Real-time log clustering analysis method based on reverse table
A cluster analysis and log technology, applied in the computer field, can solve problems such as the inability to meet the requirements of enterprises, and achieve the effect of improving versatility and speed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
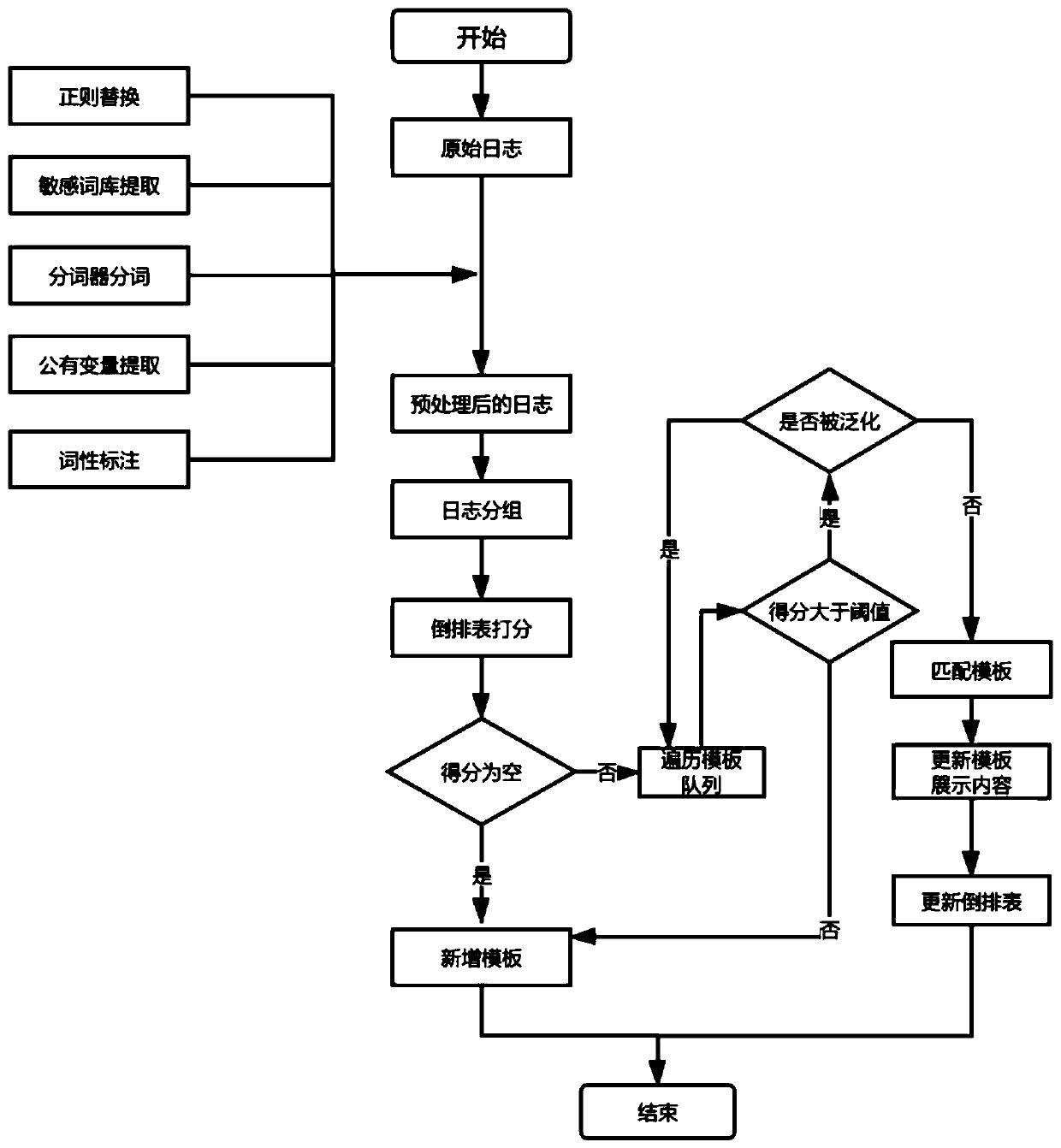
[0033] Embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings, as figure 1 As shown, the implementation steps are as follows:
[0034] Step 1: Initialization: Define the encapsulation structure of each word in the log, including four types of encapsulation structures: normal, regex, important and verb;
[0035] Step 2: Raw log preprocessing:
[0036] The first step is regularized replacement; use regular expressions to replace the IP address, port number, and time in the original log with strings such as $IP, $IPPort, and DateTime, and perform simple encapsulation;
[0037] In the second step, the sensitive word library is proposed; according to the semantic analysis and the set sensitive word pattern, the sensitive words in the original log are processed, and their type is set as important;
[0038] The third step is the word segmentation of the word breaker; in order to perform accurate word segmentation on the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com