Violent invasion detection system and method based on expression recognition
An expression recognition and detection system technology, applied in character and pattern recognition, acquisition/recognition of facial features, instruments, etc., can solve the problems of high maintenance cost of manpower and material resources, dead angle detection of detection equipment, inconvenient detection, etc., to save labor costs , low cost and cheap hardware
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
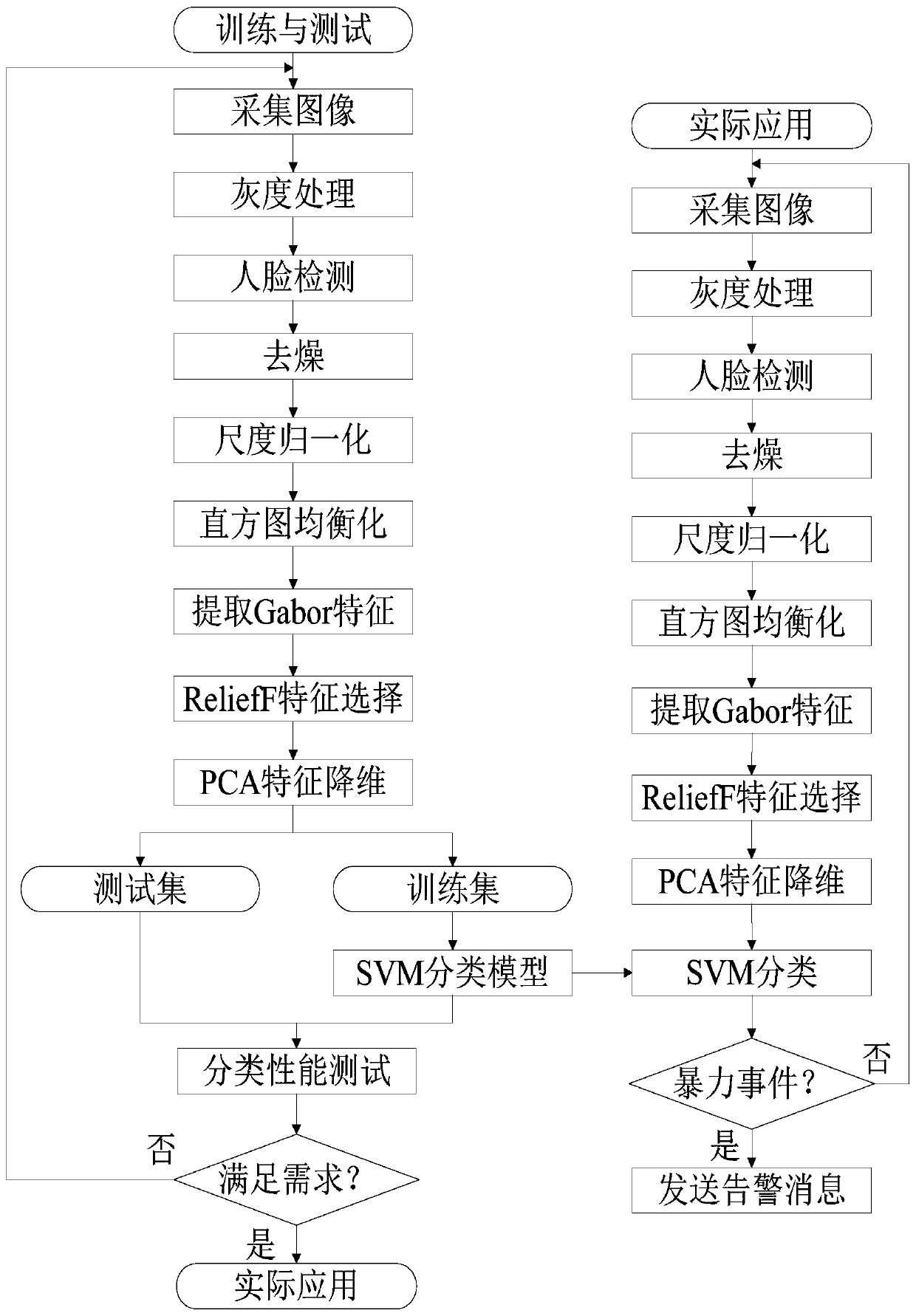
[0026] Specific Embodiment 1: In this embodiment, a violent infringement detection system based on facial expression recognition includes a hat body;
[0027] The hat main body is provided with a microprocessor module, an image acquisition module, a positioning module and a wireless communication module;
[0028] The image collection module is used to collect the facial image data of the person facing the user and transmit it to the microprocessor;
[0029] The positioning module is used to collect the location information of the user;
[0030] The microprocessor module is used to determine whether the user is in a state of being violently violated according to the facial image data of the person;
[0031] The wireless communication module is used for transmitting the judgment result and position information of the microprocessor module.
specific Embodiment approach 2
[0032] Specific embodiment 2: The difference between this embodiment and specific embodiment 1 is that when the microprocessor module judges that the user is in a state of being violently violated, the microprocessor module controls the wireless communication module to send an alarm message to the designated recipient, which contains Location information of the person wearing the hat;
[0033] When the microprocessor module judges that the user is not in the state of being violated by violence, the microprocessor module controls the wireless communication module not to communicate (do not send an alarm message to the designated receiver).
[0034] Other steps and parameters are the same as those in Embodiment 1.
specific Embodiment approach 3
[0035] Specific embodiment three: the difference between this embodiment and specific embodiment one or two is that the image acquisition module is a camera.
[0036] Other steps and parameters are the same as those in Embodiment 1 or Embodiment 2.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com