Verification method and device
A verification method and a verification code technology, which are applied in the field of verification methods and devices, can solve the problems of long time consumption and long time for verifying the receiving end, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
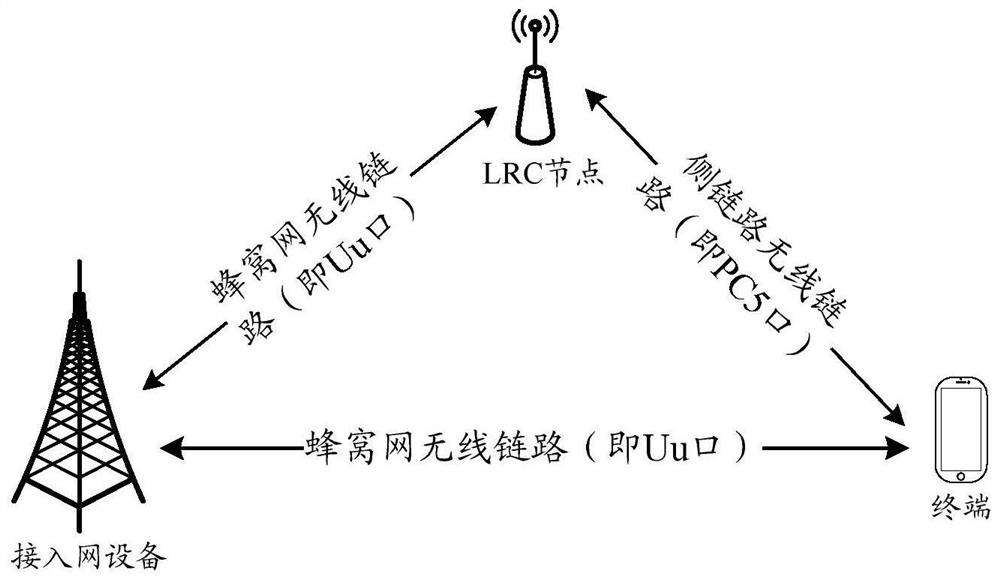
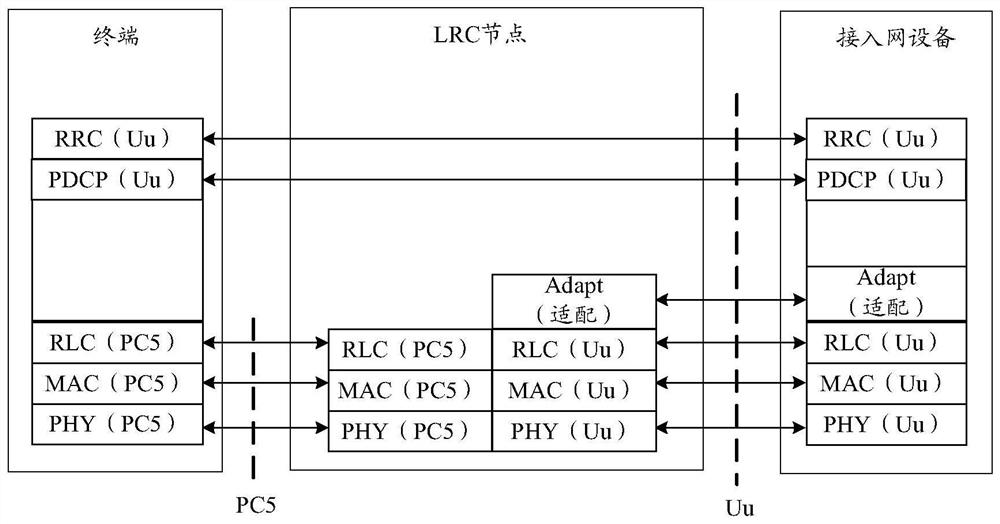
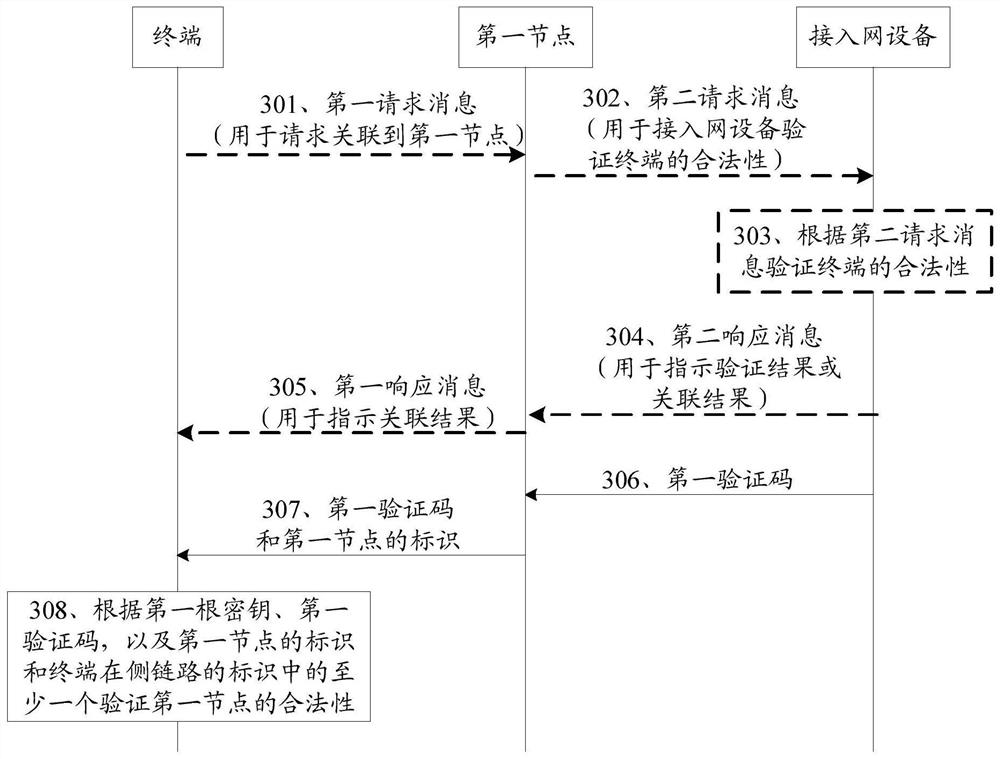
[0120] After the terminal establishes a Uu-RRC connection with the access network device, the core network will authenticate the terminal. After the authentication is successful, a root key (referred to as the first root key) used for communication between the terminal and the access network device will be generated, and the first root key is stored in the terminal and the access network device. Embodiment 1 provides a verification method. In the verification method, the terminal verifies the legitimacy of the first node based on the first root key, and the access network device verifies the validity of the first node based on the first root key or the Uu-RRC sent by the terminal. UE The message verifies the legitimacy of the terminal. Among them, legitimacy can also be called credibility. In each embodiment of the present application, legality may be regarded as credible, and illegality may be regarded as untrustworthy, and details will not be described later.
[0121] Such...
Embodiment 2
[0184] Embodiment 2 provides a verification method. The main differences from the verification method provided in Embodiment 1 include but are not limited to: 1. The verification of the legitimacy of the terminal is no longer performed by the access network device, but by the first node ; 2. The first node's verification of the legitimacy of the terminal and the terminal's verification of the legitimacy of the first node are no longer based on the first root key, but based on the second root key. Wherein, the second root key is a root key used for communication between the terminal and the first node, and the second root key may be generated according to the first root key. For the description related to the first root key, please refer to Embodiment 1, which will not be repeated here.
[0185] Such as Figure 4 As shown, the verification method provided by Embodiment 2 includes:
[0186] 400. The access network device sends the identifier of the side link of the terminal an...
Embodiment 3
[0229] This embodiment provides a verification method, and the verification process of the legitimacy of the first node is the same as the verification process of the legitimacy of the first node in Embodiment 2. There are three ways to implement the verification of the validity of the terminal, and two of the three ways are the same as the ways 1 and 2 in the first embodiment. Such as Figure 5 As shown, the verification method provided by Embodiment 3 is specifically described below, and the verification method includes:
[0230] 501. It is the same as step 402 above.
[0231] 502, the same as the above step 301.
[0232] 503, the same as step 302 above.
[0233] 504, the same as the above step 303.
[0234] 505. Same as step 304 above.
[0235] 506. Same as step 305 above.
[0236] There are three ways to implement the verification of the legitimacy of the terminal in steps 502 to 506 . The first implementation manner among the three implementation manners is the sam...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com