A data encryption storage method for mimic defense system
A data encryption and defense system technology, applied in digital data protection, electrical digital data processing, instruments, etc., can solve problems such as the inability to defend against data storage security issues, and achieve the goal of ensuring non-tampering, increasing difficulty, and improving data security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to make the objectives, technical solutions and advantages of the embodiments of the present invention clearer, the technical solutions of the present invention will be described clearly and completely below with reference to the accompanying drawings of the present invention.
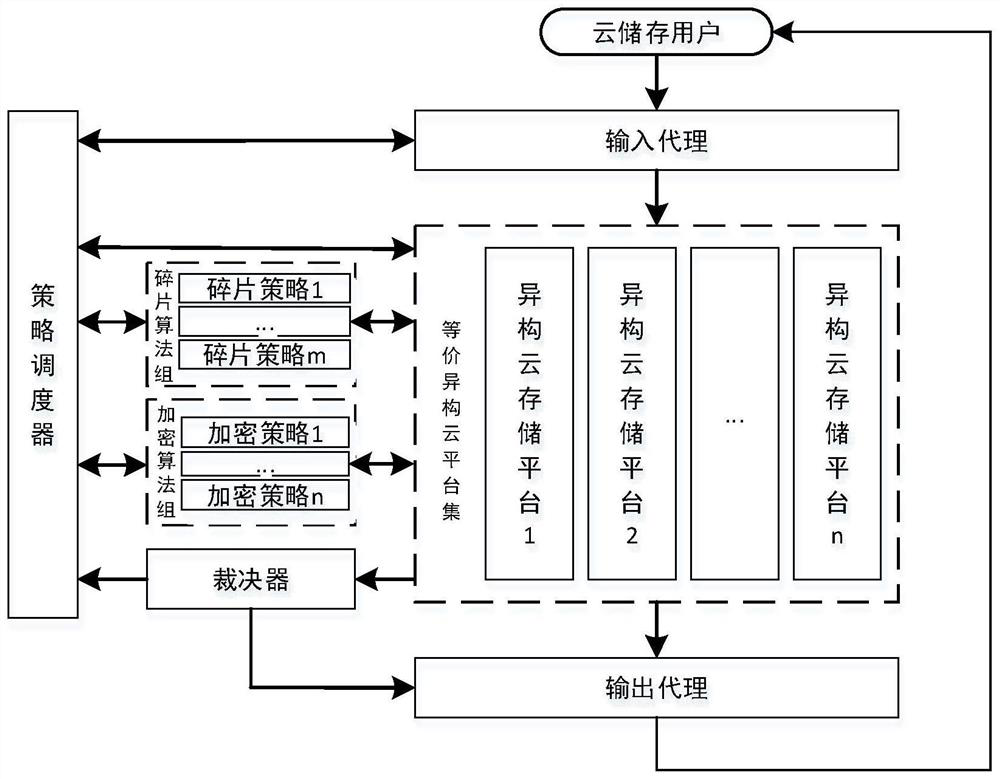
[0025] like figure 1 It is a flow chart of the data storage and encryption method for the mimic defense system of the present invention, and the method specifically includes the following steps:
[0026] (1) When the user performs a file write operation, the following sub-steps are included:
[0027] (1.1) The user sets the storage attributes of the data files to be uploaded, including file security level requirements and throughput requirements, and selects the data files to be uploaded. The input proxy module receives the storage attributes uploaded by the user and the data files to be uploaded, and sets the user settings The storage attributes and user information of the predetermin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com