Method and system for quickly obtaining temporary password
A temporary password and fast technology, applied in transmission systems, digital transmission systems, collaborative devices, etc., can solve problems such as hidden security risks, inability to obtain temporary passwords, users do not know the time of the device, etc., to achieve the effect of high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
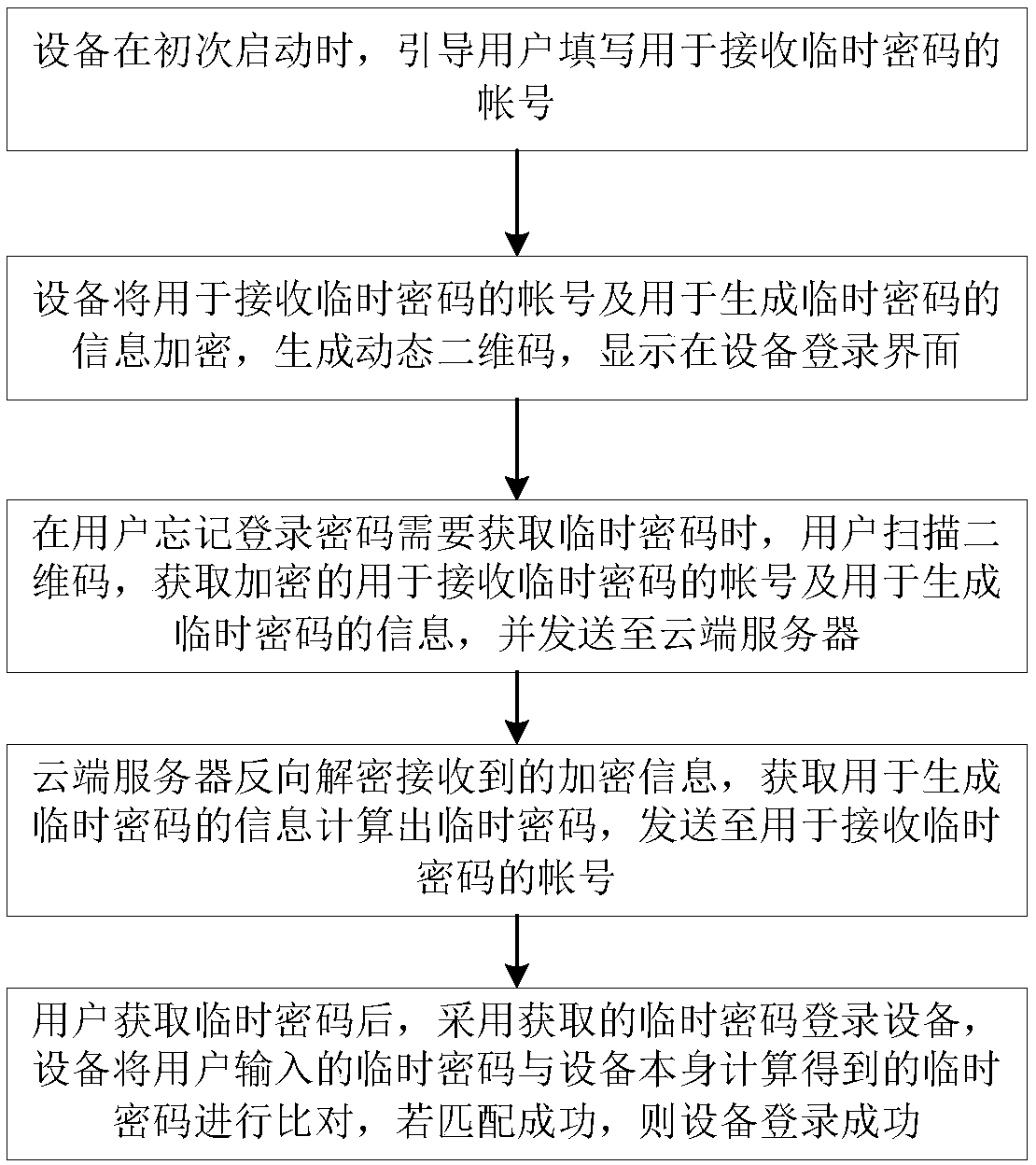
[0030] The technical solution of the present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments, and the following embodiments do not constitute a limitation of the present invention.
[0031] In this embodiment, a method for quickly obtaining a temporary password, such as figure 1 shown, including:
[0032] Step S1. When the device starts up for the first time, guide the user to fill in the account number for receiving the temporary password.
[0033] In the technical fields such as the Internet, communications, video surveillance, and the Internet of Things, there are a large number of networking devices. For example, in a video surveillance system, there are network cameras IPC, network hard disk video recorders NVR, etc. These devices generally have a login password for users to log in to the device and configure the device. In this embodiment, a monitoring device in a video monitoring system is taken as an e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com