Resource calling method, resource calling device, client and business server
A client and server technology, applied in the Internet field, can solve problems such as increasing the complexity of business server design
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
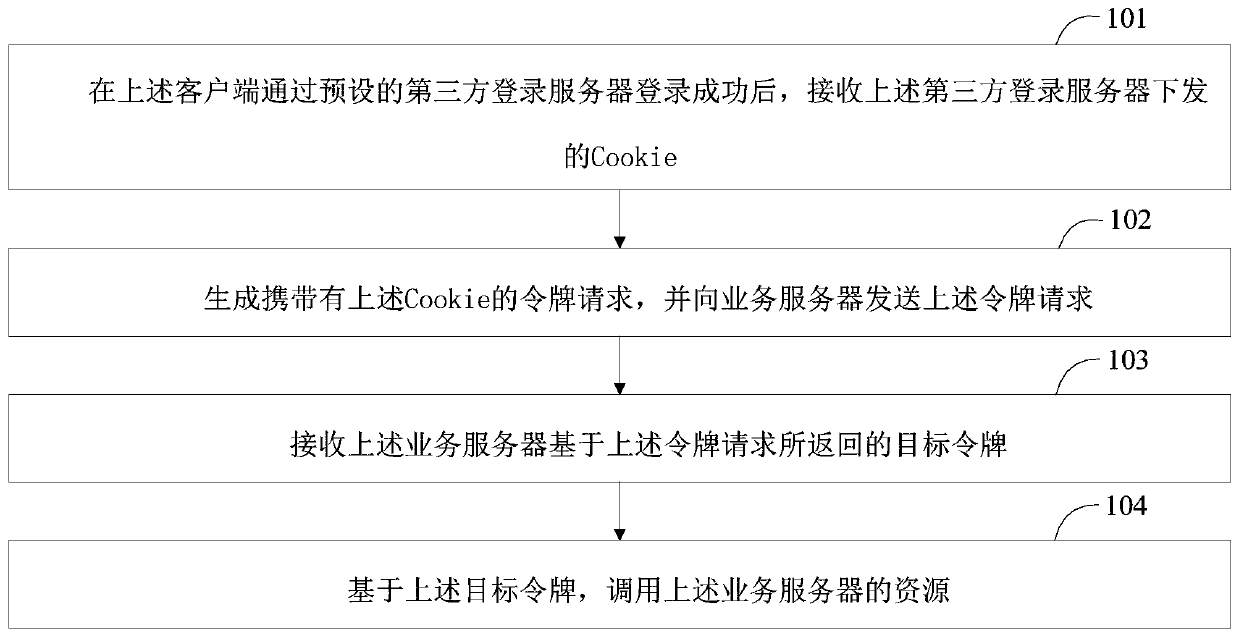
[0047] A resource calling method provided by the embodiment of the present application is described below, wherein the resource calling method provided by the embodiment of the present application is applied to the client, please refer to figure 1 , the resource calling method includes:
[0048]Step 101, after the above-mentioned client successfully logs in through the preset third-party login server, receiving the cookie issued by the above-mentioned third-party login server;
[0049] In this embodiment of the application, the business system can be integrated with a third-party login system, wherein the business system corresponds to a business server, which is used to provide various resources of the business system; the third-party login system corresponds to a third-party login server, The third-party login server is used to provide a third-party login function for the business system. In this way, when the client logs in to the business system, it can log in through the...
Embodiment 2
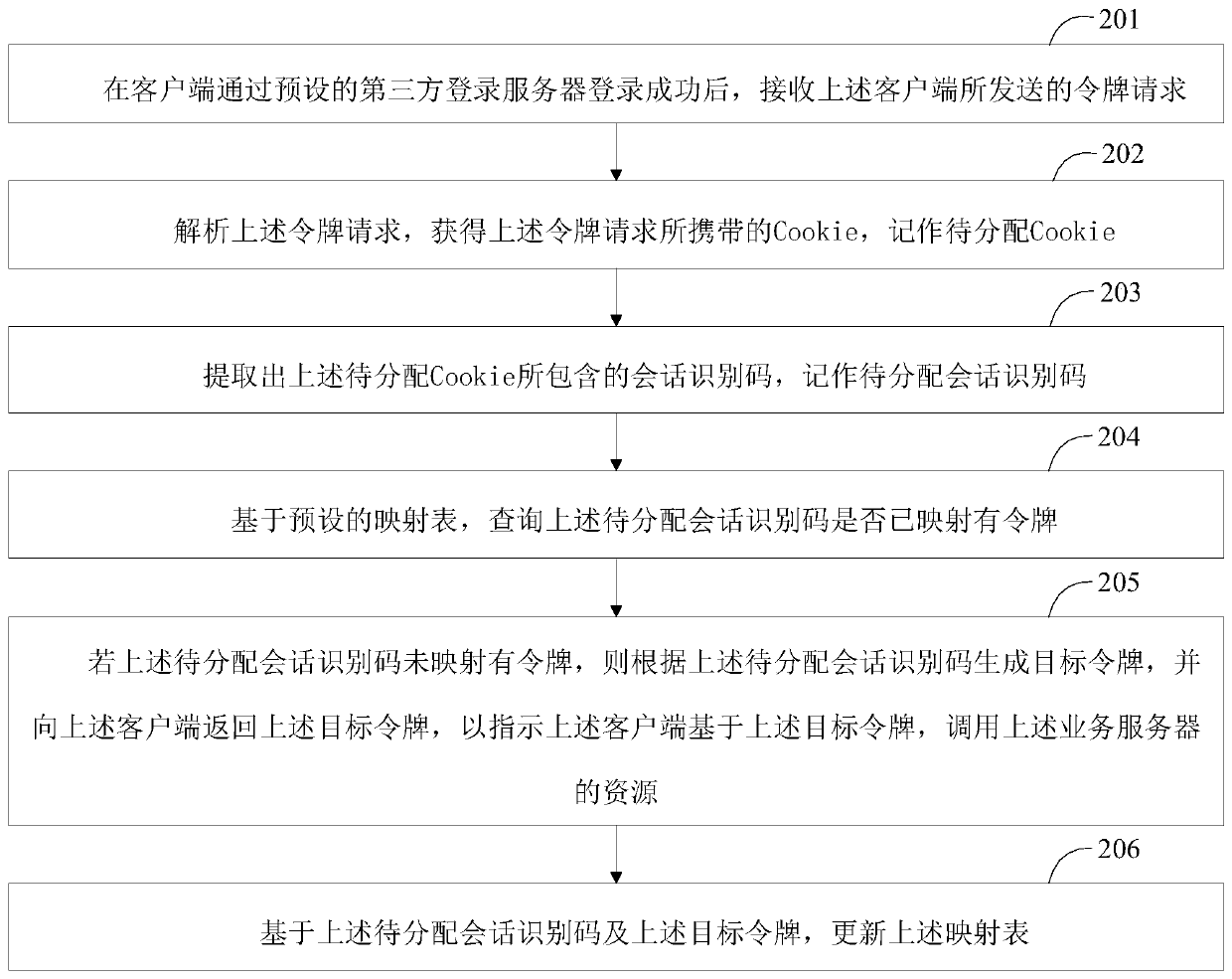
[0061] A resource calling method provided by the embodiment of the present application is described below, wherein the resource calling method provided by the embodiment of the present application is applied to the service server, please refer to figure 2 , the resource calling method includes:
[0062] Step 201, after the client successfully logs in through the preset third-party login server, receive the token request sent by the client;
[0063] In this embodiment of the application, the business system may be integrated with a third-party login system, so that when the client logs in to the business system, it logs in through the third-party login server corresponding to the above-mentioned third-party login system. After the above-mentioned client successfully logs in through the above-mentioned third-party login server, the above-mentioned third-party login server can notify the above-mentioned client to jump to the page of the above-mentioned business system, and the a...
Embodiment 3
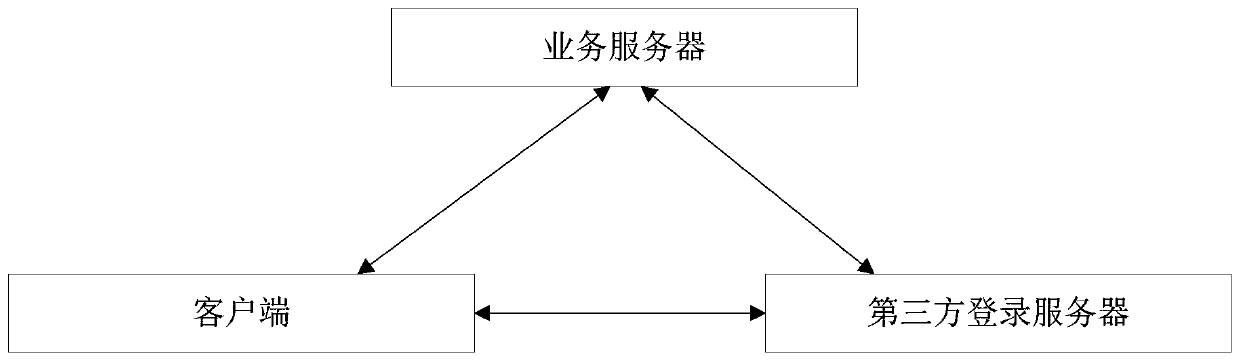
[0086] A resource calling method provided by the embodiment of the present application is described below, wherein the resource calling method provided by the embodiment of the present application is applied to the resource calling system, please refer to image 3 , the resource call system is composed of a third-party login server, a client and a business server, and there is data interaction between the third-party login server and the client, between the third-party login server and the business server, and between the client and the business server. see Figure 4 , Figure 4 An example of the interaction process between the client, the business server and the third-party login server is given:
[0087] First, the client (that is, the real user) sends a login request to the third-party login system, which contains the user name and password; the third-party login server verifies the user name and password; if the user name and password are verified successfully, Then assi...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap