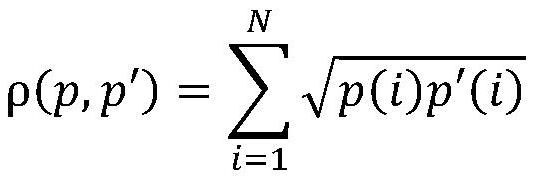Network picture infringement monitoring and automatic evidence obtaining method
A picture and network technology, applied in the direction of network data retrieval, network data indexing, image enhancement, etc., can solve the problems of limited coverage, poor timeliness, high cost, etc., and achieve a large amount of data, convenient evidence collection and storage, and wide coverage Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
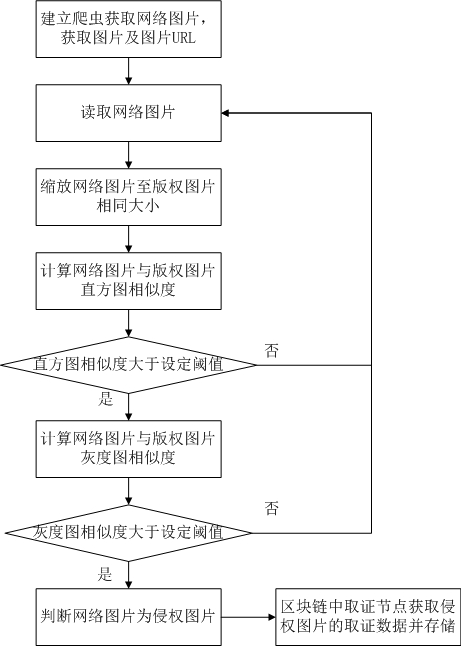
[0066] Such as figure 1 As shown, a network image infringement monitoring and automatic evidence collection system includes the following steps:
[0067] Step A): Obtain the network picture, save the network picture and the URL of the webpage where the network picture is located.
[0068] Create a crawler to crawl webpages on the network, save the URL and code of the webpage, obtain the domain name of the webpage from the URL of the webpage, and include webpages with the same domain name into the same website.
[0069] Classify websites according to their priority. For websites with high average daily visits, websites with high historical infringements, and websites that allow users to upload and display pictures and have high average daily visits as high-priority websites, the crawler crawls and obtains Priority crawling of network pictures. Prioritize sites based on their traffic, history of infringement, and type of interaction:
[0070] Divide the priority into high pri...
Embodiment 2
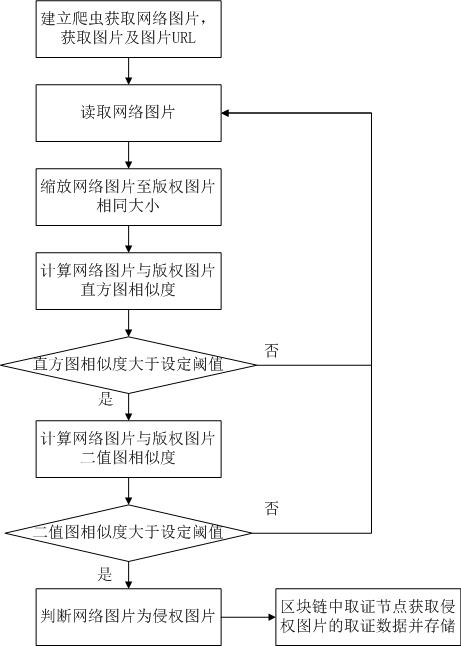
[0096] Such as figure 2 As shown, a network picture infringement monitoring and automatic evidence collection system, step A) and step C) are the same as the first embodiment, and step B) includes the following steps.
[0097] Step B1): Scale the network picture.
[0098] Step B11): preset several preset sizes, and save the copyrighted images registered by the user after being scaled according to the preset sizes.
[0099] Step B12): Read the size of the network picture, and scale the network picture to a preset size closest to its size.
[0100] Step B2): extract the histogram of the network picture, if the similarity between the histogram of the copyright picture and the zoomed network picture histogram is greater than the first set threshold, then determine that the network picture is a suspected infringement picture, and enter step B3), Otherwise, select the next network picture and return to step B1) for execution.
[0101]Calculate the histogram of the copyright imag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com