Safe and efficient consensus mechanism implementation method and system
An implementation method and consensus technology, applied in the field of information security, which can solve the problems of high resource consumption, low throughput, and the master node is vulnerable to targeted attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] In order to make the above objects, features and advantages of the present invention more clearly understood, the present invention will be further described below through specific embodiments and accompanying drawings.
[0046] The safe and efficient consensus mechanism implementation method of the present invention includes the following contents:
[0047] 1. Selection of the master node
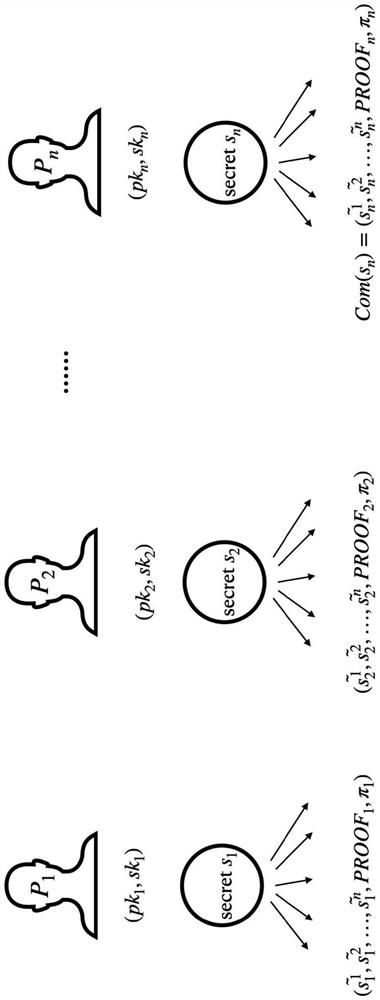
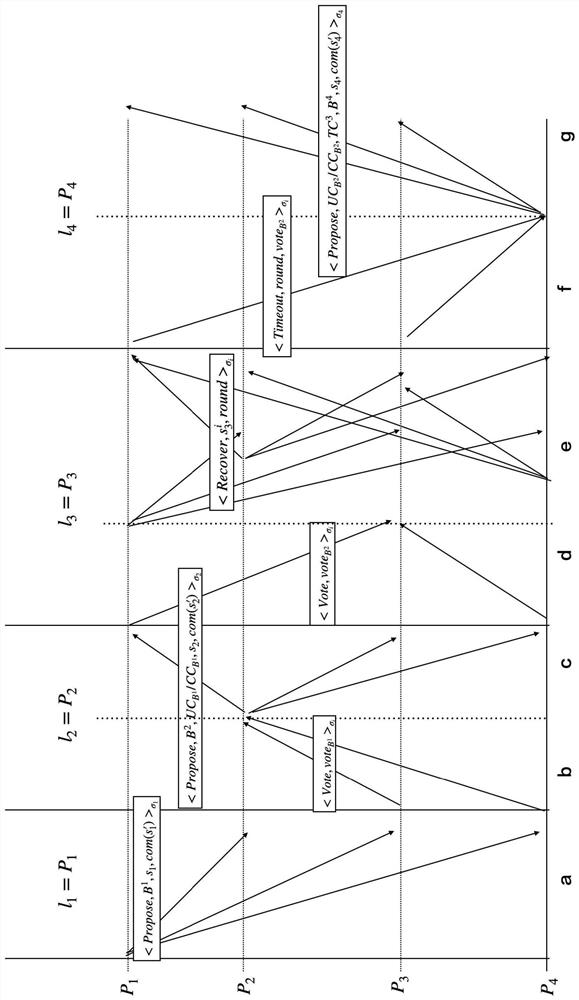
[0048] The publicly verifiable secret sharing PVSS scheme allows nodes to share their secret value s in a set of n = 3f + 1 nodes, so that any subset containing at least t = f + 1 nodes can be recovered. The secret value s, f is the maximum number of malicious nodes allowed. This feature can be well applied to the selection of the master node. When the malicious node does not respond, other nodes can also recover their secret value to calculate the random number of this round and enter a new round. This ensures that the behavior of malicious nodes cannot affect the generation of r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com