Method for creating safe closed-loop process based on MITRE ATT&CK
A closed-loop and safe technology, applied in computer security devices, instruments, computing, etc., can solve problems such as low analysis efficiency, inability to share work with others, accuracy errors, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
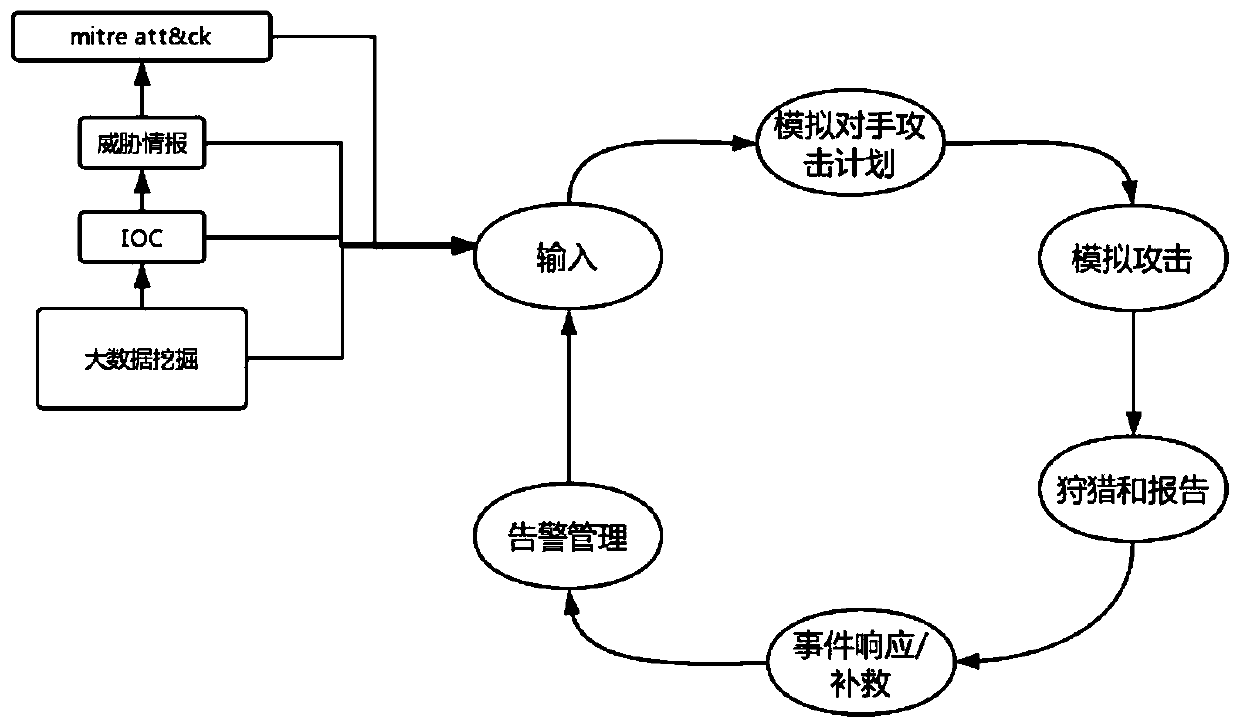
[0030] Embodiment 1, a method for creating a secure closed-loop process based on MITER ATT&CK, such as figure 1 shown, including the following steps:
[0031] 1), the first stage:
[0032] When creating an effective search, alert, and response improvement cycle that starts with input, the traditional data-informed cycle allows for more effective decision-making on alert and defense. The input content includes big data mining to obtain data, according to indicator IOC, threat intelligence, big data mining, etc.
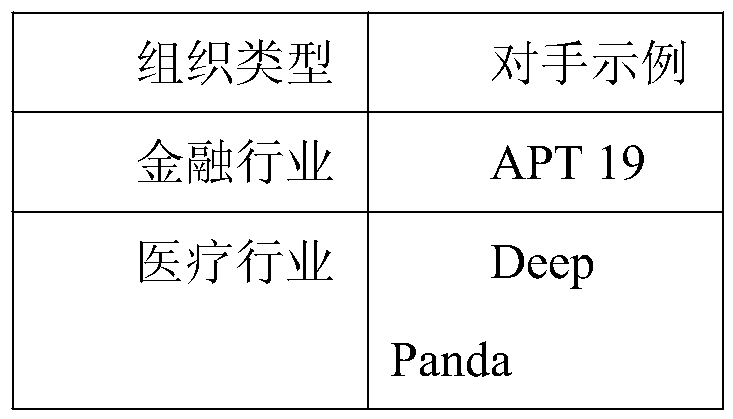
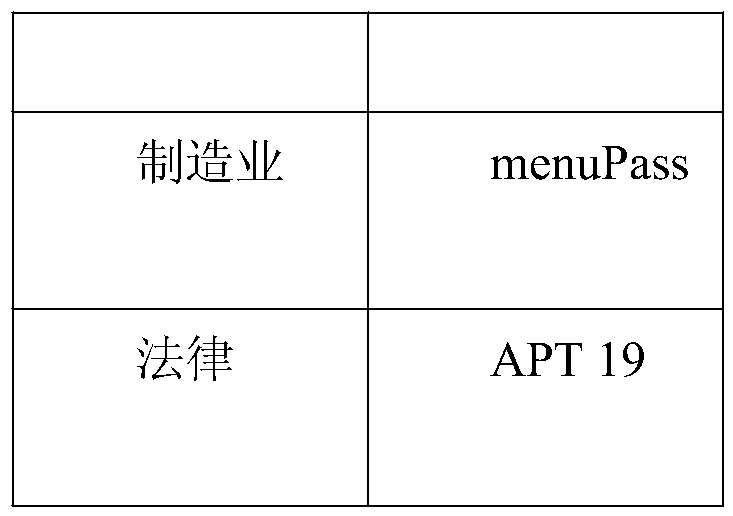
[0033] ATT&CK is a tactic to obtain a portrait of a specific industry or a specific organization from the attack characteristics in threat intelligence.
[0034] Threat Intelligence:
[0035] External threat intelligence is useful for two key reasons: new attack TTPs and attack verification and identification. Threat intelligence can be used to create one-off attack simulations, based on recent attacks such as the campaign carried out by APT39, or even more certain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com