Cipher machine with secret key destroying function and secret key destroying method
A cipher machine and key technology, applied in the field of information security, can solve problems such as the inability to guarantee the timeliness of key destruction, key security risks, etc., to prevent violent opening or cracking, protect key security, and have a high success rate Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The scheme will be described below in conjunction with the accompanying drawings and specific implementation methods.
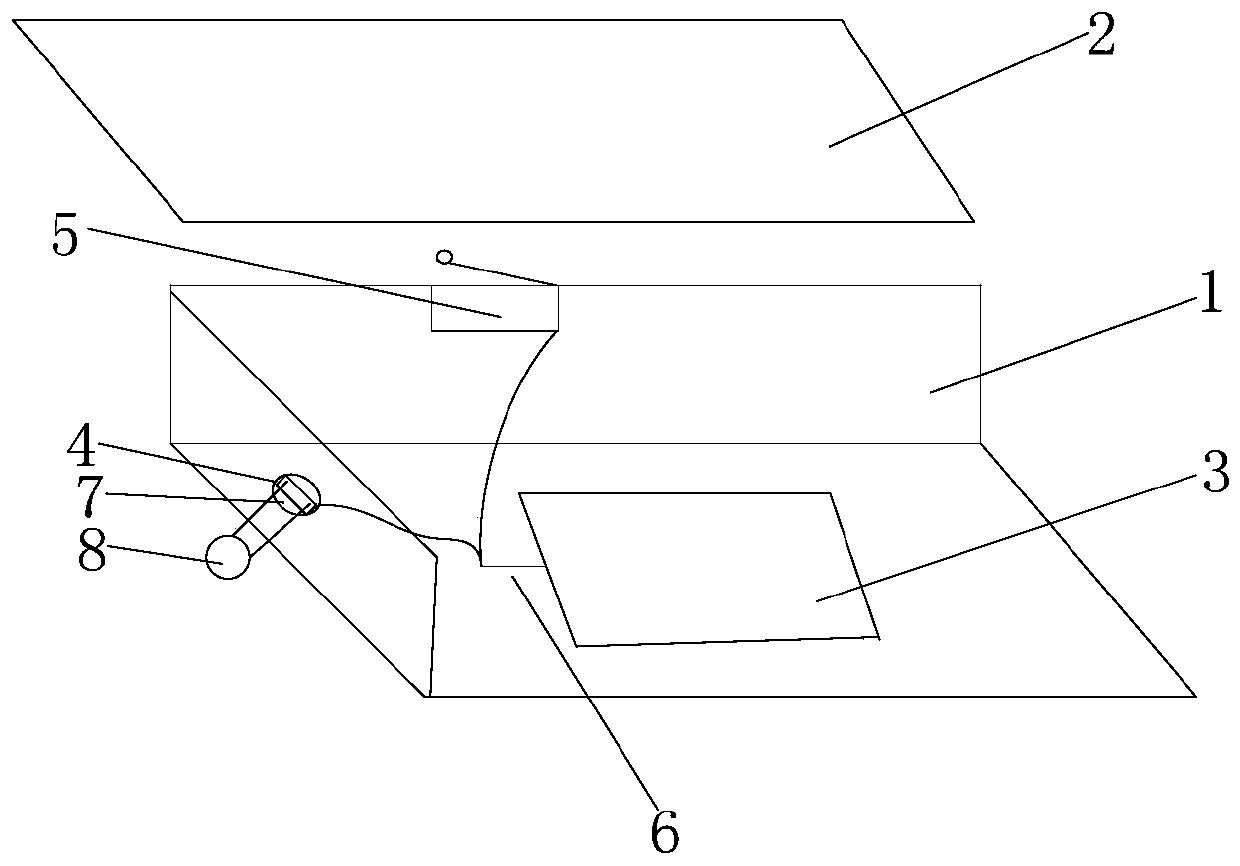
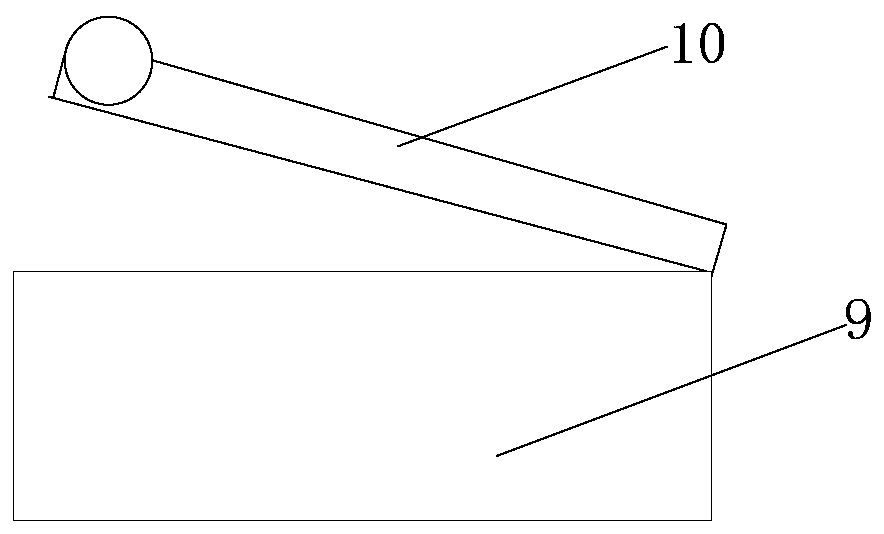
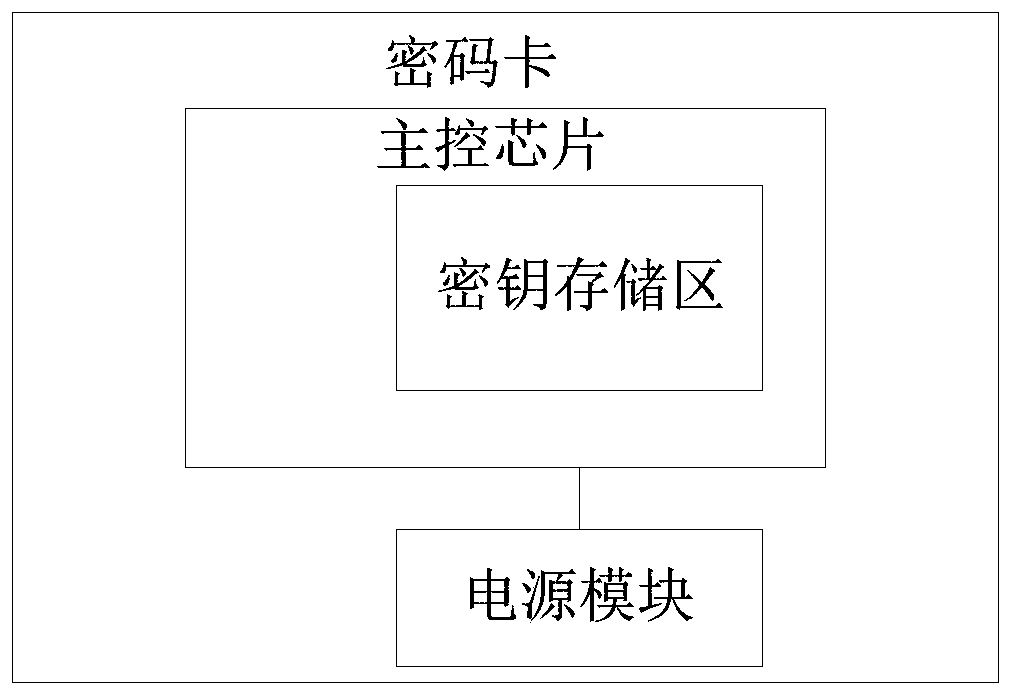
[0024] figure 1 For a schematic structural diagram of a cryptographic machine with key destruction provided in the embodiment of this application, see figure 1 , the cipher machine with key destruction in this embodiment includes a cipher machine housing 1 and a cover plate 2, the cipher machine housing 1 and the cover plate 2 are movably connected, and the cipher machine housing 1 is provided with A cipher card 3, the cipher card 3 is configured to trigger key destruction at a low level, a first control switch 4 is arranged on the cipher machine housing 1, and the cipher machine housing 1 is packaged with the cover plate 2 A second control switch 5 is arranged at the place, and the first control switch 4 and the second control switch 5 are electrically connected with the password card 3 through a connecting wire, and control the first control switch ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com