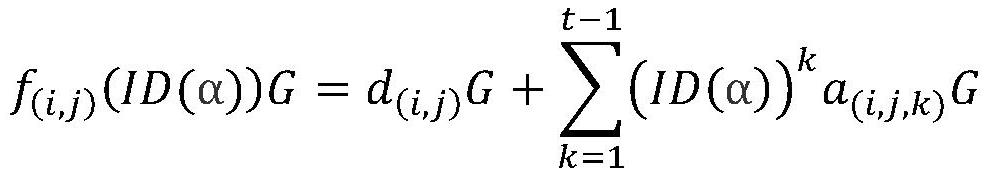A double threshold signature method based on ecdsa
A double-door and multiplication technology, applied in the field of electronic information security, can solve the problems of reducing the security of the scheme and not being able to obtain rights and interests, and achieve the effects of eliminating single-point failure, improving security, and strong versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0102] The present invention will be described in detail below according to the accompanying drawings and preferred embodiments, and the objects and effects of the present invention will become more apparent. It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention.
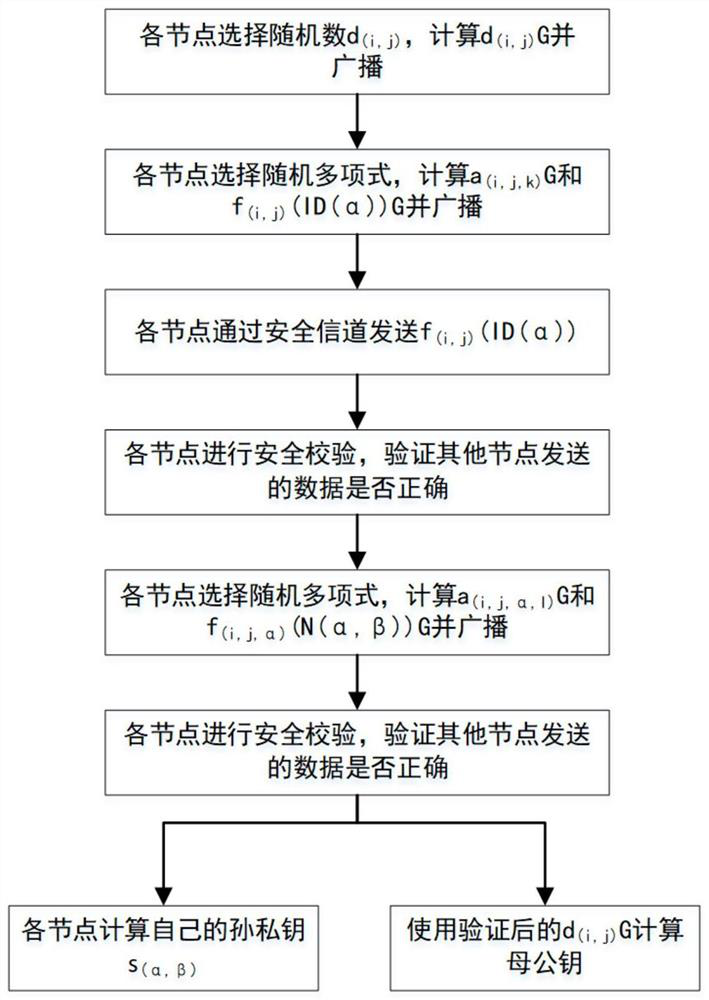
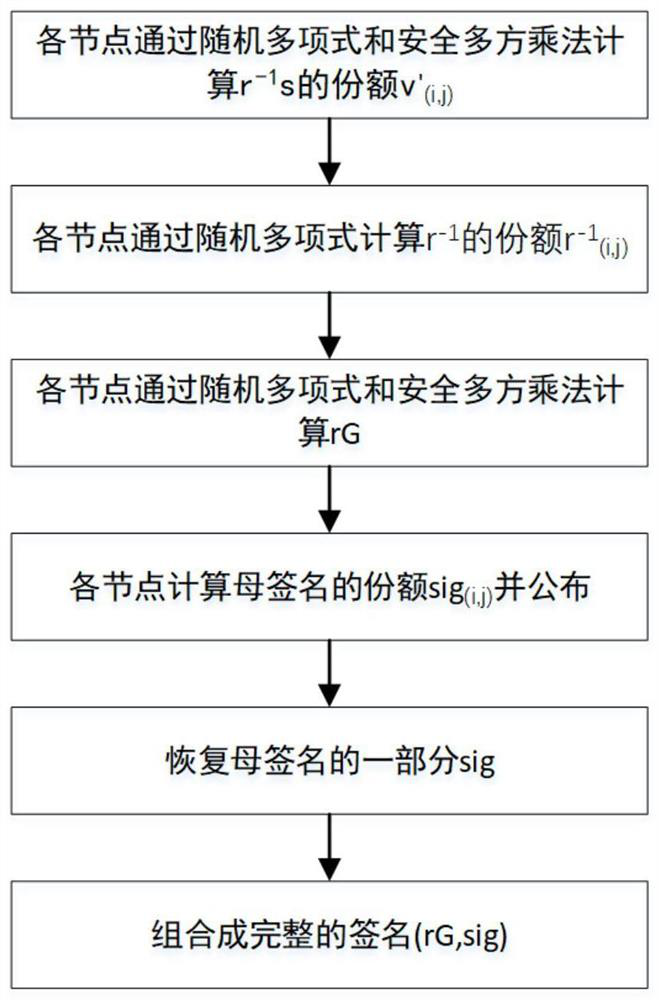
[0103] The ECDSA-based dual threshold signature method of the present invention is mainly composed of two parts: generating the parent public key and grandchild private key and synthesizing the signature. The first part corresponds to the initialization of the system, and the second part corresponds to the use of the system.
[0104] 1. Generate the parent public key and the grandchild private key (such as figure 1 shown)
[0105] In this process, (i, j) is used to represent a node, i represents the large group where the node is located, and j represents the serial number of the node in the large group, (α, β) is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com