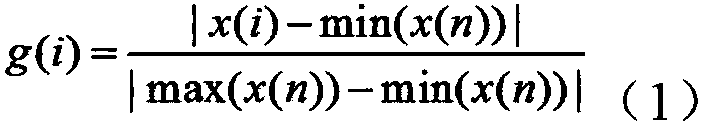User load electricity stealing model mining system and method based on complex user behavior analysis
A technology of behavior analysis and model mining, applied in information technology support systems, electronic digital data processing, character and pattern recognition, etc., can solve problems such as consuming manpower and material resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0096] In order to deepen the understanding of the present invention, the present invention will be further described below in conjunction with examples, which are only used to explain the present invention and do not constitute a limitation to the protection scope of the present invention.
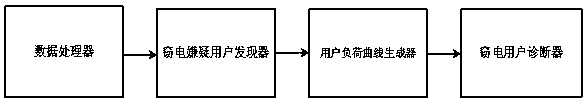
[0097] Such as Figure 1-2 As shown, this example provides a user load stealing power model mining system based on complex user behavior analysis, including a data processor, a power stealing suspect user discoverer, a user load curve generator and a power stealing user diagnostic device, the data The processor is connected with the electricity-stealing suspected user finder, the electricity-stealing suspected user finder is connected with the user load curve generator, and the user load curve generator is connected with the electricity-stealing user diagnostic device.
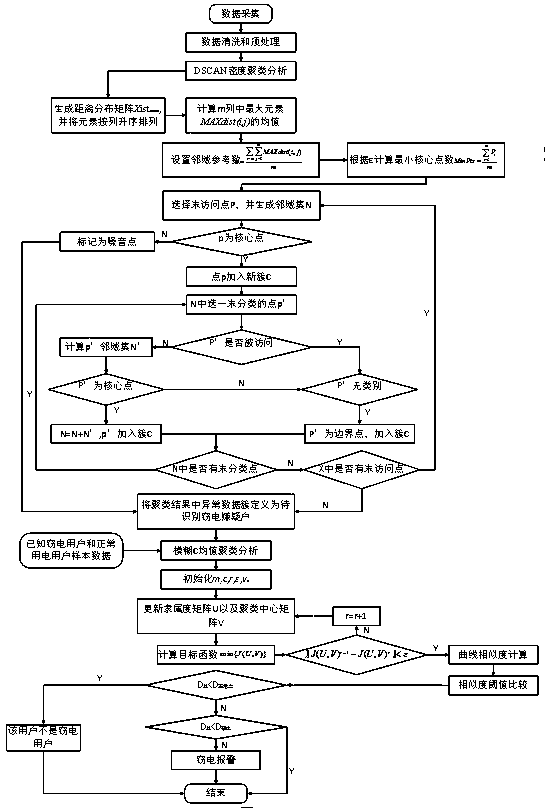
[0098] This example also provides a method for mining electricity stealing model of user load based on complex user beh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com