Signature algorithm for preventing large-batch data from being tampered in Internet of Vehicles
A data signature and mass-volume technology, applied in digital transmission systems, encryption devices with shift registers/memory, user identity/authority verification, etc., can solve problems such as time-consuming and inability to complete records, and achieve high computing efficiency, Strong security and excellent computing speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The present invention will be further explained below in conjunction with the accompanying drawings and specific embodiments. It should be understood that the following specific embodiments are only used to illustrate the present invention and are not intended to limit the scope of the present invention.
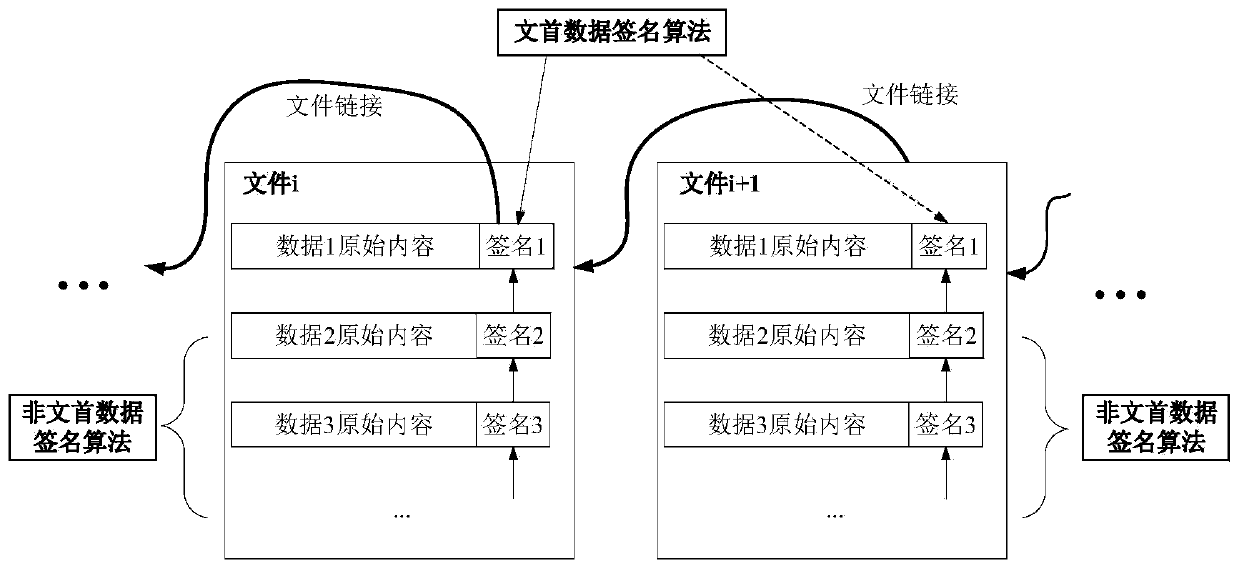
[0028] A tamper-proof signature algorithm for large amounts of data in the Internet of Vehicles, its overall structure is as follows: figure 1 As shown, for each piece of original data, its corresponding signature will be calculated and saved together. The data storage file is based on the time when the data was generated.
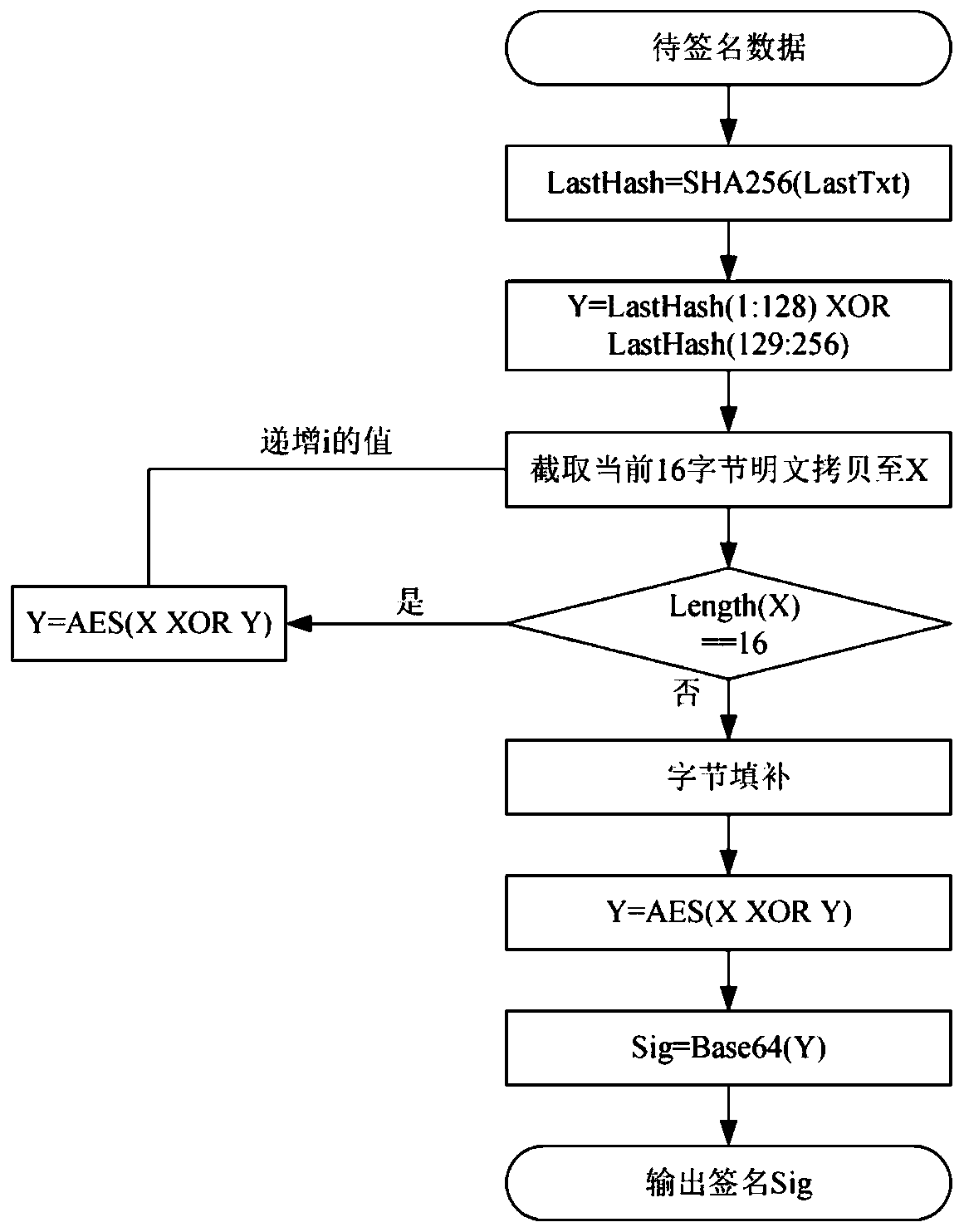
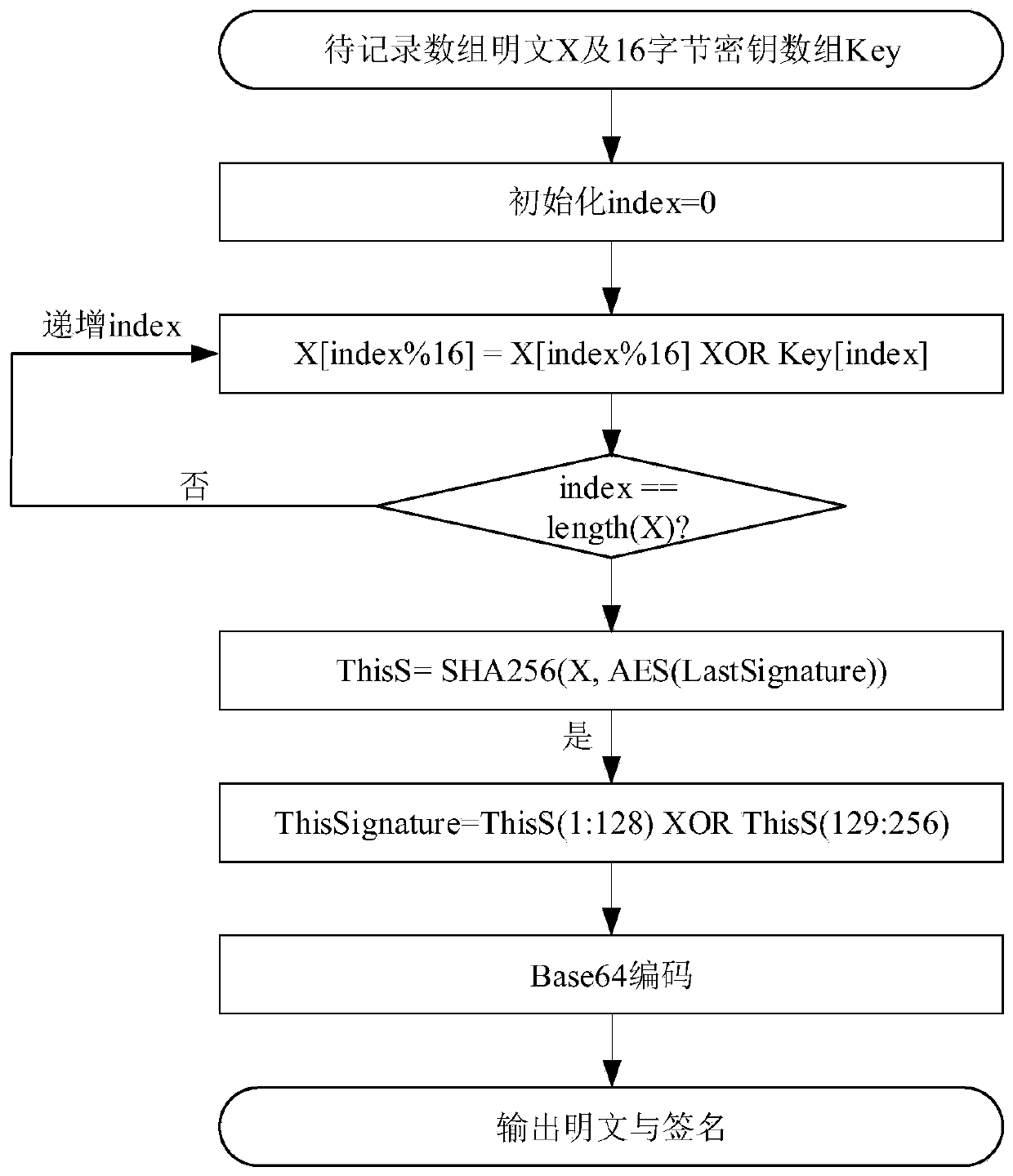
[0029] For each piece of original data, its corresponding signature will be calculated and saved together. The data storage file is based on the time when the data was generated. The first data signature algorithm in each file adopts figure 2 The signature algorithm of the header data shown in the document is used to complete the connection betw...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com