Maintenance behavior intelligent monitoring method and device and computer readable storage medium
A technology of intelligent monitoring and behavior, applied in the computer field
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0065] In this embodiment, the terminal devices are communicatively connected to each other to form a core network.
[0066] The application scenario of this embodiment is that the reserved interface of the core network is an unmanaged switch interface and all terminal devices in the core network are in the same subnet.
[0067] Alternatively, the reserved interface of the core network is a managed switch interface, and the reserved interface of the core network is in the same Virtual Local Area Network (Virtual Local Area Network) as all terminal devices in the core network.
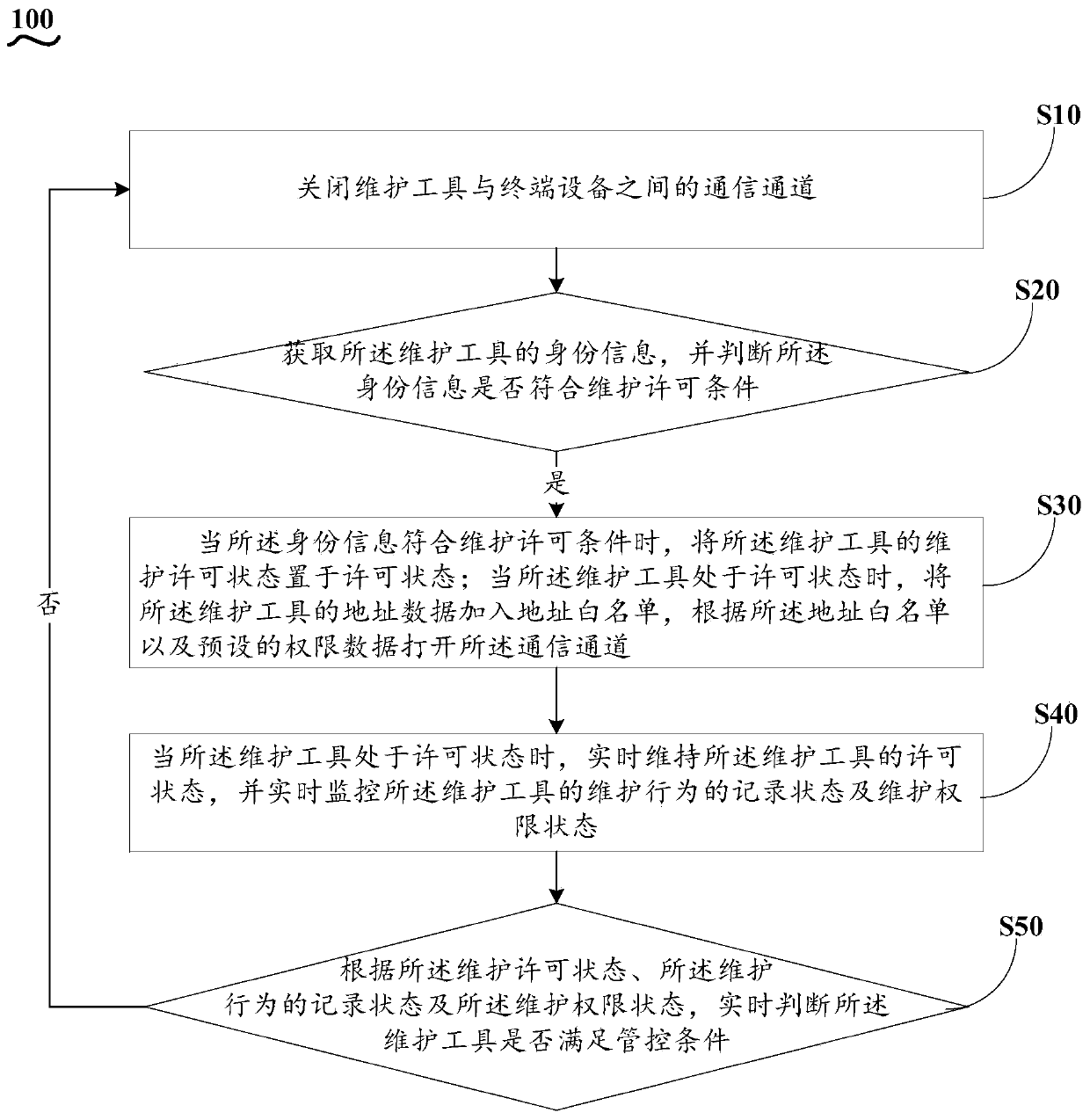
[0068] see figure 1 , the intelligent monitoring method of maintenance behavior includes:
[0069] S10. Close the communication channel between the maintenance tool and the terminal device, so as to prohibit the maintenance tool from performing maintenance on the terminal device;
[0070] Specifically, the data exchange module is powered on; in a default state, the data exchange function between the i...
no. 2 example
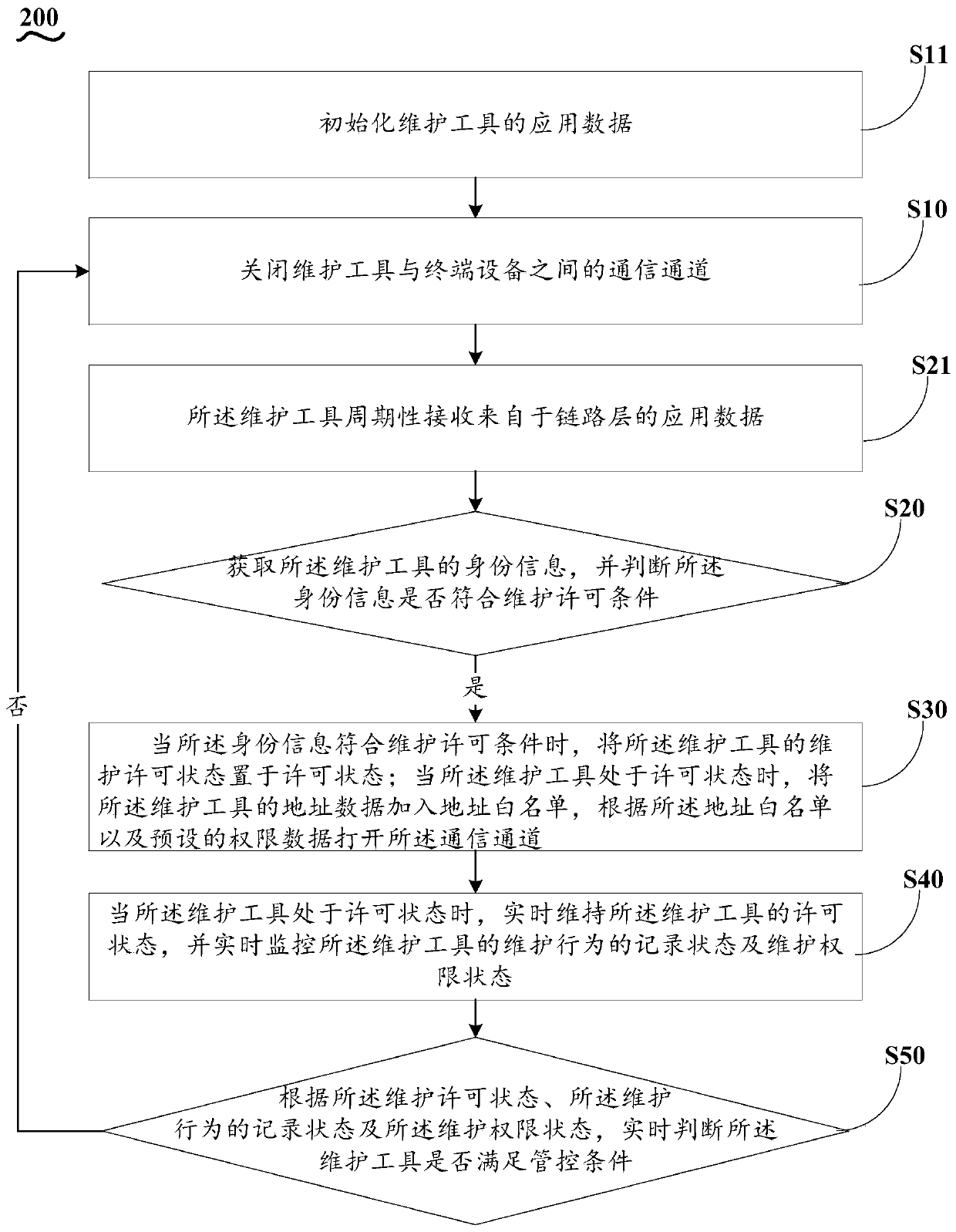
[0147] Based on the intelligent monitoring method 100 for maintenance behavior provided by the first embodiment of the present invention, the second embodiment of the present invention proposes another intelligent monitoring method 200 for maintenance behavior, the steps S10-S50 of which are the same as those in the first embodiment The examples are the same and will not be repeated here, the difference is that:
[0148] Before the step S10, the method 200 also includes:
[0149] S11. Initialize the application data of the maintenance tool, so as to provide the maintenance tool with a stable network address;
[0150] Specifically, turn off the data exchange function;
[0151] Obtain the subnet mask data, authentication service IP address, and authentication service port number from the local storage medium;
[0152] Judging whether the IP address and the subnet mask of the network adapter performing the authentication service are the same as the authentication service IP add...
no. 3 example
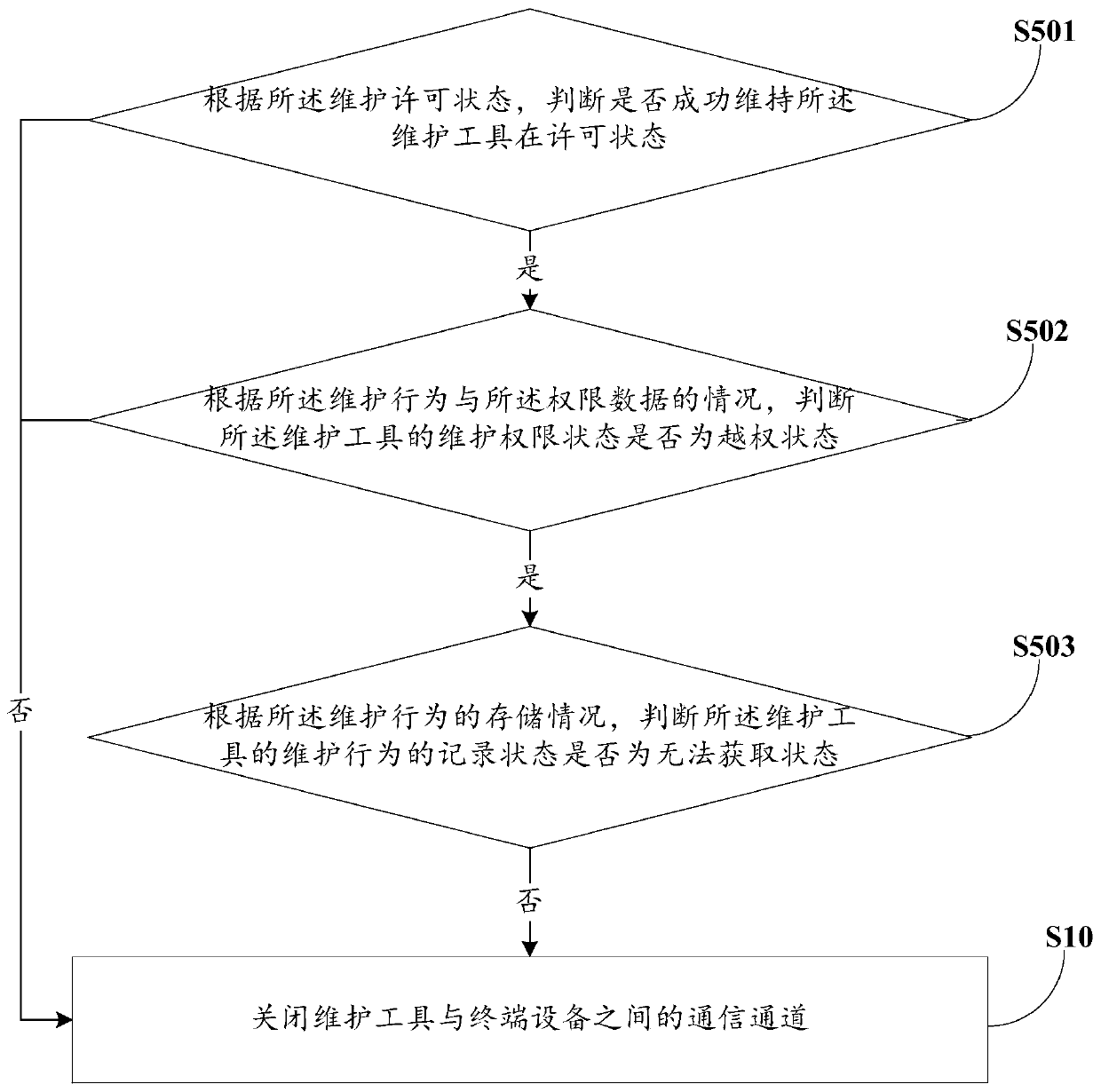
[0168] Based on the intelligent monitoring method 100 for maintenance behavior provided by the first embodiment of the present invention, the third embodiment of the present invention proposes another intelligent monitoring method 300 for maintenance behavior, the steps S10-S50 of which are the same as those in the first embodiment The examples are the same and will not be repeated here, the difference is that:
[0169] Between the step S10 and the step S20, the method 300 further includes:
[0170] S22. Obtain the application initialization data of the maintenance tool through the connection layer.
[0171] Specifically, detecting and judging whether the maintenance tool exists, if the interface connected to the maintenance tool is converted from a power-off unavailable state to a power-on available state, the maintenance tool exists;
[0172] Obtain the link layer LLDP message sent by the maintenance tool;
[0173] Extract the Optional TLV whose TLV type is 127;
[0174] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com