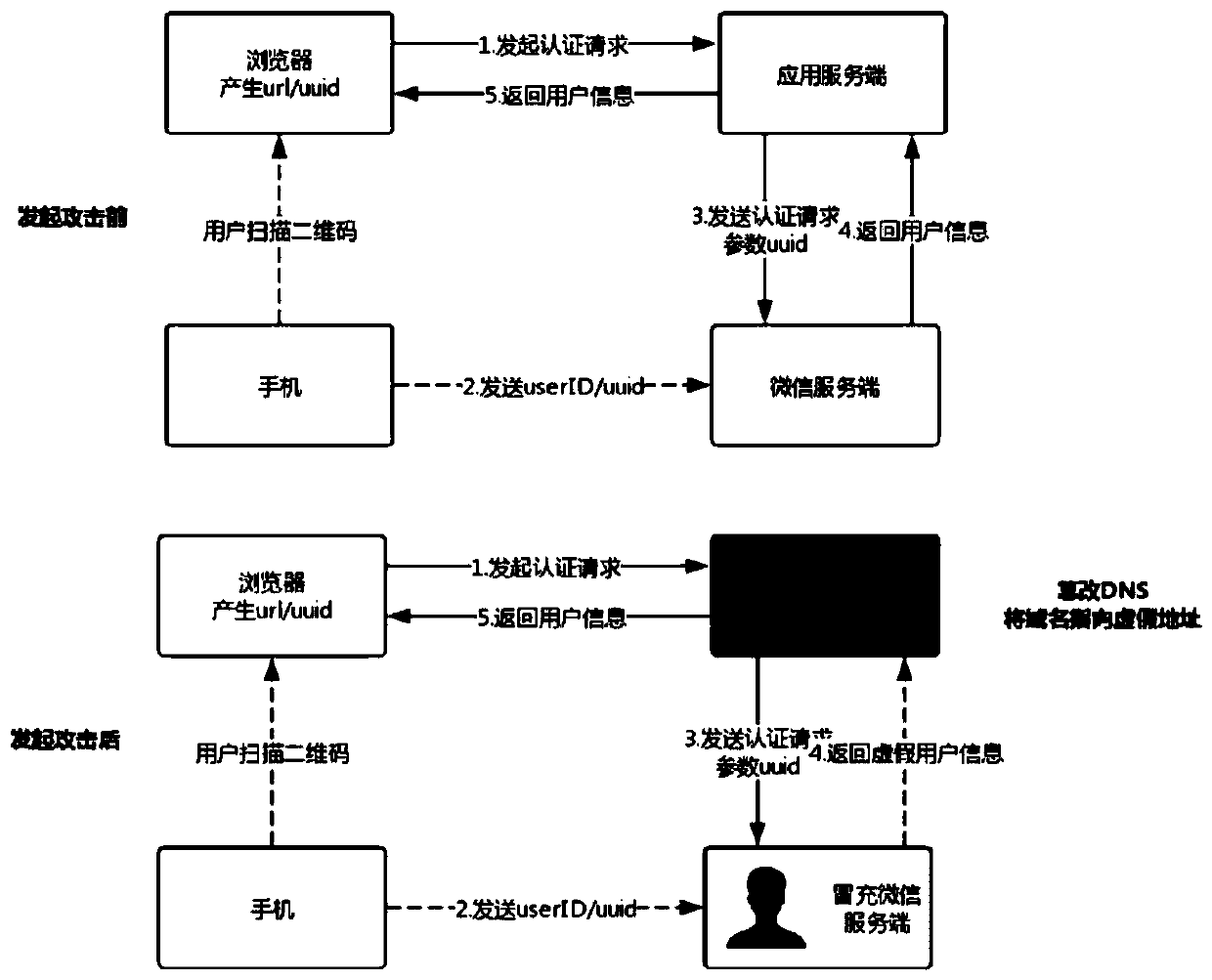
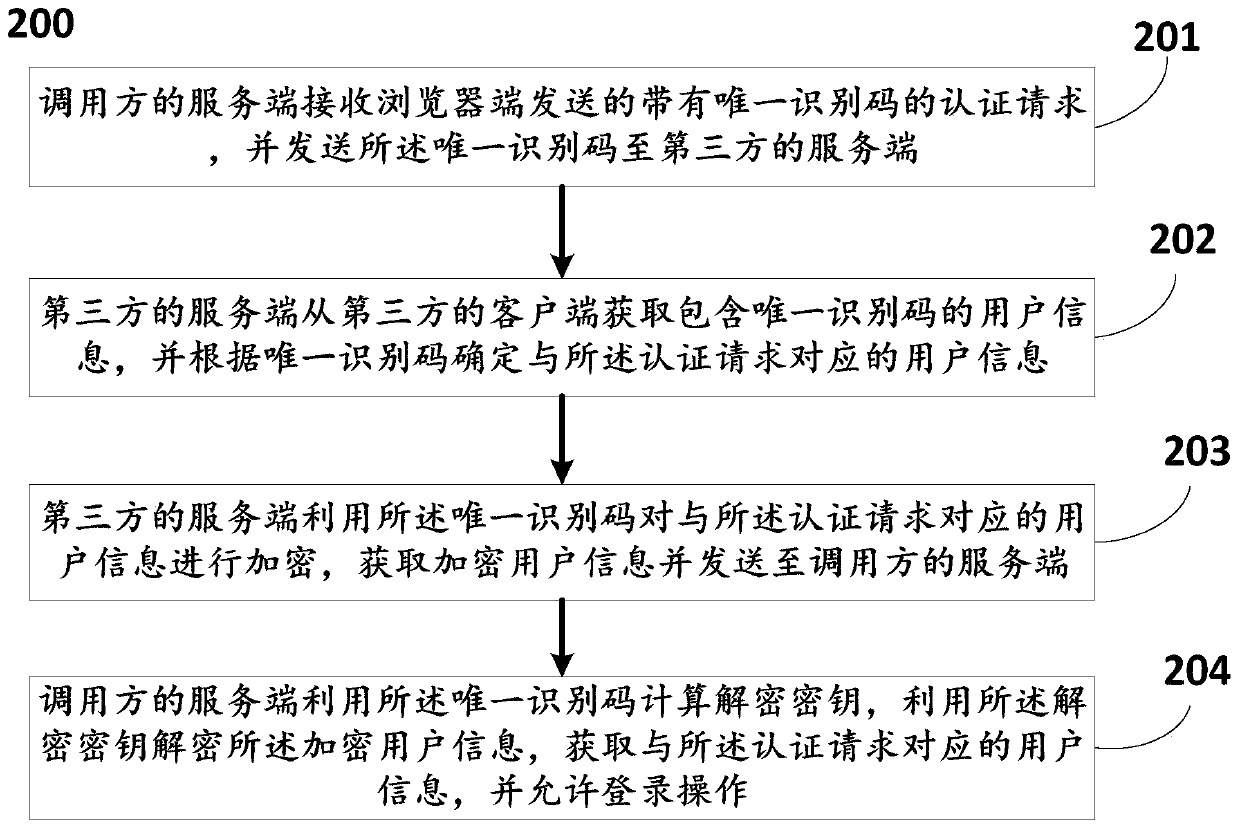
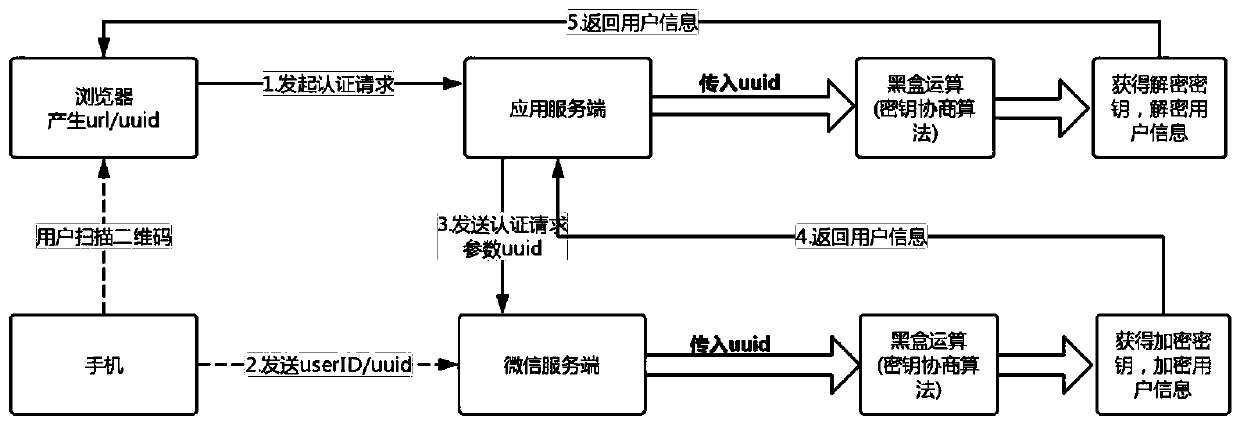
Secure login method and system based on third-party authorization
A secure login, unique technology, applied in the field of information security to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] Exemplary embodiments of the present invention will now be described with reference to the accompanying drawings. However, the present invention can be implemented in many different forms and is not limited to the embodiments described herein. These embodiments are provided to disclose the present invention in detail and completely. Invention and fully convey the scope of the present invention to those skilled in the art. The terms in the exemplary embodiments shown in the drawings do not limit the present invention. In the drawings, the same units / elements use the same reference signs.
[0043] Unless otherwise specified, the terms (including scientific and technological terms) used herein have the usual meanings to those skilled in the art. In addition, it is understandable that the terms defined in commonly used dictionaries should be understood as having consistent meanings in the context of their related fields, and should not be understood as idealized or overly for...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap