CentOS high-interaction honeypot system based on Docker and implementation method thereof
A high-interaction, honeypot technology, applied in the field of Docker-based CentOS high-interaction honeypot system, can solve the problems of less research, low hacker interaction, and difficult to distinguish operations.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
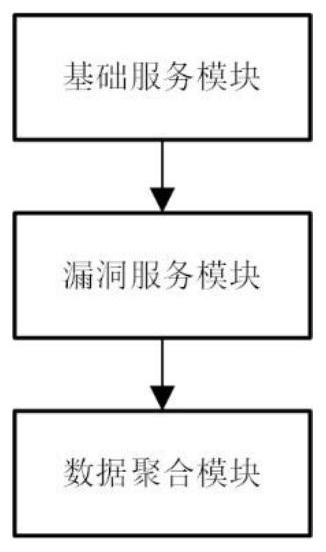
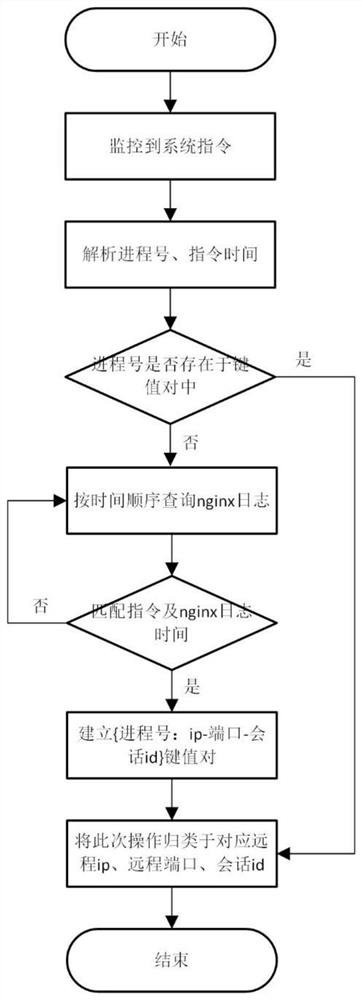
[0024] Such as figure 1 As shown, a Docker-based CentOS high-interaction honeypot system includes:
[0025] Basic service module: Based on the basic CentOS image, a large number of other basic services are deployed to simulate the operating environment of the real host to achieve a high interaction effect. While deceiving the attacker to invade, it increases its own concealment and enables the attacker to stay longer in the system. Long time and not easy to find itself a honeypot. Specifically, it provides basic CentOS services. Mainly, using the convenient deployment feature of Docker, you can freely and effectively configure various services in the honeypot system, increase service categories, and improve the interaction between honeypots and hackers. First use Docker to pull the basic centos7 image as the basic image of this embodiment. After that, all kinds of basic services and vulnerability services are deployed based on this basic image, and various services are instal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com