Blockchain-based access control method for electronic medical records
An electronic medical record and access control technology, applied in electronic digital data processing, instruments, computing, etc., can solve the problem that it is difficult to ensure that patients can accurately remember the quantitative value of historical symptoms, affect doctors' understanding of patients' historical symptoms, and contain non-professional medical terms, etc. problems, to support medical research and precision medicine, eliminate data silos, and prevent tampering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
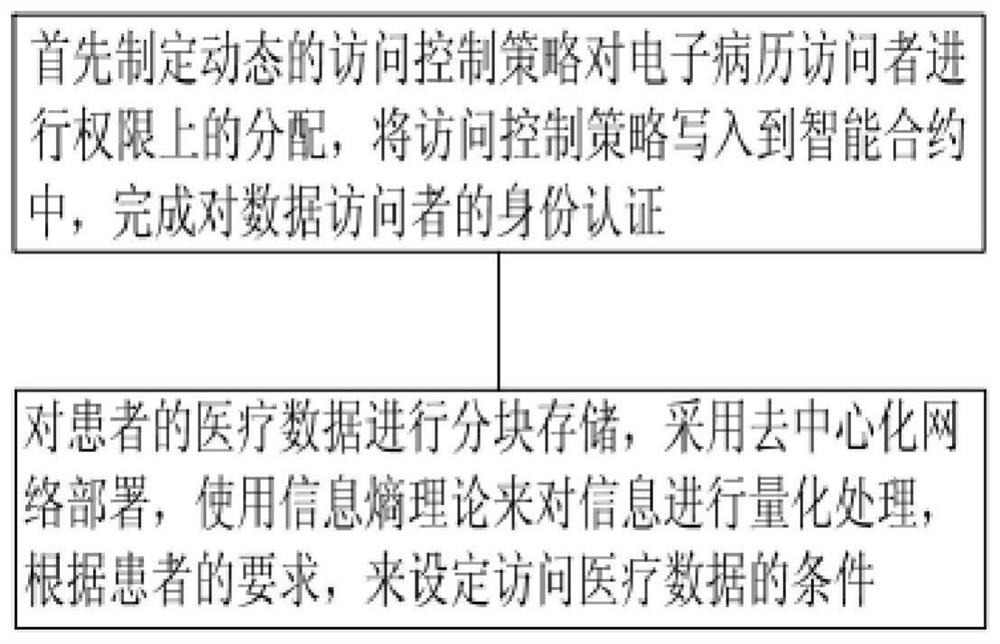
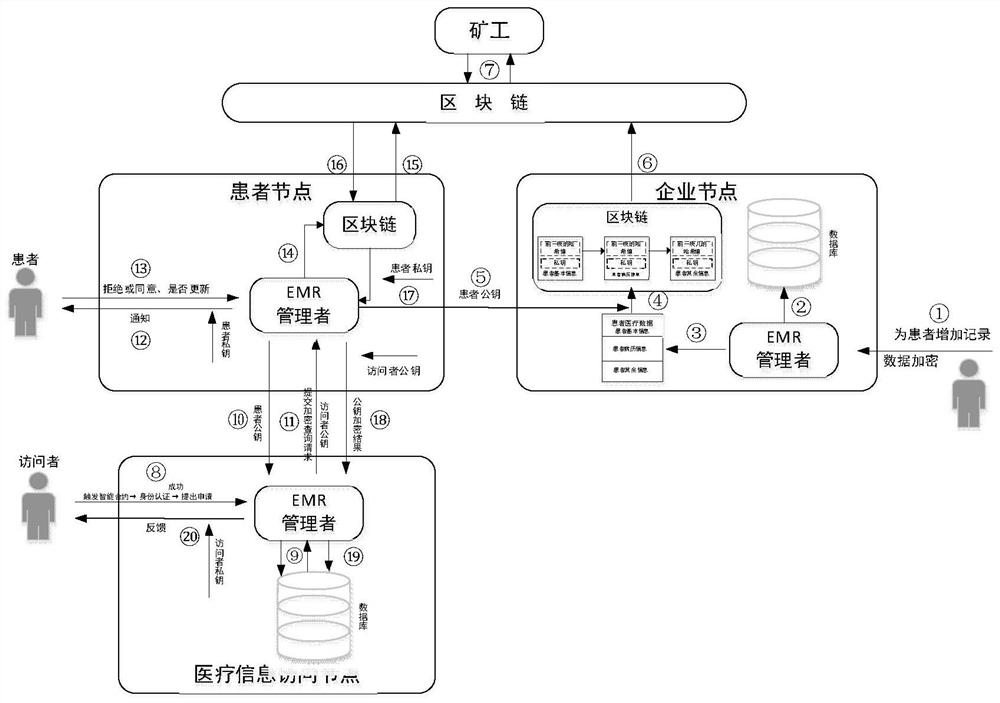
[0106] Example 1: Cary, a dermatologist, proposes to access the inspection data of patient Bob's bronchitis (respiratory medicine) for the purpose of treatment. First of all, Cary needs to perform identity authentication. For the established access control strategy, doctor Cary's identity authentication cannot pass, and he does not have the corresponding authority to view the medical data of patients who are not in the department. In this way, the user's identity and authority are restricted through access control to achieve the purpose of data protection.
example 2
[0107] Example 2: Cardiovascular physician Mark proposes to access the medical data of patient Mary's cardiovascular disease. The purpose of the visit is for disease research, and the intended purpose of the medical data of patient Mary's cardiovascular disease is treatment. Doctor Mark has passed the corresponding identity authentication, and his visit purpose is inconsistent with the intended purpose, so there is no need to calculate the information entropy Es of this visit request. This visit request is rejected and the medical data cannot be viewed. In this way, the risk of accessing data is reduced, and the patient's request is given priority; if doctor Mark believes that this disease research is effective in preventing disease and is beneficial to the patient's health, doctor Mark can apply again, specifying the purpose of the visit , and calculate Es and compare it with Et, and send the result together with the public key to the EMR administrator. After receiving the req...
example 3
[0108] Example 3: The clinician Jack proposes to visit the patient Tom's gastrointestinal health for further treatment. First of all, the role of doctor Jack is the clinical attending doctor, who has passed the corresponding identity authentication, and the purpose of the visit is consistent with the intended purpose, and compares Es and Et. If Es
[0109] Security Analysis:
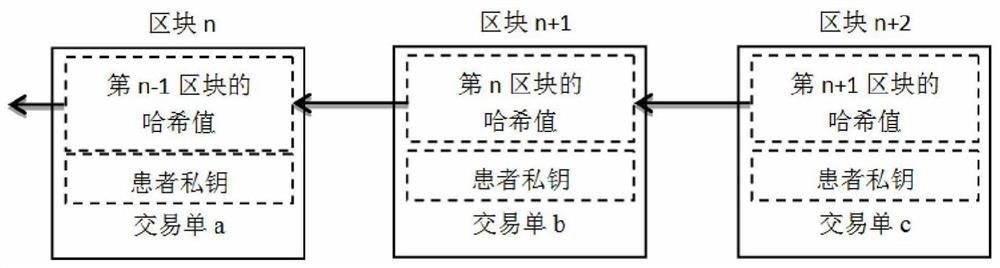
[0110] 1) File storage security: The c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com