256×32-dimensional template iris normalized image by the Daugman rubber band method.
[0121] 5) The computer s...
Embodiment 2
[0130] Under the framework of claim 1, to six people (named A, B, C, D1, D2, D3, the information of A, B, D1, D2, D3 has not been entered before, but the information of C has been entered, the test iris and The template iris is collected by the same iris collector) The whole process of operation:
[0131] 1) Use an iris collector to collect 2000 template iris grayscale images of A.
[0132] 2) The computer system extracts the eye image information of each template iris grayscale image of A, and uses A's 2000 template iris grayscale images to set the characteristics of A's eye image.
[0133] 3) The computer system extracts the iris quality information of each template iris grayscale image of A, and uses A's 2000 template iris grayscale images to set A's iris quality characteristics.
[0134] 4) The computer system converts each template iris grayscale image of A into a 256×32-dimensional template iris normalized image by the Daugman rubber band method.
[0135] 5) The comput...
Embodiment 3
[0152] Under the framework of claim 1, to six people (named A, B, C, D1, D2, D3, before entering the information of A, C, D1, D2, D3, but not the information of B entering, test iris and The template iris is collected by the same iris collector) The whole process of operation:
[0153] 1) Collect one test iris grayscale image of B.
[0154] 2) The computer system extracts the eye image information of the test iris grayscale image of B.
[0155] 3) The computer system extracts the iris quality information of the test iris grayscale image of B.
[0156] 4) The computer system matches the eye image information and iris quality information of B with the eye image features and iris quality features of A, C, D1, D2, D3 respectively, and extracts the template iris feature information of A, C, and D1.
[0157] 5) The computer system converts the test iris grayscale image of B into a 256×32-dimensional test iris normalized image by the Daugman rubber band method.
[0158] 6) The com...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com