Vulnerability mining model construction method based on swarm intelligence
A technology of vulnerability mining and swarm intelligence, which is applied in the directions of instrument and platform integrity maintenance, electrical digital data processing, etc., can solve the problems of late start in the research of vulnerability mining and analysis technology, achieve fast and efficient search and solution capabilities, and reduce the cost of vulnerability mining , the effect of high concurrency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] Among the present invention, the key technical problems to be solved are as follows:
[0023] (1) Vulnerability mining description method based on swarm intelligence
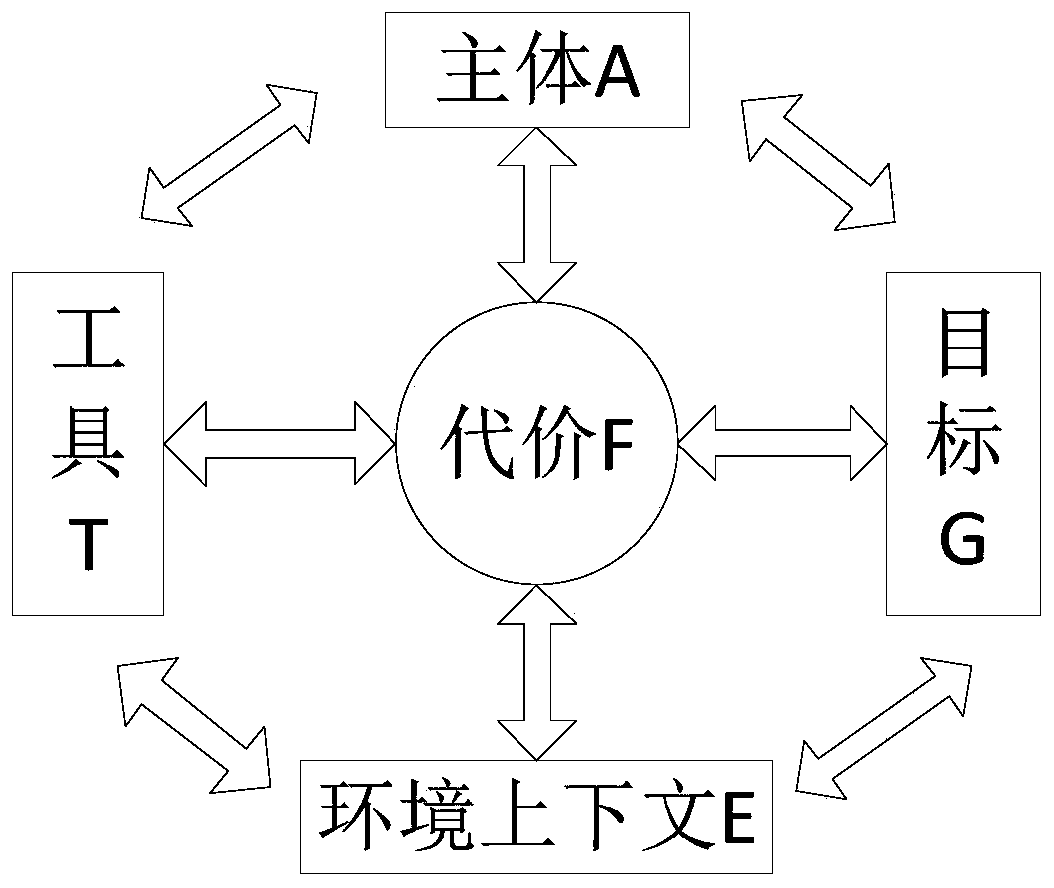
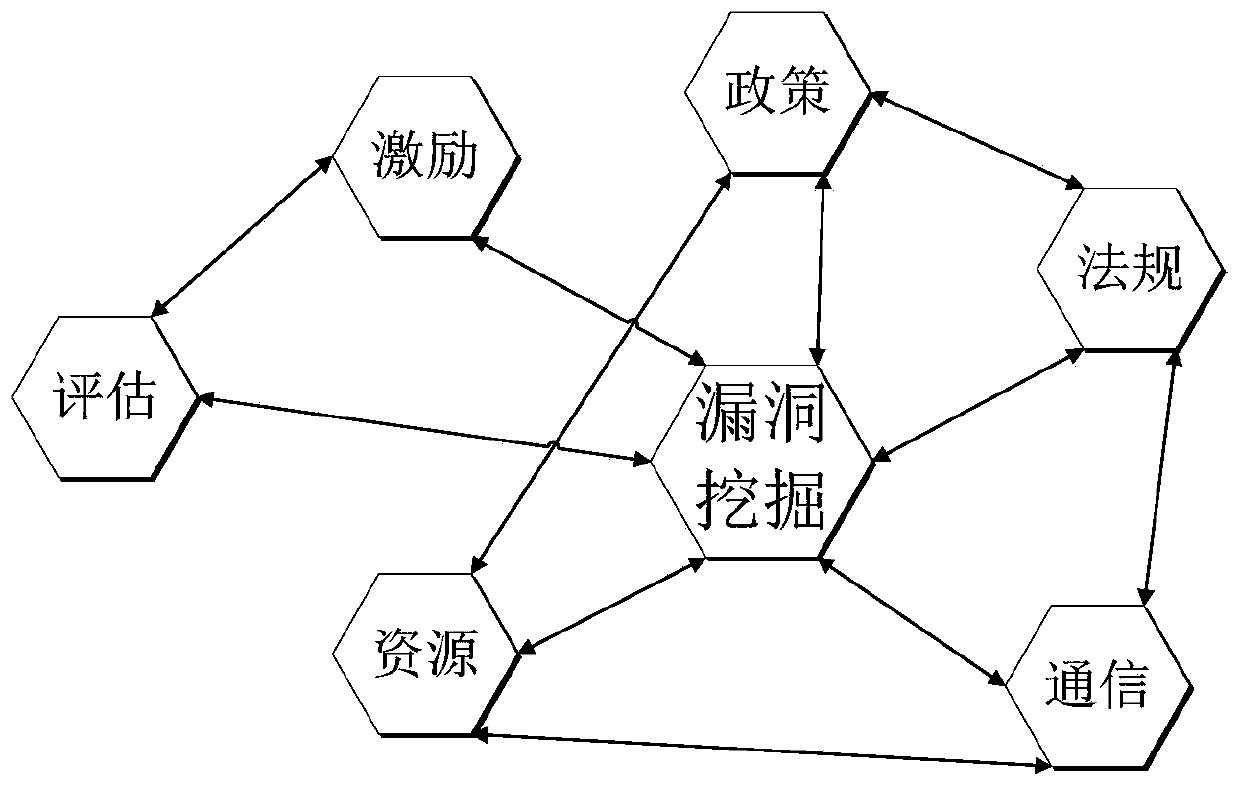
[0024] The core of swarm intelligence lies in the effective management and collaborative utilization of swarm intelligence resources in an open network environment to maximize swarm intelligence. The correct theoretical method is the basis for technological breakthroughs and application innovations. The swarm intelligence project for vulnerability mining is related to four factors, namely, the main body (human-machine) participating in vulnerability mining, the tools used for mining, the goals and tasks to be achieved by mining, and Dig into your physical and cyber environment. The main problem to be solved by the present invention is to generalize highly random and complex characteristics of cyberspace vulnerability mining subjects, tools, targets, and environments into a formalized process semantic cal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com