Private data identification and processing method and device, equipment and readable medium
A technology of privacy data and identification method, which is applied in the computer field and can solve problems such as privacy data leakage, personal and public security issues, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
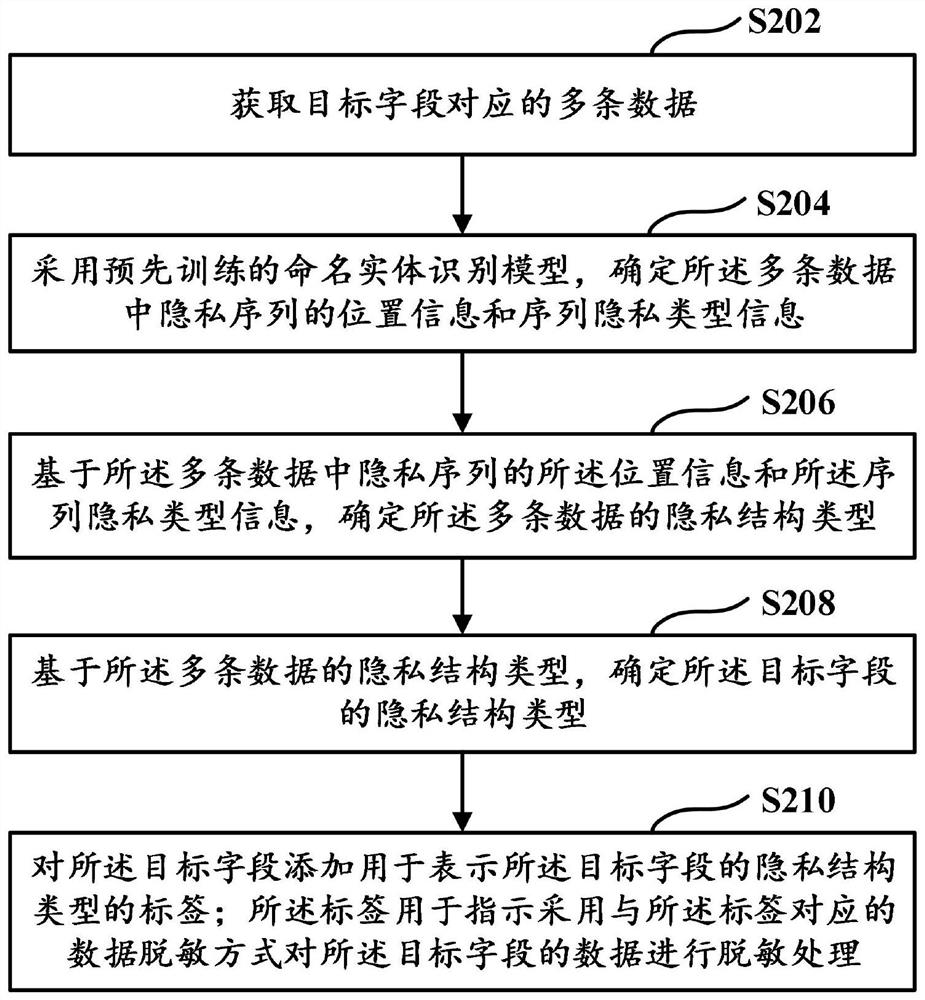
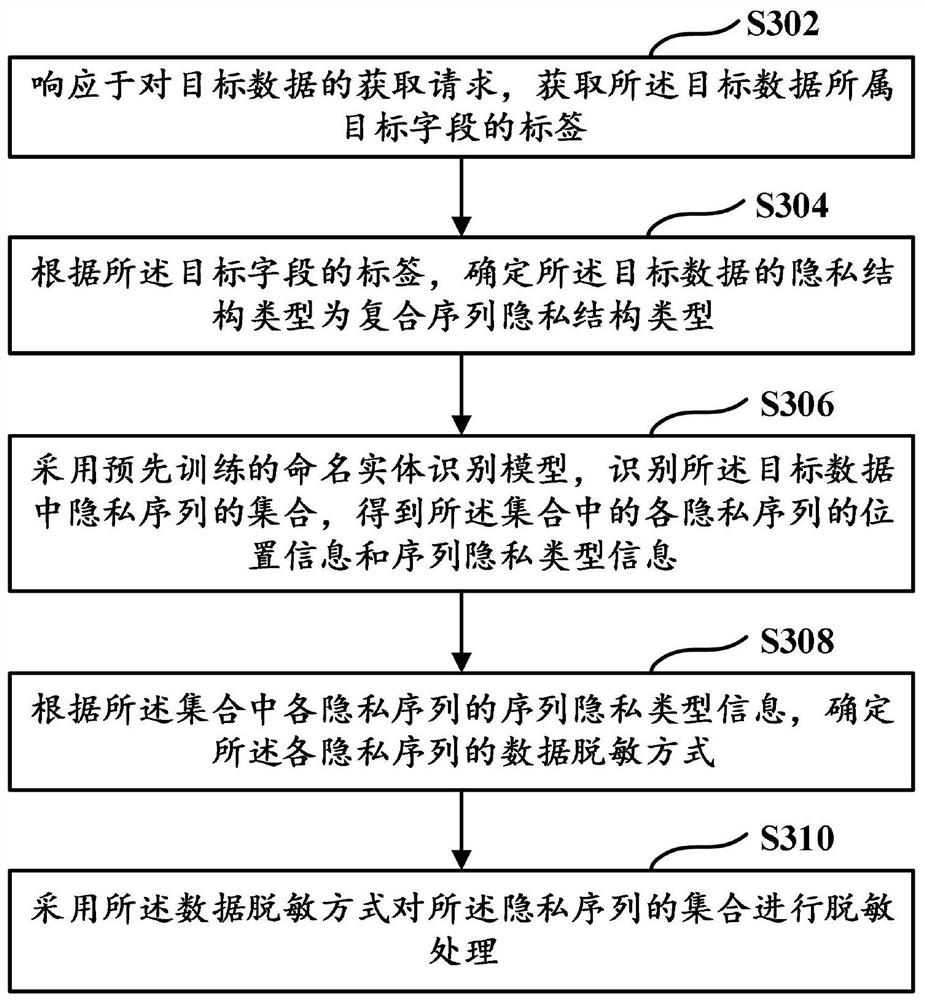
[0032] Privacy data protection can be roughly divided into two parts. First, it is necessary to identify potential private data from the massive data table, and then use various methods to encrypt the identified private data to effectively prevent the leakage of private data. It can be seen that how to effectively identify potential private data from massive data is a prerequisite for privacy data protection. For this reason, it is necessary to provide a method capable of identifying private data.
[0033] The storage form of data can include structured form, semi-structured form or unstructured form. Structured data can be represented and stored in a relational database, in a two-dimensional form, such as data in relational databases and object-oriented databases. Semi-structured data contains related tags to separate semantic elements and layer records and fields. Common semi-structured data, such as XML, JSON, HTML, etc. Unstructured data may be data without a fixed structur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com